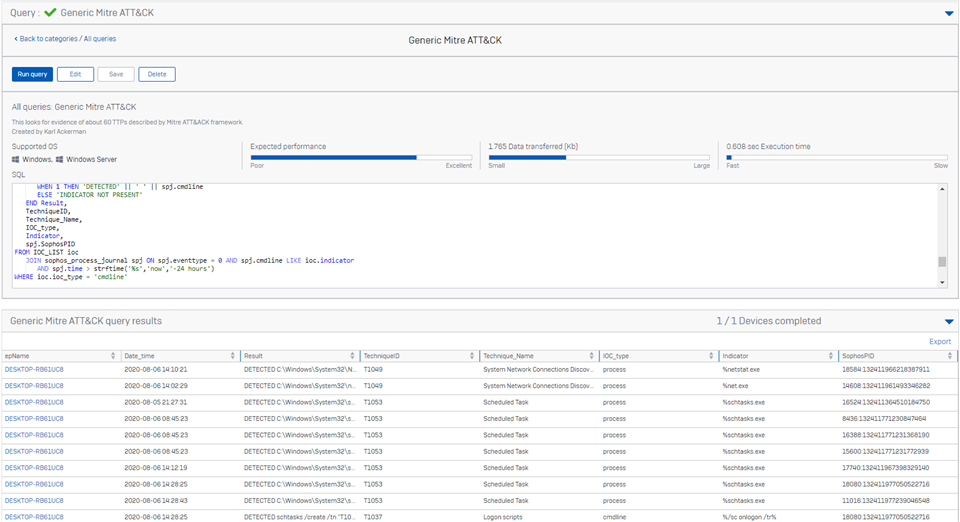
I have been experimenting with queries that identify activity that maps to the ATT&CK framework from MITRE. We have published some queries that already do some of that work. (Search for the Caldera query in the console). Below is another bit of work to detect another set of TTPs.
Some notes on Mitre and ATT&CK
MITRE is a US government funded non-profit entity that does lots of interesting IT research work from radar arrays to security stuff. They are based just down the street from our offices in Burlington. A good group of folks. Oh yea what does MITRE stand for...
- MITRE - Massachusetts Institute of Technology Research & Engineering
ATT&CK is a program run by MITRE run that classifies the tactics techniques and procedures used by threat actors (Criminals, Nationstates, hacktivists and the like). https://attack.mitre.org/
- ATT&CK - Adversarial Tactics, Techniques, and Common Knowledge
Over the last few years MITRE has run a test and published results. You have to pay to participate in the test and they will test your product vs a simulated threat actor. Sophos has not participated in the last two years because you have to ensure the product being tested is configured to NOT BLOCK malicious activity and instead allow it to proceed. The test is to determine if you can notify or observe the suspect and malicious activity. Sophos endpoint will simply kill malware when we see it and that means they can not go very far in any tests as we usually prevent the initial beachhead on the device from which the adversary takes additional actions.
In 2020 MITRE changed the test to allow products that BLOCK malicious activity and we will be participating.
Most of the techniques described in the Mitre ATT&CK framework are not malicious they are just things that folks have observed that bag guys do. Like if the adversary gets onto a device they may run a command to see what other devices are in the network, or check what type of operating system they are on. These are things that admins and even some users do and by themselves are not malicious. Other things in the test are malicious like attaching to the LSASS process and extracting the clear text password.
Below is a very noisy (IE detections do not mean you have an advanced threat actor in your environment) query to identify some of the Mitre TTPs.
You can change the JOIN to a LEFT JOIN if you want verbose mode where we indicate if the indicator was NOT found instead of just reporting on detections.
