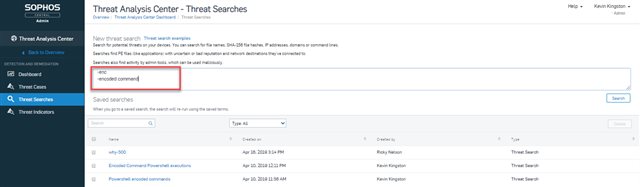
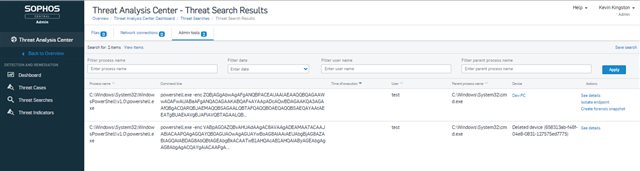
Intercept X Advanced with EDR 1.1 is now available. With this latest update, EDR enabled devices will now start to capture and allow searching for the execution of good admin tools which can be used for malicious purposes. To begin with we’ll be supporting PowerShell executions and will look to add support for new admin tools over time. Analysts now have the ability to track down malicious executions that otherwise may remain hidden. For example, executions which use the encoded command argument are more likely to be associated with bad behavior and are less common in good executions.
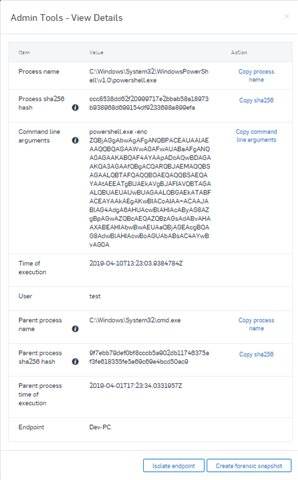
Details being captured include:
- Command line arguments passed
- Time of the execution
- User who ran the process
- Parent process name
- Parent process hash
See here for a video giving an overview of the Admin Tool search capability.
For EDR customers generating forensic snapshots, snapshots generated and converted using the latest version of the SDR Exporter will now contain Windows Authentication audit events from the device in question. See here for more detail on Generating Forensic snapshots.
These new capabilities have also been added to the Intercept X for Server with EDR Early Access Program (EAP) so participants can start using these new features on their servers. Click here for details on joining the Server Early Access Program.