Disclaimer: This information is provided as-is for the benefit of the Community. Please contact Sophos Professional Services if you require assistance with your specific environment.
Index
- Purpose
- Prerequisites
- Query #1 - Live Discover - Check if Embedded Files Are Restricted
- Result #1
- Query #2 - Live Discover - Check if Embedded File Types Are Filtered
- Result #2
- Query #3 - Live Discover - Hunting for OneNote File Types
- Result #3
- Query #4 - Data Lake: Email - Find Emails with Attachments
- Result #4
- Query #5 - Data Lake: Firewall - Find OneNote File Downloads
- Result #5
Purpose
This post is going to cover how the Sophos Central Adaptive Cybersecurity Ecosystem (ACE) empowers an analyst to maximize time spent hunting across their environment. We will focus our attention to a trend in attacks -- using Microsoft OneNote files.
Why? Simple--Microsoft put restrictions on the use of macros in Word and Excel documents. This has made it challenging for adversaries to follow their traditional playbooks. Their solution? Quite simple too -- send the target a OneNote file with embedded files.
This post is the Query Corner's version of "March Madness"
Prerequisites
You must have XDR enabled in your environment. Sophos Email Security or XG/XGS Firewall Series will be required for some of the queries.
DISCLAIMER: Query #1 and #2 rely upon Microsoft 365 Administrative Templates to be successful. These links are provided "as-is" and Sophos does not support them in any capacity.
Query #1 - Live Discover - Check if Embedded Files Are Restricted
NOTE: Please verify you have met the prerequisites.
SELECT name, datetime(mtime,'unixepoch','localtime') as modifiedTime,
CASE
WHEN DATA = '1' THEN 'Enabled'
WHEN DATA = '0' THEN 'Disabled'
ELSE 'key not found'
END AS Status
FROM registry WHERE path LIKE 'HKEY_USERS\%\Software\Policies\Microsoft\office\%\onenote\options\%%'
AND name = 'disableembeddedfiles'
Result #1
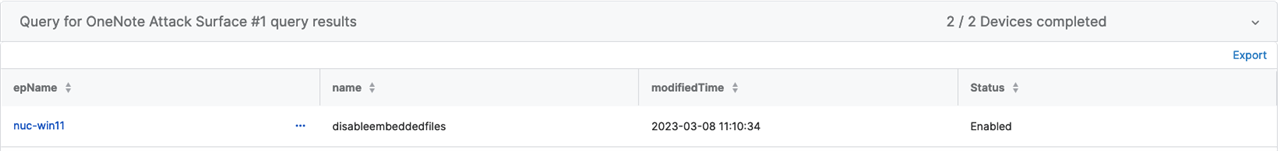
If your agent reports enabled, then OneNote will be restricted from loading ANY embedded file type. If this returns nothing, the Admin Templates are not enabled to the device(s) or this is not configured.
Query #2 - Live Discover - Check if Embedded File Types Are Filtered
NOTE: Please verify you have met the prerequisite.
/*
-- author: jkopacko
+= version 1.0 - 03/06/2023
*/
SELECT name,
REPLACE(data, ';', ' ') AS fileTypes,
datetime(mtime,'unixepoch','localtime') as modifiedTime
FROM registry
WHERE path LIKE 'HKEY_USERS\%\Software\Policies\Microsoft\office\%\onenote\options\embeddedfileopenoptions\%%'
AND name = 'blockedextensions'
Result #2
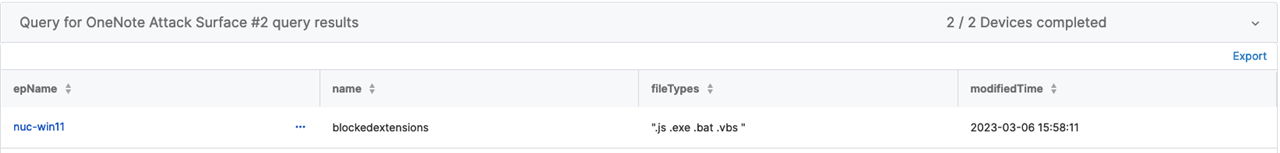
If this returns nothing, the Admin Templates are not enabled to the device(s) or the mitigation is not configured.
