Sophos implements many layers of security, including control policies configurable for your Endpoints protected by Intercept X Advanced. One such control policy that is vital to give attention to is Application Control. The following article is not a Sophos sponsored best practice, but the opinion of this engineer and utilizing this control for years in the field as a line of defense.
What is Application Control (Intercept X Advanced):
Documentation for Application Control
Where can I configure Application Control?
How should I configure Application Control?
Configure Application Control - Allow Mode
Configure Application Control - Block Mode
What is Application Control (Intercept X Advanced):
We are a complete cybersecurity ecosystem, so we also have Application Controls in the Sophos Firewall, however, the Application Control this article is focused on is Application Control policies enabled by use of Intercept X Advanced on Windows/macOS. As stated in Sophos Documentation, "Application control lets you detect and block applications that are not a security threat, but that you decide are unsuitable for use in the office"
Documentation for Application Control
Sophos Central Admin - Application Control
Where can I configure Application Control?
From within Sophos Central, visit "My Products > Endpoint/Server > Policies"
Within Policies, scroll down to Application Control and select either your Base Policy or a targeted Policy for Security Groups/Users/Computers:
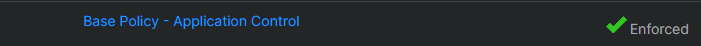
For this article, we will utilize the Base Policy - Application Control
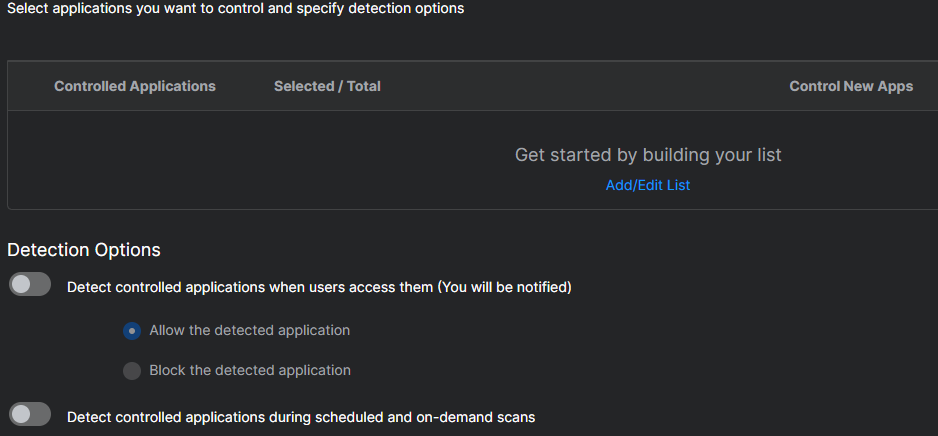
If this is your first time accessing Application Control policies, it will appear unconfigured with a section to Add/Edit an Application list and the ability to enable/disable the detect/control options.
How should I configure Application Control?
There are two methods available when it comes to application control:
- Allow the Detected Application (My Recommendation if you are unsure and need to audit first)
- This mode will look for applications you select from the list above and log that it is either installed or was attempted to be installed on a system, providing you a trail of applications that you can run "Allowed Applications" reporting for up to 90 days
- Block the Detected Application (My Recommendation if you know what you want to block)
- This mode will detect all applications you select from the list above and not only log that it was detected but also control its ability to execute. (Note: Downloading the app in the first place, is controlled by Web Control policies or Sophos Firewall using "Executable Files" categories in "Warn/Block" mode.)
You can also enable Detect Controlled Applications during schedule and on-demand scans if you utilize these in your Threat Policies.
Configure Application Control - Allow Mode
Configure Application Control - Block Mode
Configure Application Control - Allow Mode
Doing this can take upwards of 5-6 minutes to initially configure but will give you a great overview of the use of applications in your organization. As always, if you dont see an application in our list, but have one you would like to control, you can click on the "Application Control Request" and submit that to our Labs team.
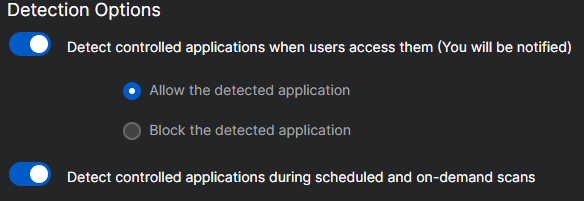
To begin, under "Detection Options" toggle "Detect controlled applications when users access them (You will be notified)", then select "Allow the detected application". Additionally, toggle "Detect controlled applications during scheduled and on-demand scans" to be Enable it.
