Disclaimer: This information is provided as-is for the benefit of the Community. Please contact Sophos Professional Services if you require assistance with your specific environment.
Table of Contents
Overview:
The latest release of Sophos Protection for Linux, provides a new update mechanism with improved communications. This mechanism helps reduce bandwidth consumption for downloads. We have seen some instances where customers running SPL on unsupported platforms are affected by issues when updating. This is a result of the capability leveraging explicit Server certificate paths. The Linux server being used in this case is not one of the Supported or tested Linux platforms that can be found in the release notes, and as such, it's likely that it uses a Certificate path that will not have been included in the update.
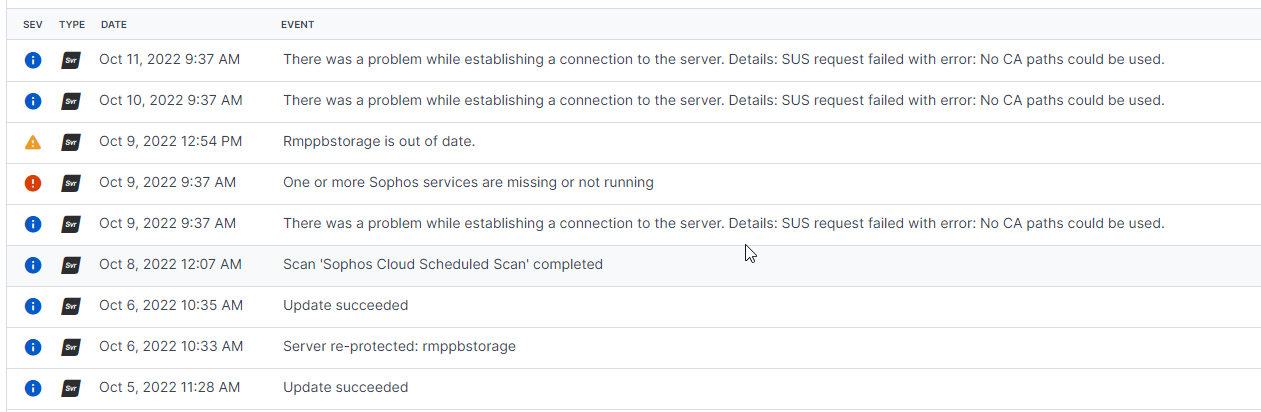
Servers impacted by this issue will see the following events in Central:
Reference to the current supported list of platforms for SPL can found here by navigating to ‘System requirements' under 'Sophos Protection for Linux' Agent.
Applies to the following Sophos products and versions:
-
Sophos Protection for Linux
What to do:
The following workaround has been seen to resolve the issue with updating for some unsupported platforms. This, in no way, adds any additional support but does enable some unsupported Linux platforms to continue to receive updates and some level of functionality from the Sophos Protection for Linux product.
The workaround here takes SLES 12 as an example and creates a symbolic link between the Linux platform's certificate repository and a typical location found on a supported Linux platform:
-
mkdir -p /etc/pki/tls/certs/
-
ln -s /etc/ssl/ca-bundle.pem /etc/pki/tls/certs/ca-bundle.crt
The above commands will need to be adjusted appropriately for different Linux platforms and versions.
Updated disclaimer
[edited by: Qoosh at 8:07 PM (GMT -7) on 31 Mar 2023]
