Disclaimer: This information is provided as-is for the benefit of the Community. Please contact Sophos Professional Services if you require assistance with your specific environment.
Here, we will take real Threat Graphs that are showing different types of malware detections. Using the information provided, we will investigate what additional actions could be taken to further improve your security. Please note that many real-world threat graphs will not necessarily provide options to improve your security. They can also just act as a record of what happened.
After clicking on the new threat graphs for an ML/PE-A detection we are presented with the simplified events chain. In this example, it shows the computer WIN7 had the route cause of the email client Outlook.exe and a beacon event on a file called 431.exe, this file was detected on November 14th and cleaned.
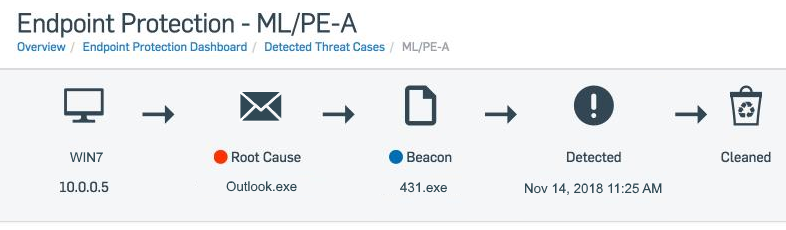
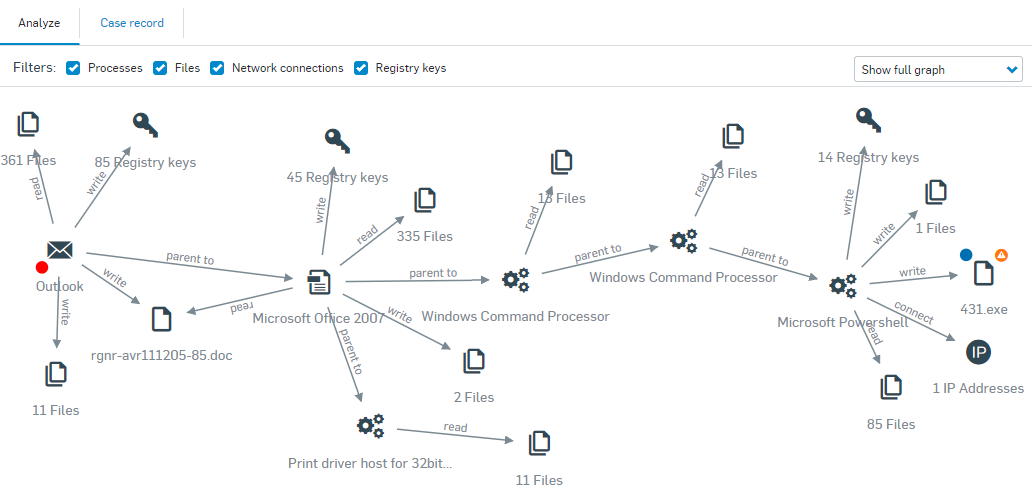
Looking at the analyze attack chain graph below, we can see several events linking the root cause - Outlook on the left hand side, to the beacon event - 431.exe on the right. We can also see that the beacon file also has an uncertain reputation.
Before we dig any deeper into this, let us get a better overview of what happened, we can select the Show direct path option from the drop down menu on the right-hand side.
This hides most of the events leaving only the ones that directly link the root cause to the beacon. It is now easy to see that Outlook wrote a word document called rgnr-avr111205-85.doc. We can also see that Outlook launched a Microsoft Office application, which read the doc file.
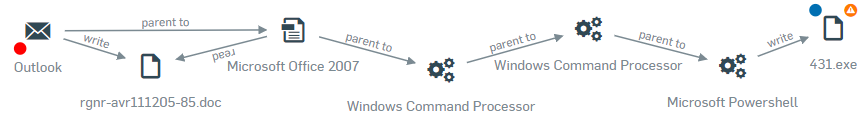
We can already see that the Microsoft Office event does not have a reputation icon, which means it has a good reputation.
