Disclaimer: This information is provided as-is for the benefit of the Community. Please contact Sophos Professional Services if you require assistance with your specific environment.
Table of Contents
Overview
This recommended read describes the issue of having trouble accessing your Sophos Firewall's web admin.
Note: The information below is taken from the KB:Sophos Firewall: Troubleshooting steps when unable to access the GUI
Check the connectivity to the Sophos Firewall.
- Verify the IP and port through which you are accessing the firewall is correct. If correct, follow the steps in the CLI section to connect to the Sophos Firewall. Otherwise, try to access the device on the correct IP and port.
- Verify if the Firewall is live through PING on the LAN/DMZ/WAN IP of the Sophos Firewall.
- Try to access the User Portal
https://<LAN_IP_OF_SophosFirewall>:<Port(default port is 443)>
- Try to use another browser.
- Try SSH to the firewall on its LAN interface IP on port 22 via Putty. If you get access to the firewall, follow the steps in the Check the tcpdump output and logs section.
Connect to the Sophos Firewall from the CLI
- Refer to Sophos Firewall: How to set up a Serial connection with a console cable
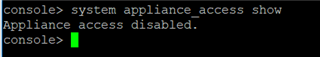
- Verify if the appliance access is disabled by running the following command from the console:
system appliance_access show
- If the Appliance access is disabled, we must enable it with the following command.
system appliance_access enableNote: This will cause a network interruption, override the configured Appliance Access, and allow access to all the services.
- Try to log into the GUI, if it is successful:
- go to Administration > Device access to enable HTTPS on the required zone.
-
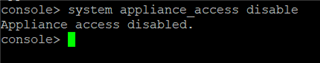
Disable the Appliance access from the CLI using the following command:
system appliance_access disable -
For Further analysis, you can do a Packet capture when you're trying to access the GUI to find out more about the root cause. Read more in Sophos Firewall: How to filter packets using packet capture.
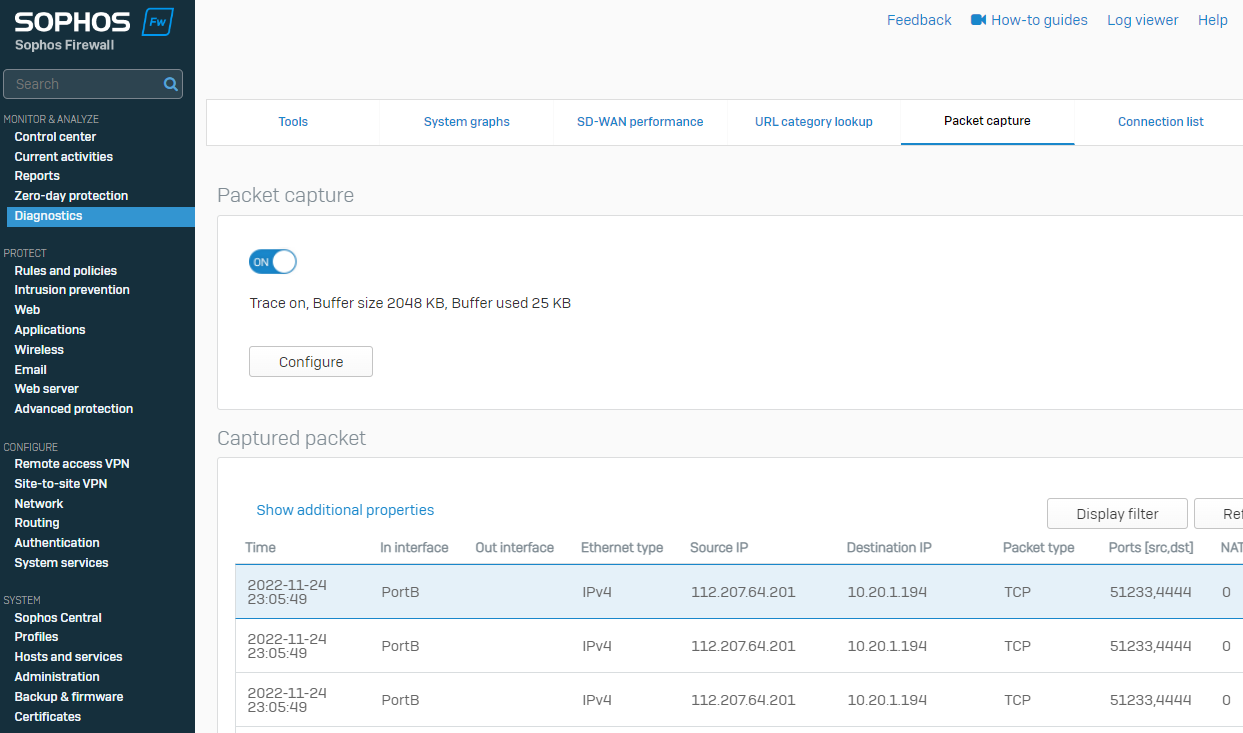
- go to Administration > Device access to enable HTTPS on the required zone.
