We have reported several issues to the Sophos support but basicly it hasn't been fixed.
The problem is related to impersonating your domain email adresses with malicious urls.
- Base email Security
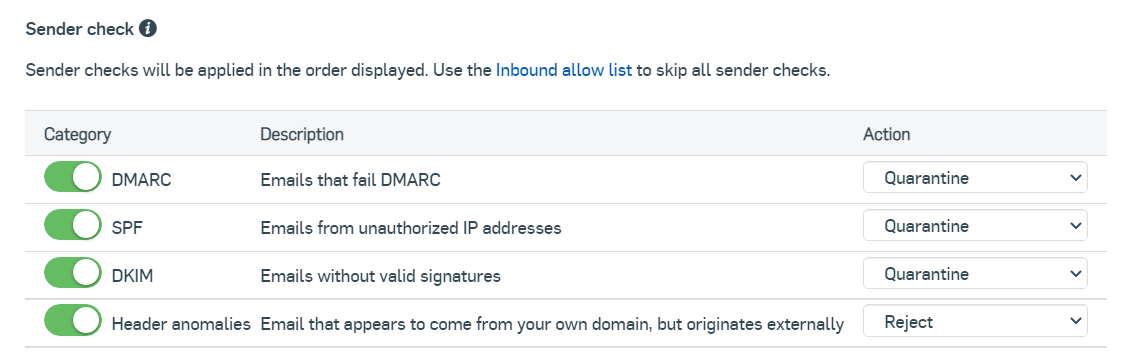
DMARC and SPF are checked against the Helo email server. When that is using it's own spf and dmarc settings they will not fail as it is not checked against the from email adress, so your domain SPF and DMARC are never taken into account.
So basicly header anomolies is useless.
The response of support was to delete the Base Email Security policy and recreate it instead of fixing their check logic.
Now we found another one. When we block the email server helo name with an add block setting, this is not enforced as they use another from adress. Argh! I have now added their IP adress also and in some cases I had to add whole ranges. An add block IP range would be helpfull.
Frustrated.
Fred
Edited tags
[edited by: Raphael Alganes at 6:14 AM (GMT -7) on 7 Jun 2023]


