Disclaimer: This information is provided as-is for the benefit of the Community. Please contact Sophos Professional Services if you require assistance with your specific environment.
Overview
This article provides a high-level overview of deploying Sophos Endpoint Agent to a Windows environment using Ansible. It also includes an example YML playbook to install Sophos. The steps below are provided with the assumption that the following infrastructure is present in the environment.
- Ansible master server
Deployment preparation:
To start deployment, we’ll need to enter the target IPs by editing the host file:
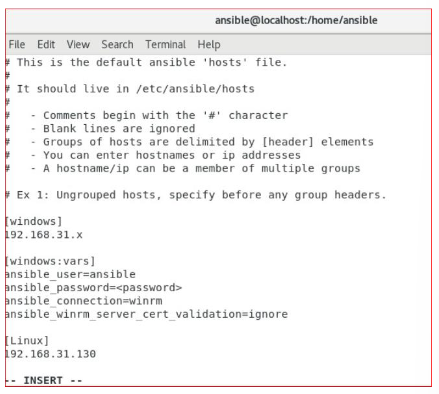
vi / etc / ansible / hosts
# This is the default ansible 'hosts' file.
#
# It should live in /etc/ansible/hosts
#
# - Comments begin with the '#" character
# - Blank lines are ignored
# - Groups of hosts are delimited by [header] elements
# - You can enter hostnames or ip addresses
# - A hostname/ip can be a member of multiple groups
# Ex 1: Ungrouped hosts, specify before any group headers.
[windows]
192.168.21.x
[windows:wars]
ansible_user=ansible
ansible_password=<password>
ansible_connection=winrm
ansible_winrm_server_cert_validation=ignore
[Linux]
192.168.31.130
-- INSERT --
Note: [windows] and [linux] are the host groups, under that, we can put our target IPs. We’ll also need to make our inventory functional for which we need to change the config file:
vi /etc/ansible/ansible.cfg
Uncomment the below lines:
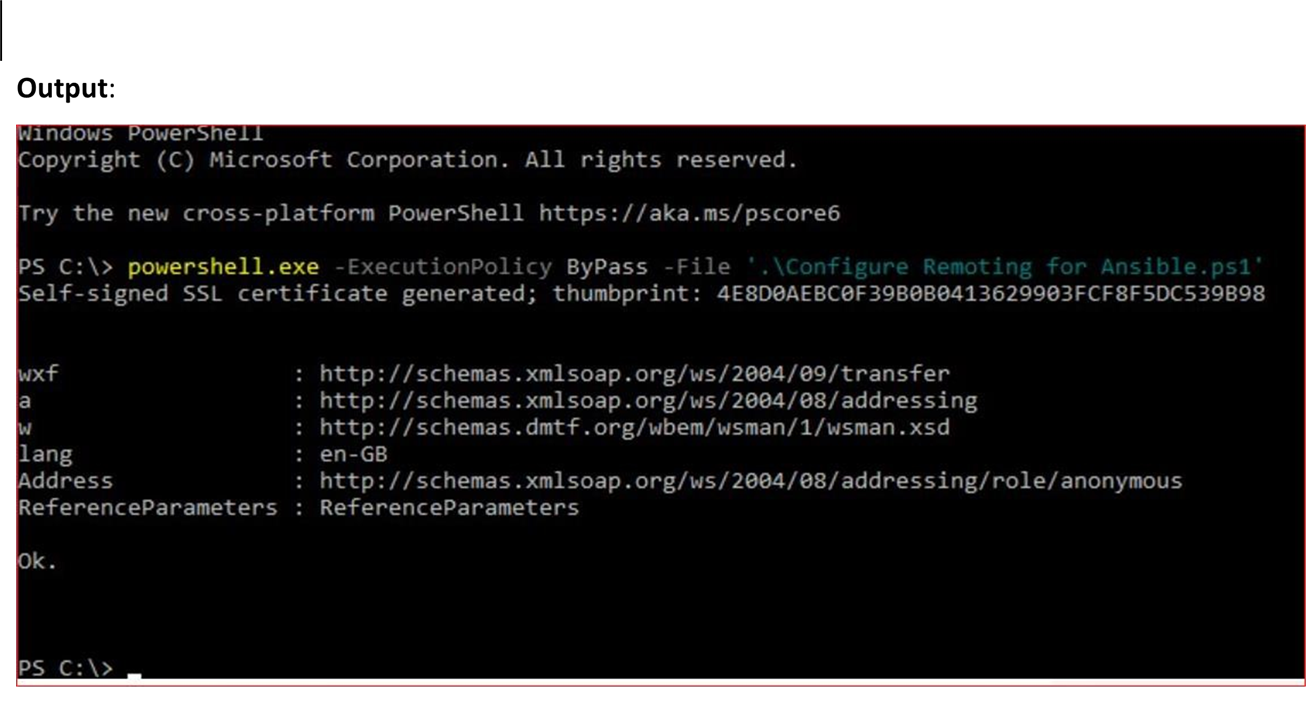
inventory Host Requirements For Ansible to communicate to a Windows host and use Windows modules, the following requirements must meet on the Windows host: 8.1, and 10, and server OSs including Windows Server 2012, 2012 R2, 2016, 2019, and 2022. Setting Up WinRM: There’s a Configure Remoting for Ansible script you can run on the remote Windows device (in a PowerShell