Now, in the Controlled Applications list above this, select "Add/Edit List" to begin selecting applications: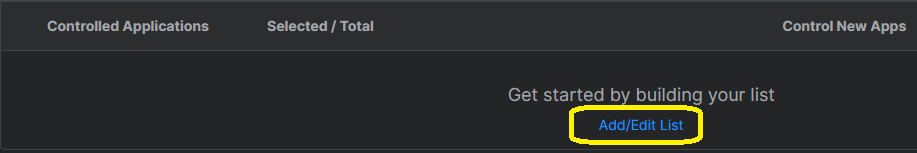
This will take some time in the next step but is absolutely worth it to get an overview of utilized applications in your organization, and then determining what you should now block by using the "Allowed Applications" reports.
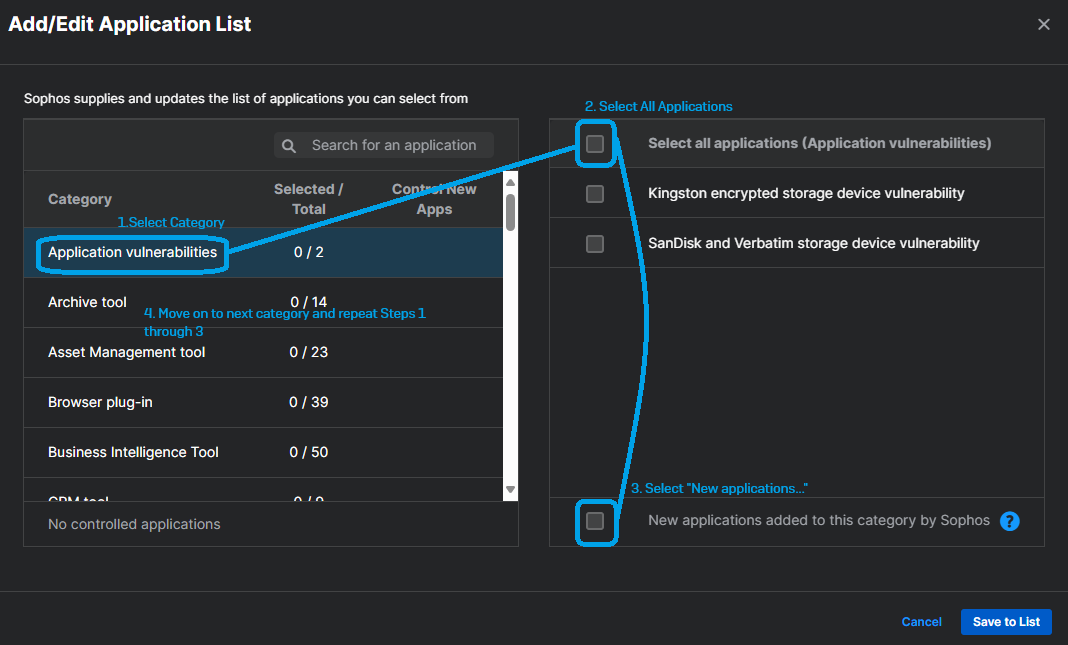
Within the Add/Edit Application List as seen below, you will start by 1) Selecting the category, then 2) Click "Select All Applications (Application Vulnerabilities), then 3) Select "New applications added to this category by Sophos", then 4) do the same thing for each category on the left pane, until all Applications are selected.
Then "Save" the policy and let it operate for up to 7 days to get an initially overview of all applications it can detect in the environment.
You can then review the captured Applications by visiting "Reports"
OR
and select "Allowed Applications" which will show you all applications detected for the last 7, 30, 90 days or Custom time period.
