Hello,
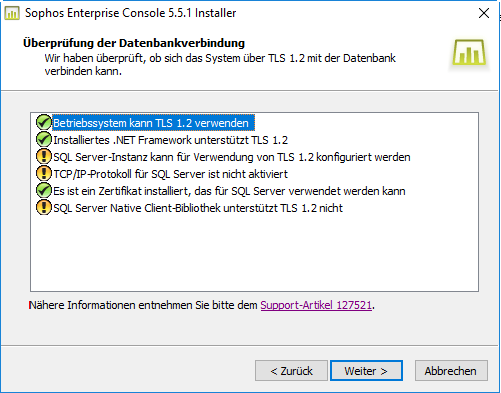
i want to update from SEC 5.5.0 to SEC 5.5.1 and I have fixed these Problems
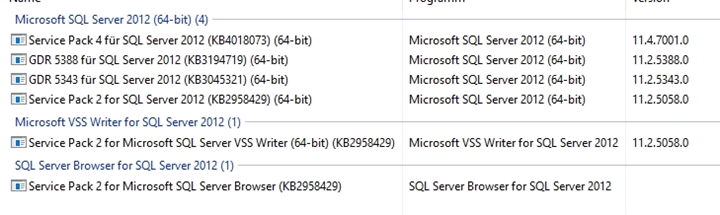
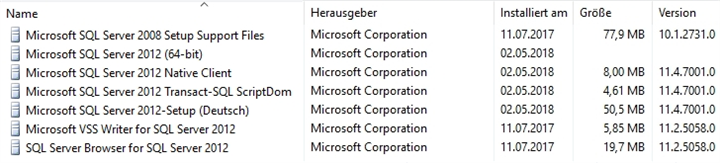
with some SQL-Updates:
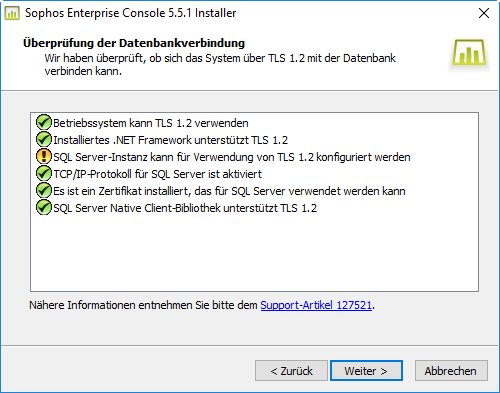
and the status quo is now:
But i don't know on which last screw i have to turn to fix the last problem.
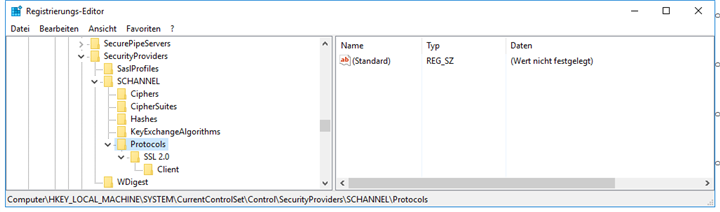
It is necessary to make these registry settings on Windows Server 2016 Standard?
Required Registry settings
If not present create the following registry keys/values:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client
"DisabledByDefault"=dword:00000000
"Enabled"=dword:00000001HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server
"DisabledByDefault"=dword:00000000
"Enabled"=dword:0000000
Because there are not present in the moment:
Thank your for Answer.
This thread was automatically locked due to age.