Hi all,
i've got a false-positive outbreak detected on one fileserver.
There're around 100 Items in Quarantine - alerts spread over 6 pages in Events-Section in central.
i went through that list multiple times but was able to release 95 elements from quarantine only.
So now i have 5 items left. But: there's no overview which items are released and which are not.
Due to all detections having the same timestamp it seems like order i different everytime i switch from page to page.
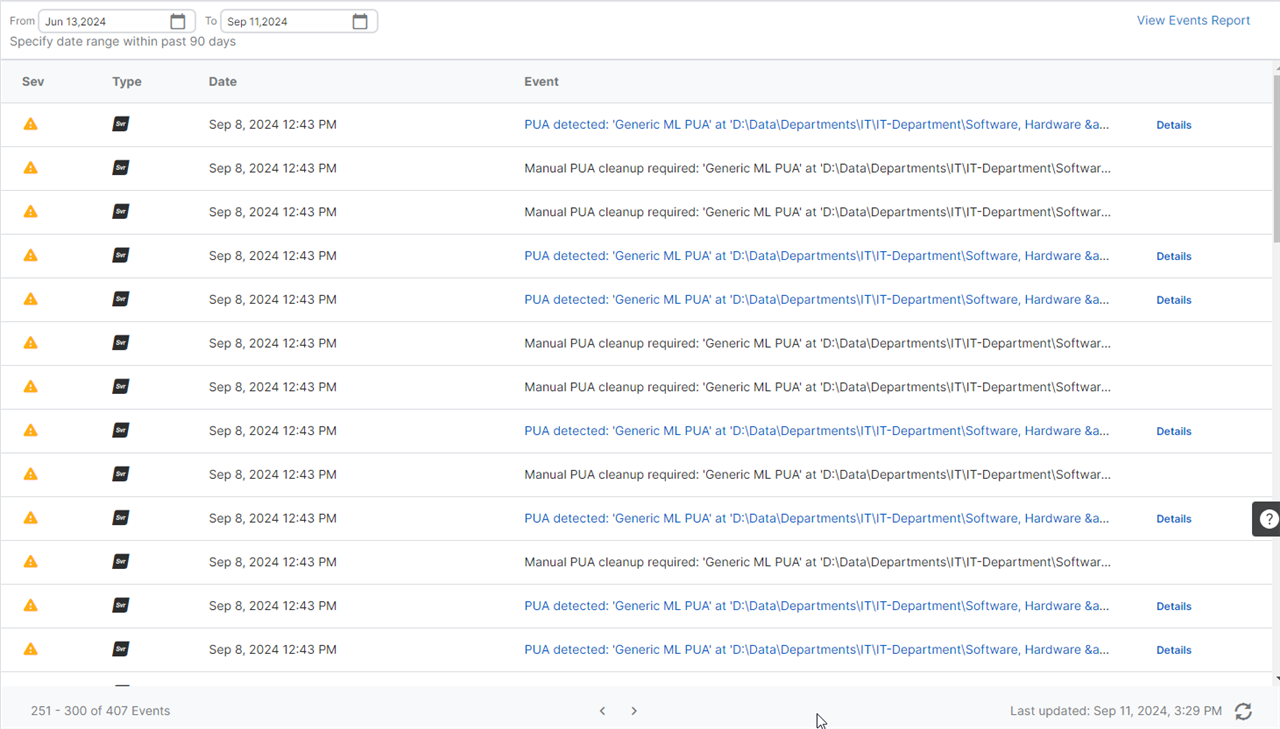
So i go through every item on every page and manually click "Details" to check whether released or not.
Why is there no table-view with multi-selection of quarantine-items to release or delete / acknowledge.
I cannot order the event list, i cannot see from view which is released, and everytime you release one item it jumps back to page 1.
Any ideas/workarounds?
Added tags
[edited by: GlennSen at 1:29 PM (GMT -7) on 3 Oct 2024]