Note: Reputation is only calculated for Portable Executable (PE) files, for example .exe, .dll. It is not shown for other file types such as .doc, .pdf, .png.
By selecting the Microsoft Office event, we can see that SophosLabs Threat Intelligence information is already available and confirms that it does have a good reputation. We can also see the path and name of the file indicate this is the Microsoft Word application.
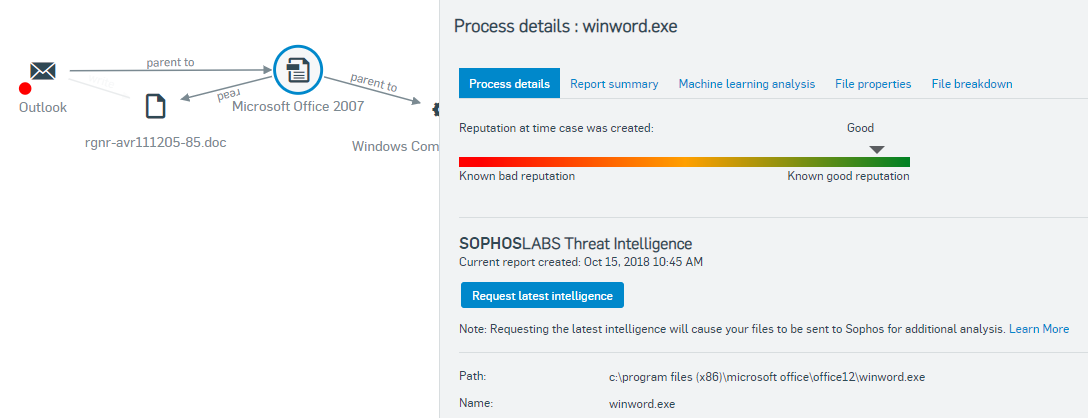
For customers using Sophos XDR, we can also see that on the File breakdown tab the file is signed by Microsoft. We could look at the other tabs to further verify the legitimacy of this file. However, it is clear this is the real Microsoft Word application.
This tells us the user most likely received an email with the word document attached and that they opened the attachment. Let us look at the next event.
We can see that Microsoft Office launches Windows Command Processes (CMD), again by selecting this event we can see it has a good reputation and we are happy this is the legitimate version of CMD.exe. What is suspicious though is the command line information it was launched with.
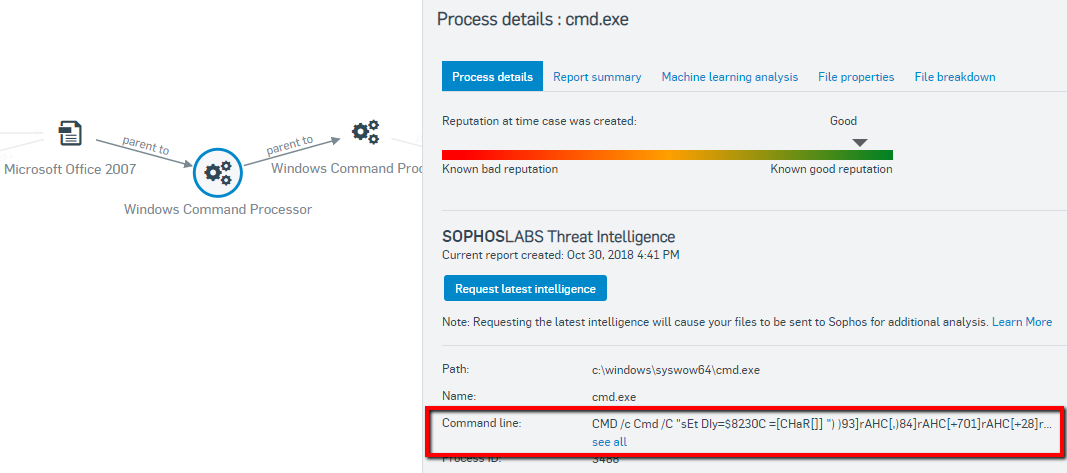
By selecting the see all link we can see the full command.