The fileTypes column has removed the proper formatting to make it easier for the analyst to read. The Group Policy formatting will look like ".ext1;.ext2;.ext3;.etc" naturally.
Query #3 - Live Discover - Hunting for OneNote File Types
NOTE: This can be resource intensive
/*
-- author: jkopacko
+= Descriptive names: startTime
+= Variable type: Date
+= Value: wildcards work but discouraged due to resource demand
+= version 1.0 - 03/06/2023
*/
SELECT sfp.sha256,
f.path,
f.filename,
datetime(f.atime,'unixepoch','localtime') AS Last_Accessed,
datetime(f.mtime,'unixepoch','localtime') AS Last_Modified,
datetime(f.ctime,'unixepoch','localtime') AS Creation_Time
FROM file f
LEFT JOIN sophos_file_properties sfp
ON f.path = sfp.path
WHERE f.filename LIKE '%.one'
AND (f.path LIKE 'C:\Users\Public\%%'
OR f.path LIKE 'C:\Users\%\Downloads\%'
OR f.path LIKE 'C:\Users\%\Documents\%'
OR f.path LIKE 'C:\Users\%\Desktop\%'
OR f.path LIKE 'C:\Users\%\Music\%%'
OR f.path LIKE 'C:\Users\%\Pictures\%%'
OR f.path LIKE 'C:\Users\%\AppData\Local\Temp\%'
OR f.path LIKE 'C:\Users\%\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\%')
--Can add more search locations but will task the service further
/*
OR f.path LIKE 'C:\ProgramData\%'
OR f.path LIKE 'C:\Perflogs\%'
OR f.path LIKE 'C:\Intel\%'
OR f.path LIKE 'C:\Temp\%'
OR f.path LIKE 'C:\Windows\%'
OR f.path LIKE 'C:\Windows\Temp\%'
OR f.path LIKE 'C:\Windows\System32\%'
OR f.path LIKE 'C:\Windows\SysWOW64\%')
*/
AND datetime(f.ctime,'unixepoch','localtime') > $$startTime$$
NOTE: Later versions of this query will be modified for gathering data sets in intervals of 6-8 hours to allow for longer hunting times
Result #3
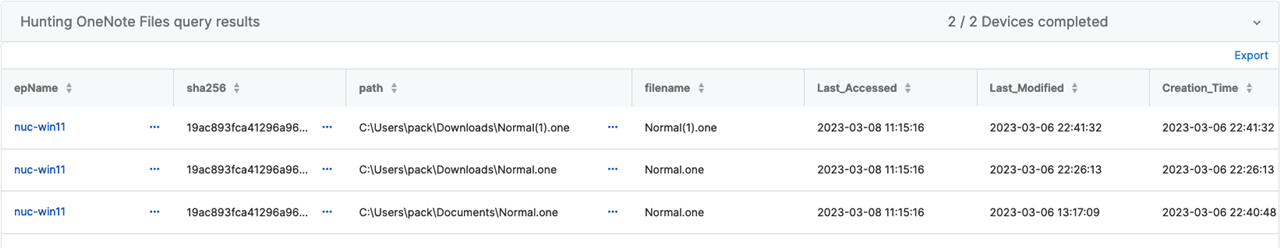
NOTE: We could use this query to hunt for a specific SHA256 discovery if we received Threat Intel on an IoC/IoA.
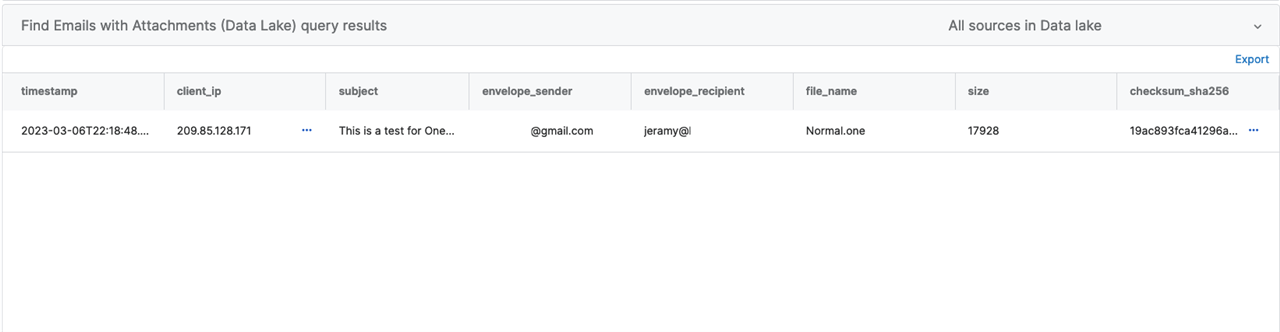
Query #4 - Data Lake: Email - Find Emails with Attachments
Good news! This is already available in your Dashboard Today.
