Product: Sophos Central Adv Email Gateway
GOAL: Not reduce security
PROBLEM: Company A acquires Company B and sets up email forwarding for newly acquired users in its own (Company A) tenant.
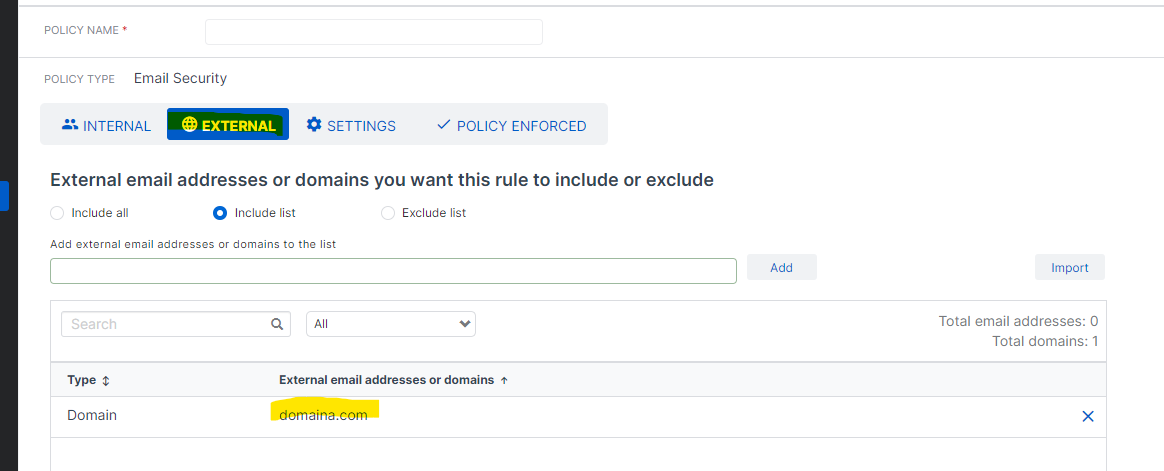
DETAILS: Company B retains its Sophos Email Gateway and Microsoft Hosted Exchange tenant. Company A creates domainA.com
accounts for Company B users in its own tenant. Company A sets up email forwarding to for those users so that emails sent to userB@domainA.com forward to userB@domainB.com. The problem we are seeing is that the forwarded emails are clearly being interpreted as spoofed emails because the from address is domainB.com.
BEHAVIOR: Emails go to quarantine.
WHAT WE HAVE TRIED: modified the SPF record to include the remote sending host. Anyone not on the VIP list will receive the email. VIP users' email will go to the quarantine this time based on VIP impersonation. Whitelisting the email host (approved domain) does not help.
WHAT WE ARE WONDERING: Does the email gateway have a control to bypass the quarantine if there is specific information in the header....such as the domain name domainA.com??
This thread was automatically locked due to age.