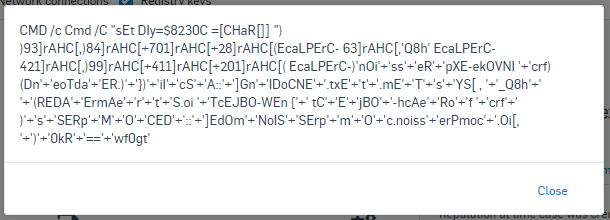
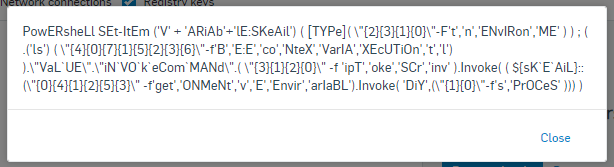
Looking at this code, you will most likely not have any idea what it is designed to do. However that is exactly the idea. This is a heavily obfuscated bit of code. Obfuscation is very typical in malicious code and is designed to hide the true goal behind the code as well as make it harder for security software to analyze. We may not know what it is doing but we are certain it is very suspicious.
We can also see that when CMD was launched it then launched another copy of CMD, this one with a similar suspicious command line.
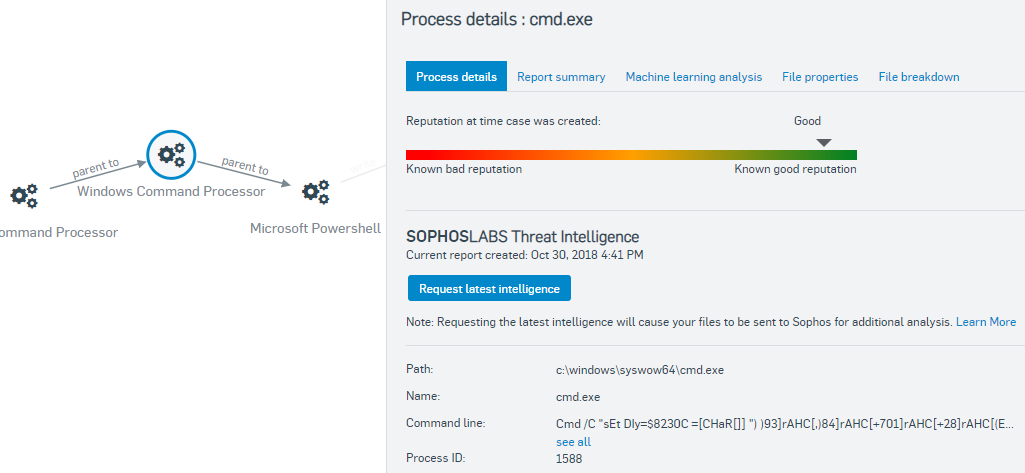
This second CMD is used to launch Microsoft Powershell.
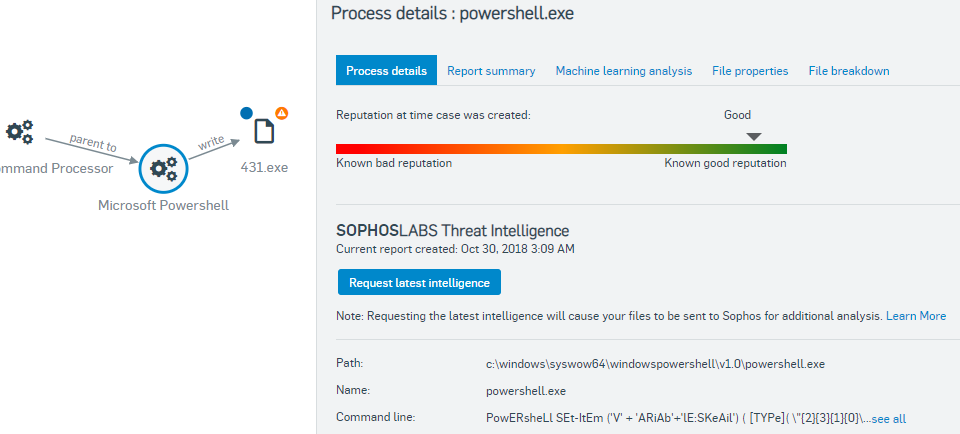
We can also see that Powershell has been launched with an obfuscated and very suspicious command line.
