
Disclaimer: This information is provided as-is for the benefit of the Community. Please contact Sophos Professional Services if you require assistance with your specific environment.
Purpose
Microsoft announced a requirement for Azure Code Signing (ACS) requirement: KB5022661—Windows support for the Azure Code Signing program
Sophos announced recent changes to Central to comply with these demands: Central Windows devices: Azure Code Signing changes
This post is to help the Sophos Central audience quickly decipher if they are impacted by the changes.
Prerequisites
You must have XDR enabled in your environment.
The following versions of Windows OS are not supported by Sophos
| Windows | Version |
| 10 | 1507, 1511, 1607, 1703, 1709, 1803, 1809, 1903, 1909, 2004, 19042 (20H2), 19043 (21H1) |
| Server | 1709, 1803, 1809, 1903, 1909 2004, 20H2 |
Full Sophos Retirement Calendar: Sophos Endpoint and Server Protection: Previously supported platforms and operating systems
Unsure of your version? Use the Live Discover Query below.
The following versions of Windows OS** are not impacted by Sophos currently
| Windows | Version (KB where ACS is applied) |
| 7 | KB5006743 (Monthly rollup) - October 12th, 2021 |
| KB5006728 (Security update) - October 12th, 2021 | |
| 8.1 | KB5006714 (Monthly rollup) - October 12th, 2021 |
| KB5006729 (Security update) - October 12th, 2021 | |
| 2008 R2 | KB5006743 (Monthly rollup) - October 12th, 2021 |
| KB5006728 (Security update) - October 12th, 2021 | |
| 2012 | KB5006739 (Monthly rollup) - October 12th, 2021 |
| KB5006732 (Security update) - October 12th, 2021 | |
| 2012 R2 | KB5006714 (Monthly rollup) - October 12th, 2021 |
| KB5006729 (Security update) - October 12th, 2021 |
*Always review the official Sophos KB regarding the ACS changes: Central Windows devices: Azure Code Signing changes
**Requires Sophos Extended Support License
***Long Term Service Channel
The following versions of Windows OS are supported by default in all versions by Sophos
| Windows | Version |
| 10 | 21H2 and 22H2 |
| 11 | All |
The following versions of Windows Server may need audited for support by Sophos
| Windows | Min Version | KB Release Info (GA/LTSC) |
| Server 2022 | 10.0.20348.261 | KB5005619 - September 27th, 2021 |
| Server 2019 | 10.0.17763.2210 | KB5005625 - September 21st, 2021 |
| Server 2016 | 10.0.14393.4704 | KB5006669 - October 12th, 2021 |
Live Discover Query
Many thanks to Jestoni Paglinawan for creating the core of this code to help our community out.
SELECT
CASE
--WinServers
WHEN name LIKE '%Windows Server 2016%' AND build = '14393' THEN 'Windows Server 2016 Build 1607'
WHEN name LIKE '%Windows Server 2019%' AND build = '17763' THEN 'Windows Server 2019 Build 1809'
WHEN name LIKE '%Windows Server 2022%' AND build = '20348' THEN 'Windows Server 2022 Build 21H2'
--Win10
WHEN name LIKE '%Windows 10%' THEN
CASE
WHEN build = '10240' THEN 'Windows 10 Build 1507 - Not Sophos Supported'
WHEN build = '14393' THEN 'Windows 10 Build 1607 - Not Sophos Supported'
WHEN build = '17763' THEN 'Windows 10 Build 1809 - Not Sophos Supported'
WHEN build = '18363' THEN 'Windows 10 Build 1909 - Not Sophos Supported'
WHEN build = '19041' THEN 'Windows 10 Build 2004 - Not Sophos Supported'
WHEN build = '19042' THEN 'Windows 10 Build 20H2 - Not Sophos Supported'
WHEN build = '19043' THEN 'Windows 10 Build 21H1 - Not Sophos Supported'
WHEN build = '19044' THEN 'Windows 10 Build 21H2 - No Patch Needed'
WHEN build = '19045' THEN 'Windows 10 Build 22H2 - No Patch Needed'
END
--Win11
WHEN name LIKE '%Windows 11%' AND build = '22000' THEN 'Windows 11 Build 21H2 - No Patch Needed'
WHEN name LIKE '%Windows 11%' AND build = '22621' THEN 'Windows 11 Build 22H2 - No Patch Needed'
ELSE 'Version NOT Identified ' || build
END AS 'Windows_build'
FROM os_version
Line up your OS against the Central Windows devices: Azure Code Signing changes table and reference the ACS support date.
You can see below that I am supported in my example:
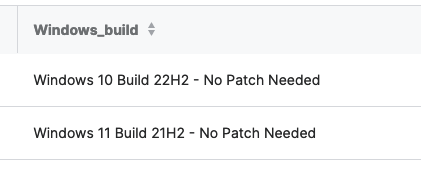
Data Lake Query
SELECT
meta_hostname AS ep_name, hotfix_id, caption, description, installed_by, installed_on
FROM
xdr_data
WHERE
query_name = 'windows_updates_patch'
If you want to verify your machine(s) have updated within the last 90 days, this will do so and report on those entries. ACS has been available since 2021 and hunting for specific KBs will not yield success at scale. Many KB #s change across service channels and builds.
Happy querying!
-jk
removed typo
[edited by: JeramyKopacko at 3:30 PM (GMT -7) on 16 Oct 2023]