- If the GUI still inaccessible, verify the configured destination port used for https GUI access using the following command:
psql -U nobody -d corporate -c "select destinationport from tbllocalservicedetails WHERE localserviceid =2"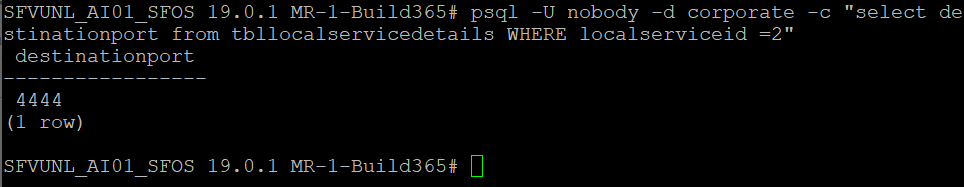
- Continue to the following sections.
Check the tcpdump output and logs.
- Make sure the date and time are set correctly on the firewall. This will help you analyze the tcpdump output accurately.
- From the Advanced Shell CLI, run the following command while accessing the GUI:
tcpdump -nei any port 4444 <or any port which you have configured to access the firewall>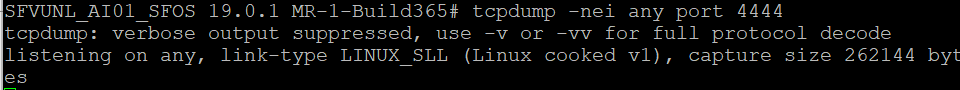
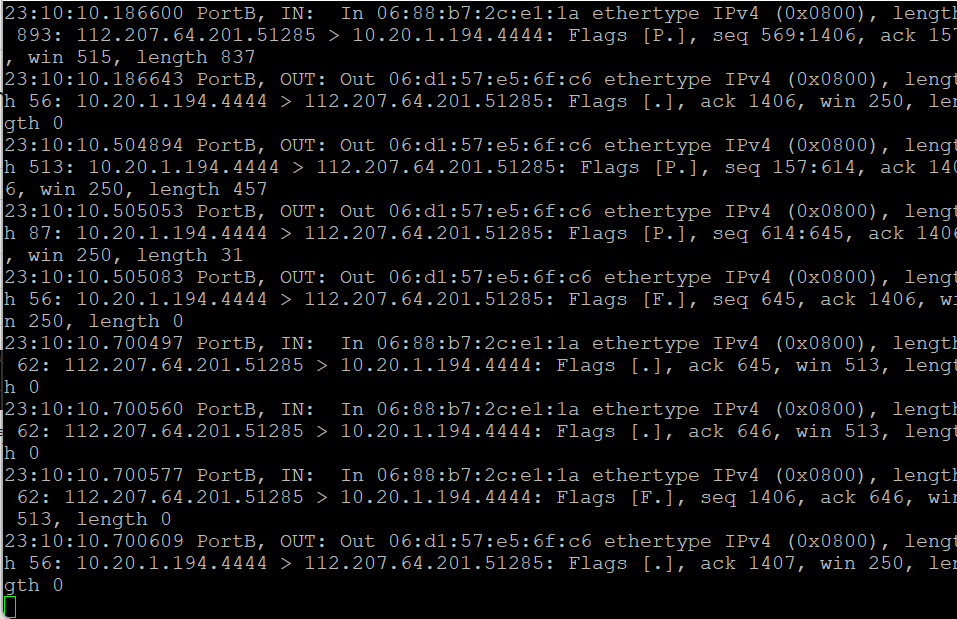
- Analyze if there is traffic that reaches the Firewall. If not, that means something else out of the Sophos perimeter is blocking the traffic.
