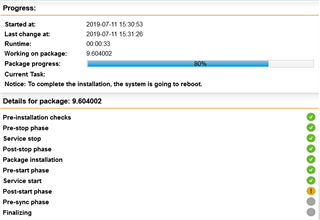
6/27/2019 Update - See the bottom section for new information
Original post
Hello all.
Sophos UTM 9 is running a (modified?) Linux kernel which is currently susceptible to a slew of CVEs disclosed by Netflix: https://github.com/Netflix/security-bulletins/blob/master/advisories/third-party/2019-001.md
Another outline of this issue can be read here: https://access.redhat.com/security/vulnerabilities/tcpsack
To confirm that your version of the UTM is vulnerable, please do the following:
- SSH into your UTM (Sophos has a decent guide for Windows users)
- Type in this command:
cat /proc/sys/net/ipv4/tcp_sack
- If stdout shows a value of
1then SACK is enabled.
I am currently on hold with the Technical team, waiting to determine if we will be allowed to turn SACK off.
Steps for mitigation
Sophos has sent out an email regarding this situation and the products affected. Their link to the new knowledgebase article contains details about steps you can take to mitigate these vulnerabilities until the next release.
In our situation, we went ahead and disabled MTU Probing altogether. Monitoring has shown no drop in performance, and our users have not noticed any decrease in bandwidth.
The steps they lay out for this are:
- Disable MTU Probing:
echo "net.ipv4.tcp_mtu_probing = 0" >> /etc/sysctl.confsysctl -p
- Add the following line to
/var/mdw/etc/iptables/iptable.filterafter(:USR_OUTPUT - [0:0])line at line 29 for UTM v9.603:
-A INPUT -p tcp -m tcpmss --mss 1:500 -j DROP
We have not implemented the other options. Consider your own situation and services before choosing what to disable.
Note: If you wish to make these changes, you must enable ssh via the web manager and login to the console.
This thread was automatically locked due to age.