------------
WITH IOC_HUNT_BY_TYPE AS (
WITH IOC_LIST (TechniqueID, Technique_Name, IOC_Type, Indicator) AS (
VALUES
('T????','Memory loaded Software','cmdline','%IEX (New-Object Net.WebClient).DownloadString%'),
('T????','Memory loaded Software','cmdline','%SQBm%'),
('T????','Powershell Install','cmdline','%download%powershell%'),
('T1003','Credential Dumping','cmdline','%mimikatz%'),
('T1003','Credential Dumping','cmdline','%dumpcreds%'),
('T1003','Credential Dumping','process','%gsecdump.exe'),
('T1003','Credential Dumping','process','%wce.exe'),
('T1003','Credential Dumping','cmdline','%save hklm\sam%'),
('T1003','Credential Dumping','cmdline','%save hklm\system%'),
('T1003','Credential Dumping','cmdline','%save hklm\security%'),
('T????','process Dumping','process','%procdump.exe'),
('T1003','Credential Dumping','cmdline','%-ma lsass.exe%'),
('T1003','Credential Dumping','filepath','c:\windows\temp\lsass_dump.dmp'),
('T1003','Credential Dumping','cmdline','%C:\windows\System32\comsvcs.dll, MiniDump (Get-Process lsass).id $env:TEMP\lsass-comsvcs.dmp full%'),
('T1003','Credential Dumping','process','%Outflank-Dumpert.exe'),
('T1003','Credential Dumping','process','%mimikatz.exe'),
('T1003','Credential Dumping','cmdline','lsass.dmp'),
('T1003','Credential Dumping','cmdline','%ac i ntds%ifm%create full%'),
('T1003','Credential Dumping','process','%ntdsutil%'),
('T1003','Credential Dumping','process','%vssadmin.exe'),
('T1003','Credential Dumping','cmdline','%create shadows /for=c:%'),
('T1003','Credential Dumping','cmdline','%\\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy1\Windows\NTDS\NTDS.dit%'),
('T1003','Credential Dumping','cmdline','%\\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy1\Windows\System32\config\SYSTEM%'),
('T1003','Credential Dumping','cmdline','%/S cpassword %logonserver%\sysvol\*.xml%'),
('T1003','Credential Dumping','cmdline','%Get-GPPPassword -Verbose%'),
('T1003','Credential Dumping','process','%accesschk.exe'),
('T1012','query registry','process','%reg.exe'),
('T1012','query registry','cmdline','%HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows%'),
('T1012','query registry','cmdline','%HKLM\Software\Microsoft\Windows\CurrentVersion\RunServicesOnce%'),
('T1012','query registry','cmdline','%HKCU\Software\Microsoft\Windows\CurrentVersion\RunServicesOnce%'),
('T1012','query registry','cmdline','%HKLM\Software\Microsoft\Windows\CurrentVersion\RunServices%'),
('T1012','query registry','cmdline','%HKCU\Software\Microsoft\Windows\CurrentVersion\RunServices%'),
('T1012','query registry','cmdline','%HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\Notify%'),
('T1012','query registry','cmdline','%HKLM\Software\Microsoft\Windows NT\CurrentVersion\Winlogon\Userinit%'),
('T1012','query registry','cmdline','%HKCU\Software\Microsoft\Windows NT\CurrentVersion\Winlogon\\Shell%'),
('T1012','query registry','cmdline','%HKLM\Software\Microsoft\Windows NT\CurrentVersion\Winlogon\\Shell%'),
('T1012','query registry','cmdline','%HKLM\Software\Microsoft\Windows NT\CurrentVersion\Winlogon\Userinit%'),
('T1012','query registry','cmdline','%HKLM\Software\Microsoft\Windows NT\CurrentVersion\Winlogon\Userinit%'),
('T1012','query registry','cmdline','%HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\ShellServiceObjectDelayLoad%'),
('T1012','query registry','cmdline','%HKLM\Software\Microsoft\Windows\CurrentVersion\RunOnce%'),
('T1012','query registry','cmdline','%HKLM\Software\Microsoft\Windows\CurrentVersion\RunOnceEx%'),