- If there’s no drop packet while accessing the Firewall, check the following logs for further analysis:
- tomcat.log
- csc.log
- syslog.log
Note: Use these commands:
tail -f /log/tomcat.log
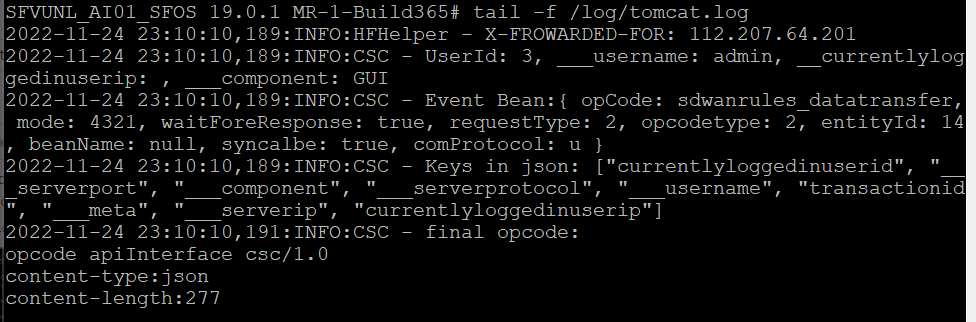
tail -f /log/csc.log
tail -f /log/syslog.log
Check and restart services
- Check services status using the following command
service -S (will show status of all services) - Specifically, you need to check the status of tomcat service (service of GUI) using the following command:
service -S | grep -iE 'tomcat|apache' (After grep you can specify any service name which you would like to grep)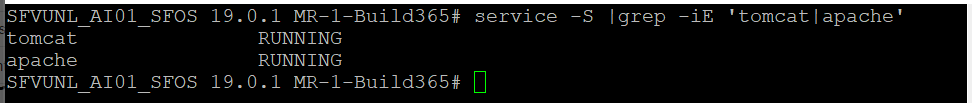
- If the Tomcat or Apache service shows STOPPED, start it respectively with the following command.
service tomcat:start -ds nosyncservice apache:start -ds nosync - If the Tomcat or Apache service shows DEAD, use the command below to restart it.
service tomcat:restart -ds nosyncservice apache:restart -ds nosync
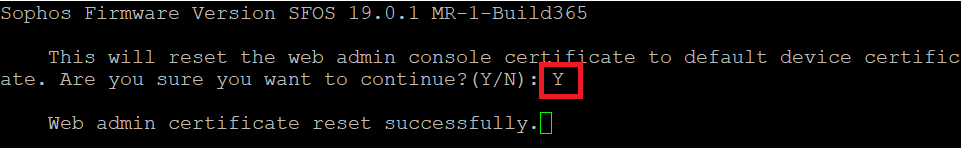
Reset the web admin console certificate to default device certificate
- From the Advanced Shell CLI:
- Choose option 2. System Configuration
- Then, option 4. Reset Default Web Admin Certificate
- Type Y to the following message:
- This should reset the admin certificate to its default, which is ApplianceCertificate.
