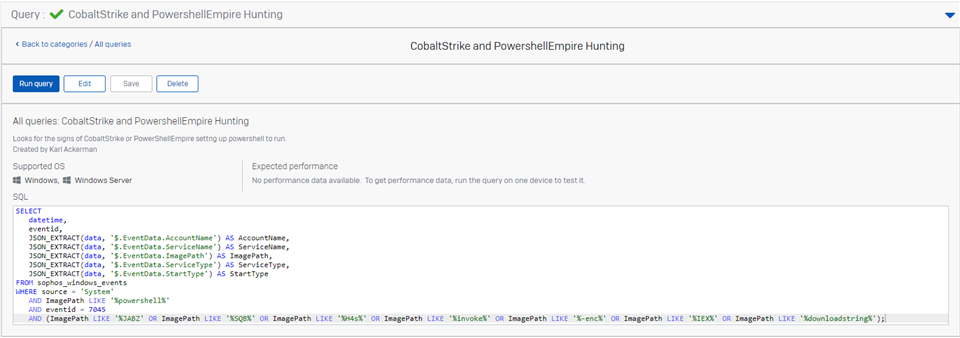
Like the earlier post we are often helping an account after they have been breached and are needing to deploy InterceptX with EDR on devices that where breached. In these situations we can't depend on the Sophos Journals for our historic activity queries. In this case we will use the windows events logs to look for suspect process that installed a service to run powershell.
it is mainly looking for malicious services being installed that execute powershell associated with Cobalt Strike or PowerShellEmpire
datetime,
eventid,
JSON_EXTRACT(data, '$.EventData.AccountName') AS AccountName,
JSON_EXTRACT(data, '$.EventData.ServiceName') AS ServiceName,
JSON_EXTRACT(data, '$.EventData.ImagePath') AS ImagePath,
JSON_EXTRACT(data, '$.EventData.ServiceType') AS ServiceType,
JSON_EXTRACT(data, '$.EventData.StartType') AS StartType
FROM sophos_windows_events
WHERE source = 'System'
AND ImagePath LIKE '%powershell%'
AND eventid = 7045
AND (ImagePath LIKE '%JABZ' OR ImagePath LIKE '%SQB%' OR ImagePath LIKE '%H4s%' OR ImagePath LIKE '%invoke%' OR ImagePath LIKE '%-enc%' OR ImagePath LIKE '%IEX%' OR ImagePath LIKE '%downloadstring%');
JSON_EXTRACT(data, '$.EventData.AccountName') AS AccountName,
JSON_EXTRACT(data, '$.EventData.ServiceName') AS ServiceName,
JSON_EXTRACT(data, '$.EventData.ImagePath') AS ImagePath,
JSON_EXTRACT(data, '$.EventData.ServiceType') AS ServiceType,
JSON_EXTRACT(data, '$.EventData.StartType') AS StartType
FROM sophos_windows_events
WHERE source = 'System'
AND ImagePath LIKE '%powershell%'
AND eventid = 7045
AND (ImagePath LIKE '%JABZ' OR ImagePath LIKE '%SQB%' OR ImagePath LIKE '%H4s%' OR ImagePath LIKE '%invoke%' OR ImagePath LIKE '%-enc%' OR ImagePath LIKE '%IEX%' OR ImagePath LIKE '%downloadstring%');