Navigate to Live Discover > Data Lake > Email > Find Emails with Attachments
Enter the query as shown below:
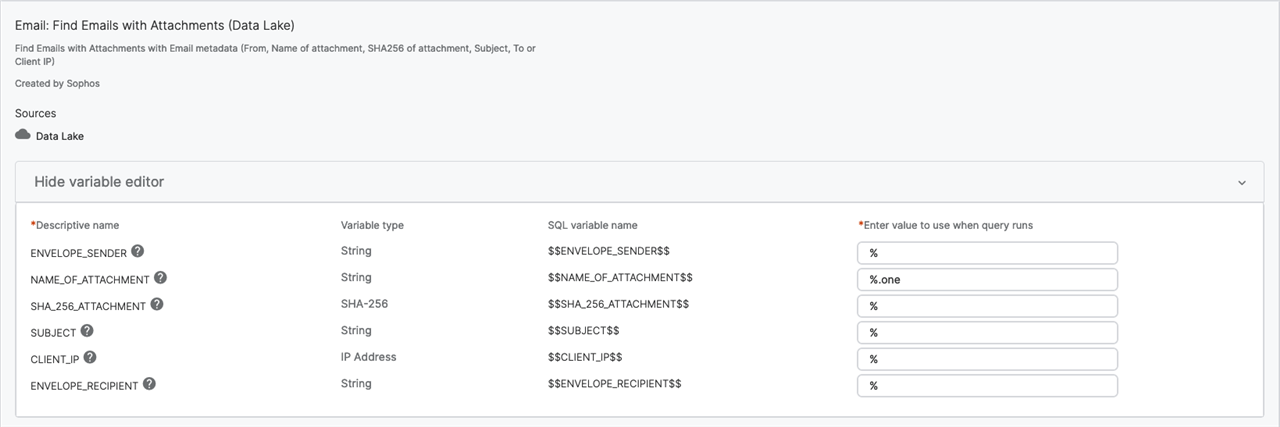
You can use wildcards within the values of the variables. Here I am expanding this to search of ANY (%) attachment name with the OneNote file extension (.one).
Result #4
Query #5 - Data Lake: Firewall - Find OneNote File Downloads
NOTE: I am using TLS decryption in my Lab environment
SELECT timestamp, log_type, log_component, log_subtype, severity, user_name, src_ip, dst_ip, dst_port, app_name, app_category, app_risk, url, download_file_name, download_file_type FROM xgfw_data WHERE download_file_name LIKE '%.one'
Result #5
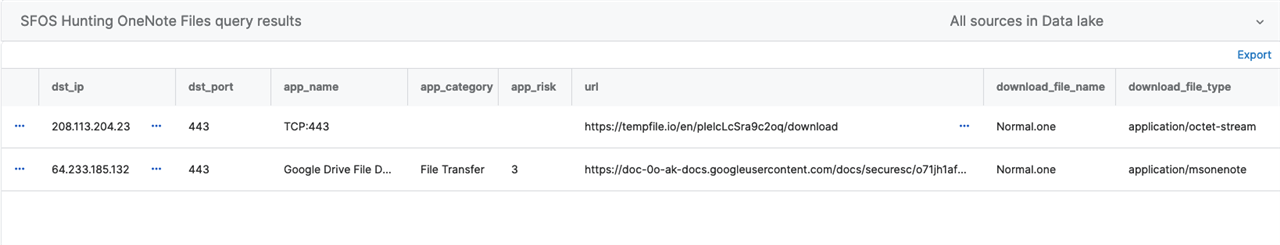
NOTE: this screenshot is missing several categories, but the destination info is what we really care about, right? ;)
Happy querying!
-jk
Added Disclaimer
[edited by: GlennSen at 4:02 PM (GMT -7) on 5 Apr 2023]