Powershell has then written the 431.exe file which was detected by Sophos Deep Learning as ML/PE-A.
By selecting the beacon event we can see confirmation that it has an uncertain reputation, as well as that it was written to the user's AppData location, this location is typically meant for data not executables so this is also suspicious.
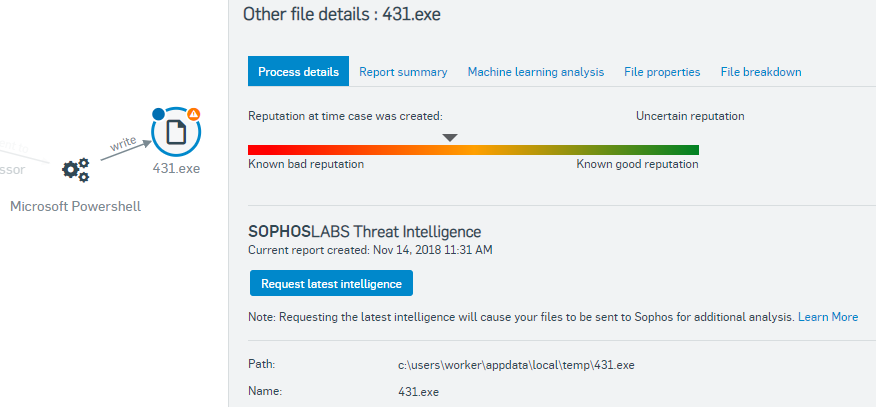
Important: Customers who are not using Sophos XDR, you will only see the one Process details tab.
For customers using Sophos EDR, by pressing the Request latest intelligence button, the file will be retrieved out of the Sophos quarantine and submitted to SophosLabs. A couple of minutes later the four other tabs (Report summary, Machine learning analysis, File properties, File breakdown) pictured will be displayed. The purpose of these additional tabs is to help display the various properties of the file in a simple way. This can be useful for various reasons, one of them is to feel confident that the file is indeed malicious and not something you want in your environment. For more information on SophosLabs Threat Intelligence, see: Sophos Central: Threat intelligence overview.
Now that we understand that the file was malicious and that it came from an email, which then used Microsoft Word, CMD and Powershell to execute the attack chain, we can decide what could be done to help prevent this type of attack happening again.
Firstly a spam email with a malicious attachment got into your network, which means it got past any email spam scanning software you have, as well as avoiding detection for the malicious word document. Regularly reviewing your email security policies to ensure you are following best practices and using the latest protection is recommended. If you are not already a customer we recommend the Sophos XG firewall to handle your email protection, combined with Sophos Sandstorm to add the protection of a sandbox environment to safely execute potential email threats before they enter your environment.
You also have a user that opened the suspicious word document on the spam email. With better user education this potentially could have been avoided. Sophos Phish Threat allows you to create realistic email phishing campaigns to send to your users. Tracking which users fall for the spam email and directing them to training material.
The next layer of protection you could look at is using Sophos Application Control, which is already included in all Sophos Central Endpoint and Server Advanced licenses, as well as Sophos Intercept X Advanced with EDR. With Application Control you could choose to block your users for running specific applications. While you are unlikely going to stop them from running Microsoft Word, do they really need to be able to run Powershell? This could be blocked with Application Control.
If you were concerned that the computer was still infected, or just wanted to be safe until you had spoken to the user. You could use the Isolate this computer option in the Suggested next steps section. This would disable all TCP and UDP traffic on the computer other than communication to Sophos. For more information on computer isolation please see: Sophos Central - Computer Isolation Overview
If you would like to look at other Threat Graphs examples, please see the links in the Related information section below. You can also use the community forum to post questions about any threat graphs you have and would like advice on.