Additional Troubleshooting Suggestions
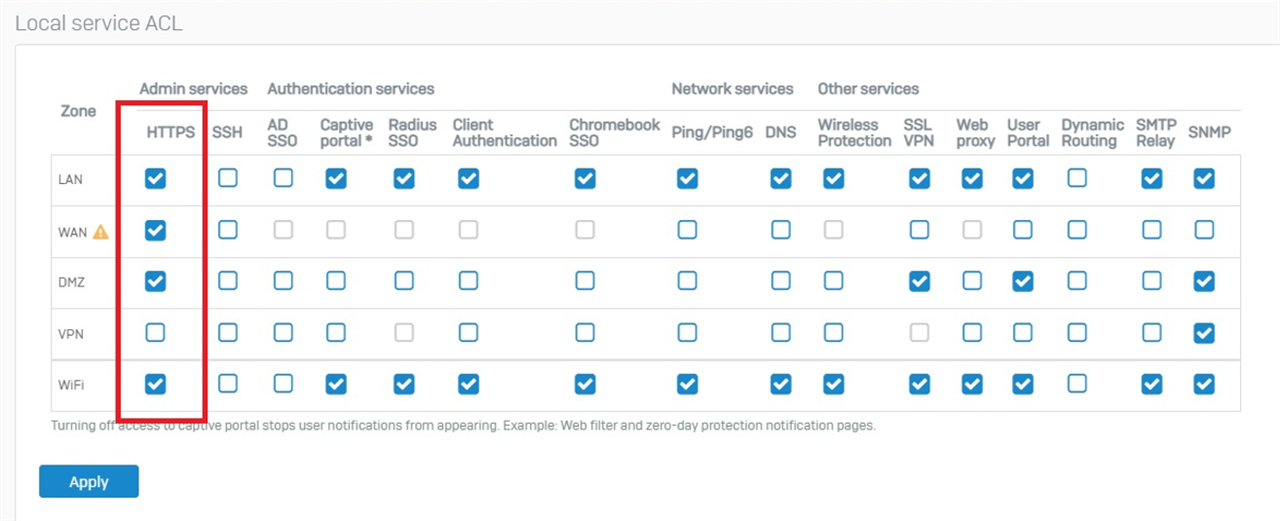
If you are unable to access the Web Admin from a certain zone, first check your Local Service ACLs
- Example: Can you access the web admin via LAN but not the Wi-Fi zone?
- Check if HTTPS Device Access is turned on for that zone
- Administration > Device Access > Local Service ACL
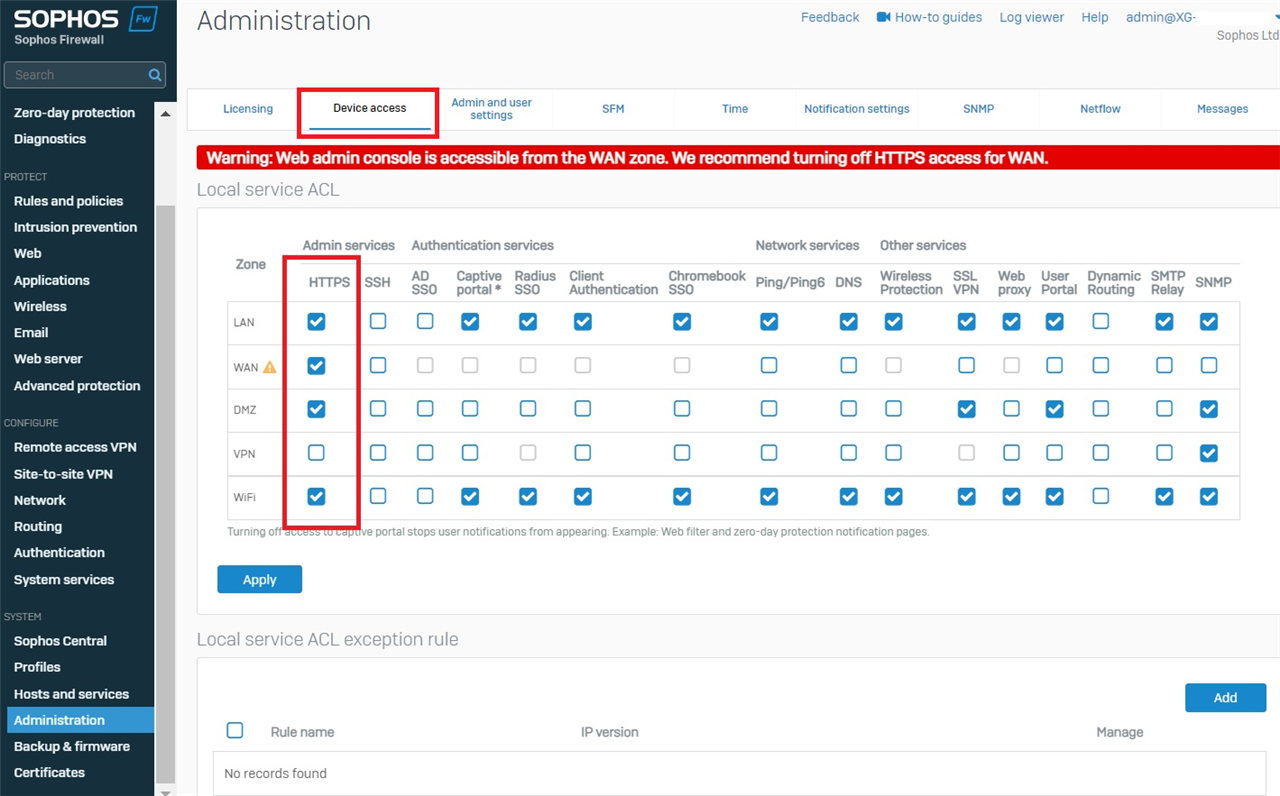