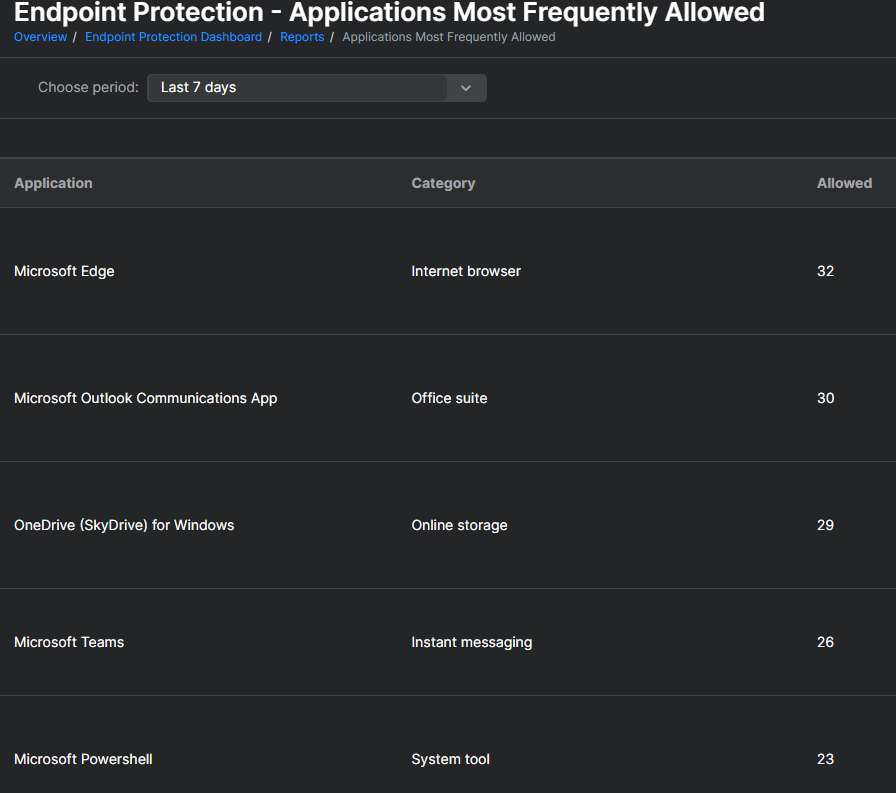
Should you wish to Export to CSV or PDF for further review and to update your policies in the future for the "Block Mode" these reports can be helpful.
Configure Application Control - Block Mode
This is ultimately the condition you want Application Control to be in going forward. If you already know the applications you want to control, or you have reviewed your Allowed Applications report for apps you have deemed unwanted in the organization, you can now either "Reset" the Base Policy and set up this control policy to "Block detected applications" and populate the list of applciations with only those apps you choose to restrict, or if you prefer not to "Reset" the policy you can change the policy action to "Block..." and go through your list of applications "unchecking" the ones you wish to permit in the environment, leaving all "checked" apps now in blocked when detected mode. Alternately you could clone the policy, or create a new one and now target a test/pilot group of computers/users to confirm your selections before production-wide implementation.
To begin, we will "Reset" our Base Application Control policy:
Once reset is completed, modify your "Detection Options" as follows:
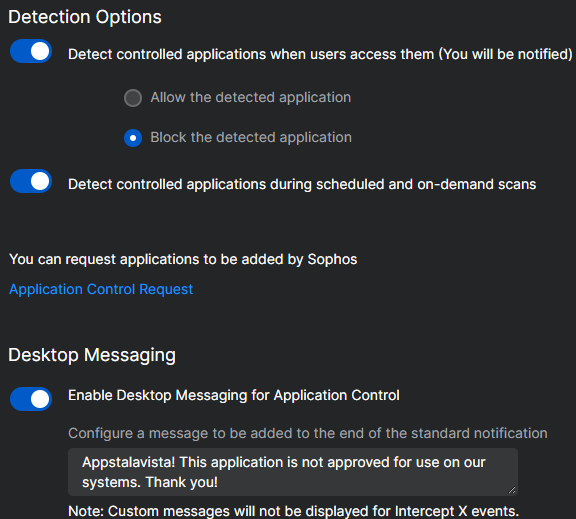
Toggle/Enable "Detect controlled applications when users access them (You will be notified)"
Select "Block the detected application"
Toggle/Enable "Detect controlled applications during scheduled and on-demand scans"
Under "Desktop Messaging" (optional):
Toggle/Enable "Enable Desktop Messaging for Application Control
You can specify a message to share with your end-users on what to do next if an app they want to use is restricted, or feel free to copy my message
With Application Control now set to Block applications based on the list selections, we will now select all applications from our previous audit run we would like to control, or you can use my recommendations below for blocking apps.
Note of Caution: The selections i display below are based on those seen utilized in attack scenarios, and best practices i have utilized in the field. They are not a list that Sophos indicates should be blocked. You should always assess whether your organization should block or allow these applications.
Apps specifically marked in "RED" are high priority to block based on Attacks.
