Disclaimer: This information is posted as-is and the content should be referenced at your own risk
Overview
This article describes how to exclude applications from CryptoGuard functionality in Sophos Central or Sophos Enterprise Console.
Exclusions can be made in both consoles following a CryptoGuard detection on the affected application. If you are encountering an issue where there is no detection, such as a performance issue or an application crashing, please contact Sophos Support for further assistance.
Please note: Sophos does not suggest excluding any applications from any of our protection methods unless the application is fully trusted by the customer. Customers excluding applications do so at their own risk. If you are at all unsure about whether you trust the application mentioned in the detection or the behaviour that is occurring at the time of the alert; please contact Sophos Support for further assistance.
For further information on exclusions methods for exploit mitigation please see this article.
Applies to the following Sophos products and versions
Sophos Central Admin
Enterprise Console 5.5.1
Central Endpoint Intercept X 2.0.14
Exploit Prevention
Central Server Intercept X 2.0.8
What to do
Sophos Central
Please note that CryptoGuard exclusions in Sophos Central are applied to your whole estate once they are saved.
The below methodology will work for CryptoGuard detections where a process is indicated as the cause (as in the below examples C:\Users\Administrator\Desktop\application.exe). If you see a detection with an IP address (for example 192.168.0.1) please contact Sophos Support for further assistance.
Within Sophos Central any CryptoGuard detection is reported in the following ways:
-
- An email is sent to all Administrators warning them of a CryptoGuard detection
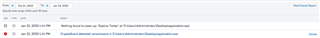
- An alert is raised in the 'Most Recent Alerts' pane on the Dashboard page in Sophos Central
-
- An alert is raised against the device where the Ransomware attack is detected in the Summary and Events views
You can exclude the detection using any of these events:
-
- Click 'Details' on the alert
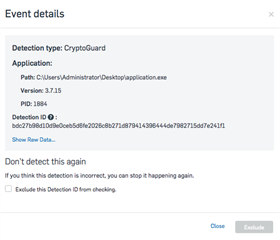
- In the Event Details, you should see the Application name and details as well as the detection type. You will also see the 'Detection ID' which is a unique identifier for this detection:
- Tick 'Exclude this Detection ID from checking' and click Exclude
- Your application will be excluded from CryptoGuard
Sophos Enterprise Console (Requires Enterprise Console 5.5.1 or higher)
The below methodology will work for CryptoGuard detections where a process is indicated as the cause (for example C:\Users\Administrator\Desktop\application.exe). If you see a detection with an IP address (for example 192.168.0.1) please contact Sophos Support for further assistance.
Within Sophos Enterprise Console any CryptoGuard detection is reported in the following ways:
-
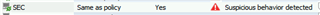
- A 'Suspicious behaviour detected' alert will be raised against the machine in the Enterprise Console
-
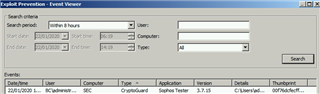
- An event is logged in the 'Exploit Prevention Events' log
To exclude an application from CryptoGuard you can follow the below steps:
-
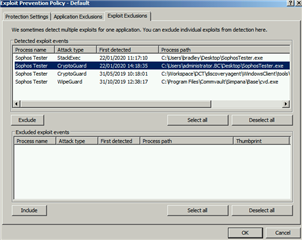
- In the Enterprise Console navigate to 'Policies' > 'Exploit Prevention'
- Locate the Exploit Prevention policy relating to the affected machine(s)
- Select 'Exploit Exclusions'
- Highlight the required CryptoGuard detection in the list that you wish to exclude and click 'Exclude'
- Click 'OK' to apply your changes
- This particular application will then be excluded from CryptoGuard on machines protected by this Exploit Prevention policy
Have an idea or suggestion regarding our Documentation, Knowledgebase, or Videos? Please visit our User Assistance forum on the Community to share your idea!