('T1012','query registry','cmdline','%HKLM\Software\Microsoft\Windows\CurrentVersion\Run%'),
('T1012','query registry','cmdline','%HKLM\Software\Microsoft\Windows\CurrentVersion\Run%'),
('T1012','query registry','cmdline','%HKCU\Software\Microsoft\Windows\CurrentVersion\RunOnce%'),
('T1012','query registry','cmdline','%HKLM\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run%'),
('T1012','query registry','cmdline','%HKCU\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run%'),
('T1012','query registry','cmdline','%HKLM\system\currentcontrolset\services /s | findstr ImagePath 2>nul | findstr /Ri ".*\.sys$%'),
('T1012','query registry','cmdline','%HKLM\Software\Microsoft\Windows\CurrentVersion\Run%'),
('T1027','Obfuscated Files or Information','cmdline','%$OriginalCommand =%'),
('T1027','Obfuscated Files or Information','cmdline','%[System.Text.Encoding]::Unicode.GetBytes%'),
('T1027','Obfuscated Files or Information','cmdline','%[Convert]::ToBase64String%'),
('T1027','Obfuscated Files or Information','cmdline','%EncodedCommand%'),
('T1027','Obfuscated Files or Information','cmdline','%Set-ItemProperty -Force -Path HKCU%'),
('T1027','Obfuscated Files or Information','cmdline','%-Command "IEX%'),
('T1027','Obfuscated Files or Information','cmdline','%[Text.Encoding]::UNICODE.GetString([Convert]::FromBase64String%'),
('T1028','Windows Remote Management','cmdline','%Enable-PSRemoting -Force%'),
('T1028','Windows Remote Management','cmdline','%Document.ActiveView.ExecuteShellCommand%'),
('T1028','Windows Remote Management','cmdline','%/user:DOMAIN\Administrator /password:%'),
('T1028','Windows Remote Management','process','%wmic.exe'),
('T1028','Windows Remote Management','cmdline','%HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\osk.exe\%/v \%Debugger\% /t REG_SZ /d \%cmd.exe\% /f%'),
('T1028','Windows Remote Management','cmdline','%\\localhost -u DOMAIN\Administrator -p%'),
('T1028','Windows Remote Management','process','%psexec.exe'),
('T1028','Windows Remote Management','cmdline','%invoke-command -ComputerName localhost -scriptblock {ipconfig}%'),
('T1031','Modify Existing Service','cmdline','%binPath= %C:\windows\system32\WindowsPowerShell\v1.0\powershell.exe -noexit -c%'),
('T1028','Windows Remote Management','cmdline','%invoke-command -ComputerName localhost -scriptblock {ipconfig}%'),
('T1028','Windows Remote Management','cmdline','%invoke-command -ComputerName localhost -scriptblock {ipconfig}%'),
('T1037','Logon scripts','cmdline','%ADD HKCU\Environment /v UserInitMprLogonScript /t REG_SZ /d%'),
('T1037','Logon scripts','cmdline','%/sc onlogon /tr%'),
('T1037','Logon scripts','cmdline','%$env:APPDATA\Microsoft\Windows\Start Menu\Programs\Startup%'),
('T1037','Logon scripts','cmdline','%C:\ProgramData\Microsoft\Windows\Start Menu\Programs\StartUp%'),
('T1048','Exfiltration Over Alternative Protocol','cmdline','%$ping = New-Object System.Net.Networkinformation.ping; foreach%'),
('T1049','System Network Connections Discovery','process','%netstat.exe'),
('T1049','System Network Connections Discovery','process','%net.exe'),
('T1049','System Network Connections Discovery','cmdline','%Get-NetTCPConnection%'),
('T1050','Service Instalation','cmdline','%New-Service -Name%'),
('T1050','Service Instalation','cmdline','%Start-Service -Name%'),
('T1053','Scheduled Task','cmdline','%/Create /SC ONCE /TN spawn /TR%'),
('T1053','Scheduled Task','process','%schtasks.exe'),
('T1053','Scheduled Task','cmdline','%/Create /S localhost /RU DOMAIN\user%'),
('T1053','Scheduled Task','cmdline','%New-ScheduledTaskAction -Execute%'),
