Hello,
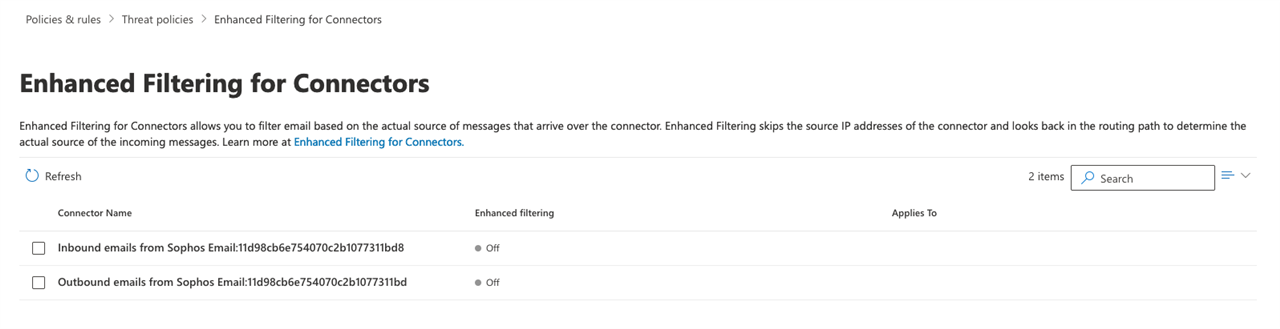
I started to setup Phish Threat for my company but I've trouble with Office 365 that they are opening the E-Mails and links so they distort the reports.
I completely copied the settings of this user community.sophos.com/.../501783 but E-Mails were still blocked, Defender active and so on.
After that I created my own rules and everything works but it seems as if Office365 is opening the E-Mails and links as soon as they come in.
Any solution or idea what I did wrong?
PS: My company is located in germany.
Edited TAGs
[edited by: emmosophos at 7:04 PM (GMT -8) on 16 Feb 2024]