| Category | Application to be Blocked | Control New Apps |
| Application Vulnerabilities | "Select All" |
Yes |
| Archive Tool |
"Select All" except for: 7-zip |
Yes |
| Asset Management Tool | None; or your Choice | Optional / Yes |
| Browser Plug-In |
"Select All" except for Grammarly (optional) |
|
| Business Intelligence Tool |
None; or your Choice |
Optional / Yes |
| CRM Tool |
None; or your Choice |
Optional / Yes |
| Design Tool |
Micromine 2016 |
Optional / Yes |
| Desktop Search Tool |
"Select All" |
Optional / Yes |
| Digital Imaging |
None; or your Choice |
Optional / Yes |
| Distributed Computing | "Select All" | Yes |
| Document Viewer |
Adobe Reader 5 |
Yes |
| Download Manager |
MEGA Downloader |
Yes |
| Email / PIM Client |
"Select All" except apps used by org |
Yes |
| Email Sync Tool |
"Select All" |
Yes |
| Encryption / Steganography tool |
"Select All" except apps used by org |
Yes |
| ERP Software |
None; or your choice |
Yes |
| File Sharing Application |
"Select All" except apps used by org |
Yes |
| FTP Client |
WinSCP |
Yes |
| Game |
"Select All" except Games allowed by org |
Yes |
| Instant Messaging |
"Select All" except IM allowed by org |
Yes |
| Internet Browser | "Select All" except Browsers allowed by org | Yes |
| Jailbreak Software | "Select All" | Yes |
| Mapping Application | "Select All" except apps allowed by org | Yes |
| Media Conversion Tool | "Select All" except apps allowed by org | Yes |
| Media Player | "Select All" except apps allowed by org | Yes |
| Mobile Synchronization | "Select All" except apps allowed by org | Yes |
| Network Monitoring/ Vulnerability Tools |
"Select All" except apps allowed by org | Yes |
| Office Suite | "Select All" except apps allowed by org | Yes |
| Online Storage | MEGAcommand MEGAsync Rclone + any apps not used by org |
Yes |
| Optical Burning Tool | "Select All" except apps allowed by org | Yes |
| Optical Media Emulation | "Select All" except apps allowed by org | Yes |
| Password / License Recovery Tool | BulletsPassView Hashcat L0phtCrack Password Auditor License Crawler Ophcrack Pantsoff Password Revealer "Select All" except apps allowed by org |
Yes |
| Pranking Software | "Select All" | Yes |
| Privacy Tool | "Select All" except apps allowed by org | Yes |
| Programming/Scripting Tool | "Select All" except apps allowed by org | Yes |
| Proxy / VPN Tool | Cyberghost VPN Proxy TOR Proxy Tor based application "Select All" except apps allowed by org |
Yes |
| Remote Management Tool | Anydesk Atera (unless you use it) Quick Assist (unless you use it) Remote Desktop XX (unless you use it) "Select All" except for specific RMM tools used by org |
Yes |
| Runtime Environment | "Select All" except for runtime env used by org | Yes |
| Screen Capture Tool | "Select All" except for apps used by org | Yes |
| Screensaver Application | "Select All" | Yes |
| Security Tool | "Select All" except for sec tools used by org | Yes |
| Software Updater | "Select All" except for apps used by org | Yes |
| System Tool | Atera Networks (unless you use it) Kali Linux for Windows (WSL) KillProcess MS HTML Help Executable "Select All" except for apps used by org |
Yes |
| Telnet Client | "Select All" except for apps used by IT / IT Policy only | Yes |
| Tethered Connection Tool | "Select All" except for apps used by org | Yes |
| Toolbar | "Select All" or your choice | Yes |
| USB Program Launcher | "Select All" or your choice | Yes |
| Virtualization Application | "Select All" except for apps used by org | Yes |
| Voice over IP | "Select All" except for apps used by org | Yes |
Note: This application list can be altered based on the security group/users/computers you apply it to. As an example, you may have a Graphics department and they need access to tools such as Adobe Photoshop, Camtasia, etc. And their Application Policy can be configured not to block those apps, while all other users can be restricted from using these tools.
Once this is in place, you can test your new policies by attempting to execute some of the applications that were either already installed on a system, or if you try to install on the system. You will see that Intercept X Advanced prompts that this application is not permitted, along with your MOTD. In this way, you lock the door on attack patterns used by many threat actors who will attempt to utilize off the shelf tools and technology to impact your operations. Just one more tool in your kit to protect your organization! If you have feedback, please contact your local SE and share with them, we are always happy to hear from you and learn how you are using the solution and if you have an idea that we can use to make the solution that much better for you!
Additional Resources on Application Control
Application Control - SophosLabs - Sophos Community
Endpoint Detection & Response: Block Application - Sophos Techvids
https://docs.sophos.com/central/customer/help/en-us/index.html?contextId=blocked-items
Sophos Central: Application Control Frequently Asked Questions (FAQ)
Interested in setting up Application Filtering at the Firewall level, see:
Application filter - Sophos Firewall
which i highly recommend you do, especially since our firewalls and endpoints communicate App data and can allow you to control new apps discovered on endpoints using a filtering rule. For example, you may have AnyDesk blocked by the Endpoint using Application Control, but you could also block it at the firewall to prevent AnyDesk connections from ever being established from within your network.
Added Microsoft OpenSSH for Windows (SFTP) recommendation under FTP Client category based on suggestions from 2024 August MDR Threatcast
[edited by: Matthew Ritchie at 4:35 PM (GMT -7) on 13 Sep 2024]