Note: To configure only certain IPs to access local services (HTTPS, etc.), check out Local Service ACL: How to Configure a Local Service ACL Exception Rule
- Check if your device's Certificate Authority is up to date:
- Certificates > Certificate Authorities > Default
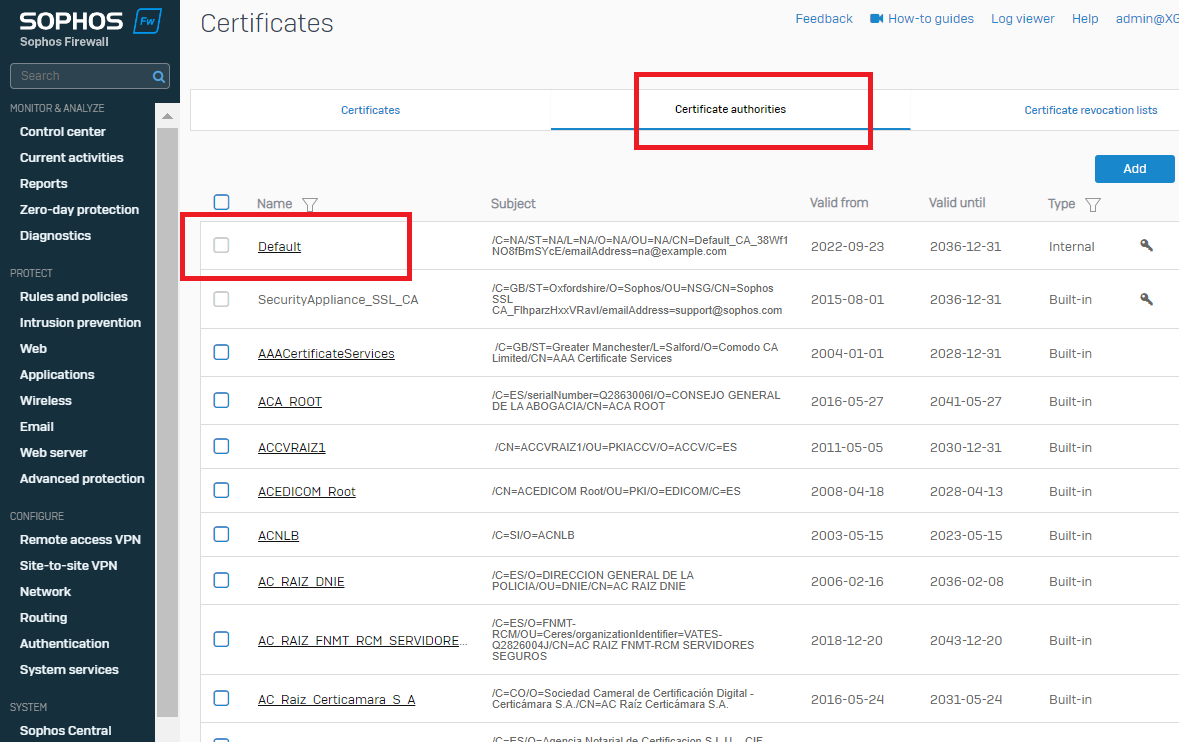
- Certificates > Certificate Authorities > Default
- Confirm which web admin certificate is being used:
- Administration > Admin & User Setting> Admin Console and user-user interaction > Certificate
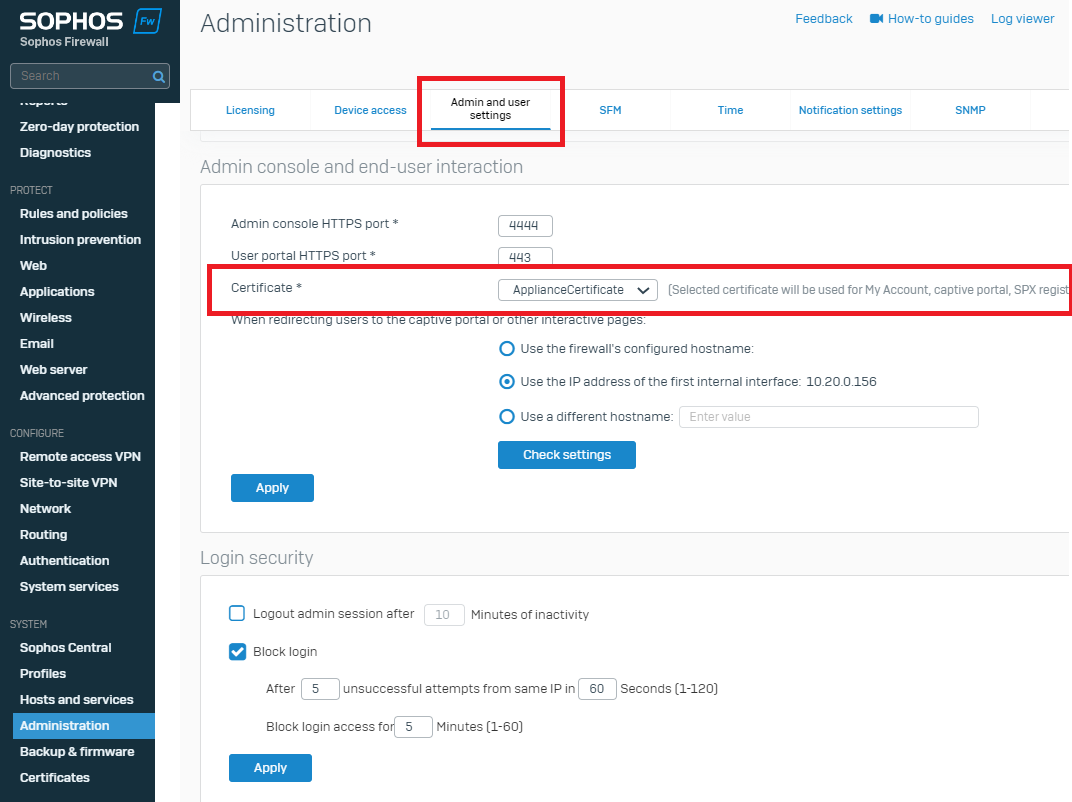
- Administration > Admin & User Setting> Admin Console and user-user interaction > Certificate
- Check if a conflicting DNAT/Business Application rule has been created for the web admin port (Default: 4444)
Revamped RR
[edited by: Erick Jan at 10:14 AM (GMT -7) on 18 Sep 2024]