('T1053','Scheduled Task','cmdline','%New-ScheduledTaskTrigger -AtLogon%'),
('T1053','Scheduled Task','cmdline','%New-ScheduledTaskPrincipal -GroupId%'),
('T1053','Scheduled Task','cmdline','%New-ScheduledTaskSettingsSet%'),
('T1053','Scheduled Task','cmdline','%New-ScheduledTask -Action%'),
('T1053','Scheduled Task','cmdline','%Register-ScheduledTask%'),
('T1063','Security Software Discovery','cmdline','%| findstr /i virus%'),
('T1063','Security Software Discovery','cmdline','%| findstr /i cb%'),
('T1063','Security Software Discovery','cmdline','%| findstr /i sophos%'),
('T1063','Security Software Discovery','cmdline','%| findstr /i defender%'),
('T1063','Security Software Discovery','cmdline','%findstr.exe 385201%'),
('T1063','Security Software Discovery','cmdline','%get-process | ?{$_.Description -like "*virus*"}%'),
('T1063','Security Software Discovery','cmdline','%get-process | ?{$_.Description -like "*defender*"}%'),
('T1063','Security Software Discovery','cmdline','%get-process | ?{$_.Description -like "*sophos*"}%'),
('T1063','Security Software Discovery','cmdline','%/Namespace:\\root\SecurityCenter2 Path AntiVirusProduct Get displayNam%'),
('T1069','Permission Groups Discovery','cmdline','%localgroup%'),
('T1069','Security Software Discovery','cmdline','%get-localgroup%'),
('T1069','Security Software Discovery','cmdline','%group /domai% "Domain Admins"%'),
('T1069','Security Software Discovery','cmdline','%groups "Account Operators" /doma%'),
('T1069','Security Software Discovery','cmdline','%groups "Exchange Organization Management" /doma%'),
('T1069','Security Software Discovery','cmdline','%group "BUILTIN\Backup Operators" /doma%'),
('T1070','Indicator Removal on Host','cmdline','%cl System%'),
('T1070','Indicator Removal on Host','cmdline','%usn deletejournal /D%'),
('T1070','Indicator Removal on Host','cmdline','%Remove-Item C:\Windows\System32\winevt\Logs\Security.evtx%'),
('T1070','Indicator Removal on Host','cmdline','%Clear-EventLog -logname%'),
('T1531','Account Removal','cmdline','%user%/delete%')
)
/* CHECK filepath of */
SELECT DISTINCT
datetime(time,'unixepoch') Date_time,
CASE sfj.pathname NOT NULL
WHEN 1 THEN 'DETECTED' || ' ' || sfj.pathname
ELSE 'INDICATOR NOT PRESENT'
END Result,
TechniqueID,
Technique_Name,
IOC_type,
Indicator,
'NOT APPLICABLE' SophosPID
FROM IOC_LIST ioc
JOIN sophos_file_journal sfj ON sfj.subject = 'FileDataChanges' AND sfj.pathname LIKE ioc.indicator
AND sfj.time > strftime('%s','now','-24 hours')
WHERE ioc.ioc_type = 'filepath'
UNION ALL
/* CHECK cmdline of historic Processes */
SELECT DISTINCT
datetime(time,'unixepoch') Date_time,
CASE spj.cmdline NOT NULL
WHEN 1 THEN 'DETECTED' || ' ' || spj.cmdline
ELSE 'INDICATOR NOT PRESENT'
END Result,
TechniqueID,
Technique_Name,
IOC_type,
Indicator,
spj.SophosPID
FROM IOC_LIST ioc
JOIN sophos_process_journal spj ON spj.eventtype = 0 AND spj.cmdline LIKE ioc.indicator
AND spj.time > strftime('%s','now','-24 hours')
WHERE ioc.ioc_type = 'cmdline'
UNION ALL
/* CHECK processes in last 1 hour */
SELECT DISTINCT
datetime(time,'unixepoch') Date_time,
CASE spj.SophosPID NOT NULL
WHEN 1 THEN 'DETECTED' || ' ' || spj.pathname
ELSE 'INDICATOR NOT PRESENT'
END Result,
TechniqueID,
Technique_Name,
IOC_type,
Indicator,
spj.sophosPID
FROM IOC_LIST ioc
JOIN sophos_process_journal spj ON spj.eventtype = 0 AND spj.pathname LIKE ioc.indicator
AND spj.time > strftime('%s','now','-24 hours')
WHERE ioc.ioc_type = 'process'
)
SELECT *
FROM IOC_HUNT_BY_TYPE
ORDER BY Result;