Good afternoon,
We ran a new PhishThreat campaign this morning against all employees and we have differing results on how Sophos handled the email.
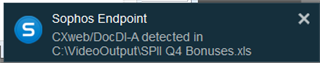
Some users, me for instance, when clicking the attached document, see that Endpoint refused access to the attachment. Other users are not seeing that and they are allowed to open the attachment, enable editing, and enable macros. Endpoint raises no alerts for them.
When I check the user's device all services are up to date and running. Reports show no malware activity on their machine. On my machine, the malware attachment is detected and stopped and the detection is shown in the logs.
I have searched through the settings and compared the configuration on multiple machines and can find no reason why Endpoint catches the malware on my machine, and not on others.
What am I missing?
DAve
This thread was automatically locked due to age.