While looking at the "sophos_ip_journal table", I noticed the interesting field "redirectionState" which could be useful to find traffic that is being covertly redirected to a local proxy before being sent on its way unbeknown to the end-user.
Most people are familiar with the concept of traffic going through an upstream web proxy but on Windows, the Windows Filtering Platform (WFP) can be used to redirect or make decisions on network traffic on the local computer. Think VPN clients, Firewalls, DLP, Web Control. In fact, the Sophos Web Protection and Control feature on Windows 8.1 and later uses WFP to redirect browser traffic using the swi_callout.sys driver to a local proxy process swi_fc.exe. This process is then able to make decisions on the traffic. I.e. block a known malicious site or a certain category of site based on the policy, etc.
So while running the Sophos endpoint client, it is expected that browser traffic is redirected as mentioned, but it might be worth searching for web traffic that is being redirected to a process with low-reputation or generally questionable. For example, a query to start us off might look like:
select spj.pathname, spj.sha256, sfp.mlScore, sfp.localRep
from sophos_ip_journal as ipj
join sophos_process_journal as spj on spj.SophosPID = ipj.targetSophosPID
join sophos_file_properties as sfp on sfp.sha256 = spj.sha256
where ipj.redirectionState=1
and ((sfp.mlScore > 20) or (sfp.localRep < 90))
and ipj.originaldestinationPort in ('80','443','8080') limit 1 ;
The results for which would be 0 if all was well, but if you see returned, as an example the following output, you might want to have a search for the sha256 of this suspicious proxy.exe as it could be inspecting web traffic for malicious purposes.
+------------------------------------------------------------------------+------------------------------------------------------------------+---------+----------+
| pathname | sha256 | mlScore | localRep |
+------------------------------------------------------------------------+------------------------------------------------------------------+---------+----------+
| C:\hacker\proxy.exe | 750c1809dea9c57b5d6ee38958b9c635ccda5b0a2c347f31f22ab838a1b94ef2 | 70 | 20 |
+------------------------------------------------------------------------+------------------------------------------------------------------+---------+----------+
This initial starter query is limited to traffic initially intending on going to ports 80 (HTTP), 443 (HTTPS) or 8080 (Common Proxy) but this could be dropped to consider more.
The ml and local reputation thresholds are also a little arbitrary but if we adjust them, to prove the query works, such that the clause is:
and ((sfp.mlScore <= 10) or (sfp.localRep > 95))
We would see our friend swi_fc.exe which is expected:
+------------------------------------------------------------------------+------------------------------------------------------------------+---------+----------+
| pathname | sha256 | mlScore | localRep |
+------------------------------------------------------------------------+------------------------------------------------------------------+---------+----------+
| C:\Program Files (x86)\Common Files\Sophos\Web Intelligence\swi_fc.exe | 650c1809dea9c57b5d6ee38958b9c635ccda5b0a2c347f31f22ab838a1b94ef2 | 10 | 91 |
+------------------------------------------------------------------------+------------------------------------------------------------------+---------+----------+
Note: "C:\Program Files (x86)\Common Files\Sophos\Web Intelligence\swi_fc.exe" as of now has a mlScore of 10 and a localRep of 91. Where the lower the mlScore the more trustworthy and the higher the localRep the better.
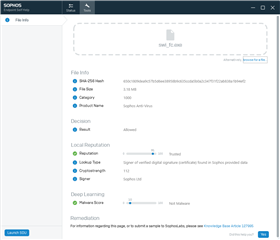
Tip: To check the mlScore or localRep of any exe on the computer, you can use the "File Info" page (under "Tools") of Endpoint Self Help. For example:
As I mention in this post: https://community.sophos.com/products/intercept/early-access-program/f/recommended-reads/120154/live-response---using-command-line-tools-to-check-files ESH uses the command line tool MLFileInfo.exe which could also be used.
Hope this is something you might find helpful.
Regards,
Jak