I see the new Mailflow functionality is appearing in my Cloud Portal as a released feature. In the help it states:
Sophos Mailflow doesn't currently support the following:
- Transport Layer Security (TLS)
- Remote block lists (RBL)
- Sophos Central Self Service Portal Emergency inbox. See Manage settings for Sophos Central Self Service.
- S/MIME (coming in Q1 2022)
What do you mean by it does not support TLS? What elements of the email transmission are not encrypted using TLS connections exactly?
After switching to the Mailflow method from the Gateway method do I also need to:
1. Remove the Bypass Exchange Online Protection in Microsoft 365 rule in O365 Mailflow Rules?
2. Remove the Secure Connector between Microsoft 365 and Sophos Gateway?
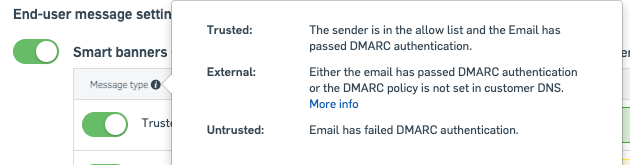
Will the new Mailflow method remove the Sophos Banners on my emails when I reply to them as part of the Outbound process?
Thanks,
Mark.
Edited tags
[edited by: Raphael Alganes at 6:04 AM (GMT -7) on 7 Jun 2023]