console as an Admin) to turn on WinRM. To set up an HTTPS listener, build a self-signed cert and run PowerShell commands, just run the script like in the example below. Script to download: Configure Remoting for Ansible Move the script to the current directory, and run it via Powershell Powershell.exe -ExecutionPolicy ByPass -File '.\Configure Remoting for Ansible.ps1'
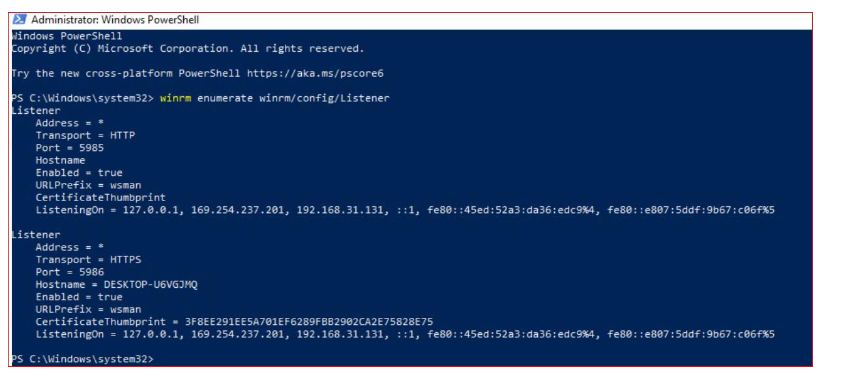
WinRM Listener: The WinRM services listen for requests on one or more ports. Each of these ports must have a listener created and configured. To view the current listeners that are running on the WinRM service, run the following command on the windows host device: winrm enumerate winrm/config/Listener Output: Now to test the connection we must ping the windows host from our ansible node. To achieve that run the below command: ansible windows -m win_ping
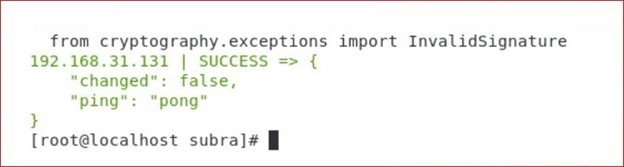
Output: Now we are all set, windows machine is now communicating to ansible node. Next is to write a playbook for installing Sophos, written in YAML code. Deploying Sophos Agent: To begin deploying the Sophos Agent, we’ll be creating an Ansible playbook that has an extension. yml. vi windows.yml (you can give any file name) You can write your own playbook now. Playbook for Sophos installation: --- #sophos Install - name: Install Sophos To run the playbook, need to run the below command: Ansible-playbook windows.yml
Output:
Sophos Endpoint Agent Deployment is now complete.
- hosts: windows
user: ansible
become: false
connection: winrm
tasks:
- name: Download Sophos
win_get_url:
url: "Sophos endpoint Download link"
dest: C:\Windows\Temp\SophosSetup.exe
win_package:
path: C:\Windows\Temp\SophosSetup.exe
product_id: 'Sophos'
arguments: --quiet
state: present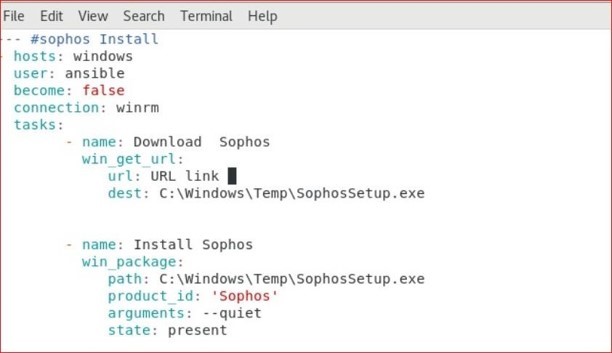

Updated disclaimer
[edited by: Qoosh at 9:31 PM (GMT -7) on 31 Mar 2023]

