Hi,
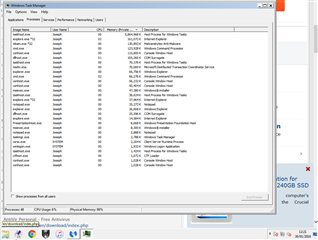
After booting up my system yesterday I found that my desktop (Windows 7 home premium x64) was running extremely slowly. Having checked through the task manager, I found that there were a large number of generic-sounding .exe executables taking up huge amounts of (primarily) system memory, and (secondarily) CPU usage. We're talking up to 98% of the 8GB of RAM, collectively. They come and went, but there's about a dozen at any one time, taking from about 100,000 - 5,000,000K. They included multiple instances of dllhost.exe, conhost.exe, cmd.exe, taskhost.exe, notepad.exe, amongst others. In short, looks like classic malware. I wasn't able to open the file locations (right clicking simply failed to open the folder) until I re-started the system in safe mode, whereupon I found the executables largely to be located in the system32 folder.
Point being, I'd scanned the computer fully only a couple of days ago with Sophos Endpoint, and found nothing. I set up another scan, which (as usual) looked like it would take several hours, so I left it running overnight. Apart from failing to scan chrome appdata (returned SAV interface error 0xa0040202), the scan completed and detected nothing.
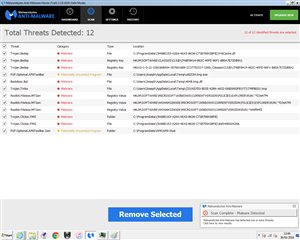
I subsequently downloaded maywarebytes and have just finished running it in safe mode with networking. It detected 12 separate threats, primarily Trojans - image attached. I've quarantined these, and following a restart the system seems to be running normally, though I haven't tried it outside safe mode yet (CPU at 0%, memory at ~25%, most of which is chrome).
Point is, despite keeping sophos up-to-date and scanning regularly, it completely failed to protect me from some fairly obvious threats. I exercise extreme caution when downloading content from the internet, so I really doubt this was something I downloaded. Am I running Sophos incorrectly, and if not, why did this happen, and how can I protect myself better in the future?
Thanks,
Joseph
example of the malware processes (there weren't actually that many at the point I took this capture, more often about 15 all above 100,000K)
Malwarebytes result (scan took only ~30 mins):
This thread was automatically locked due to age.