Disclaimer: This information is provided as-is for the benefit of the Community. Please contact Sophos Professional Services if you require assistance with your specific environment.
______________________________________________________________________________________________________________________________
Overview
This article shows you the Windows registry keys to confirm if the Sophos components are off when we disable them from the endpoint UI.
Applies to the following Sophos product(s) and version(s)
Sophos Central Endpoint and Server.
Introduction
When you are performing component isolation via the local endpoint UI for issues you are facing with Sophos endpoint, have you ever wondered where you can confirm if the components are indeed set to disabled? The following config keys in the Windows registry can help you to identify whether the components are off before you run any test.
Information
Component isolation is often required for Central administrator to perform during troubleshooting if they do not know which Sophos component is causing the issue. To find out more about how you should perform the component isolation, please refer to Sophos KB - Sophos Central Endpoint: Basic troubleshooting.
After STiNG 2.0 upgrade, most of the Sophos endpoint config keys can be found in the Windows registry. Following are the correspondent keys to help you troubleshoot.
Correspondent registry keys for the endpoint UI switches and related policies
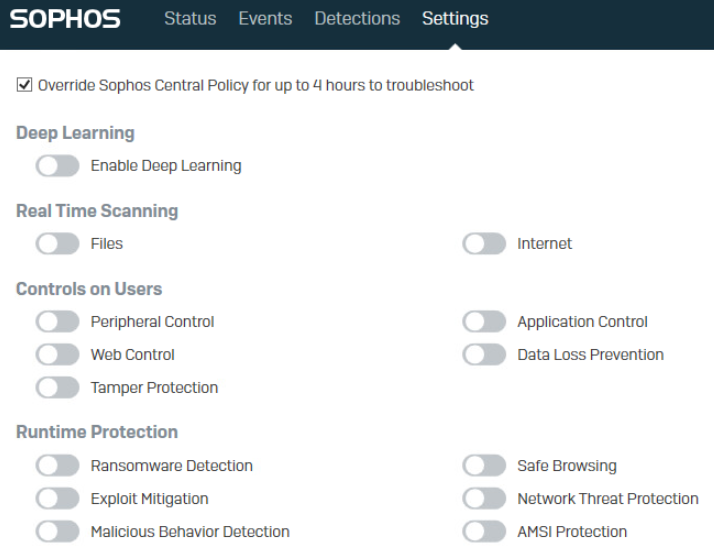
- Real Time Scanning for File
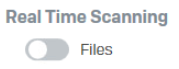
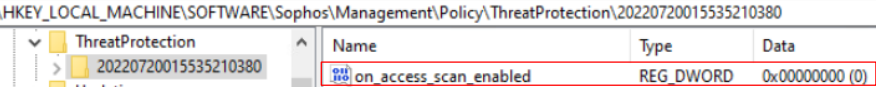
Reg key: HKEY_LOCAL_MACHINE\SOFTWARE\Sophos\Management\Policy\ThreatProtection\Number folder
The "on_access_scan_enabled" key value should change from 1 to 0 when it is disabled
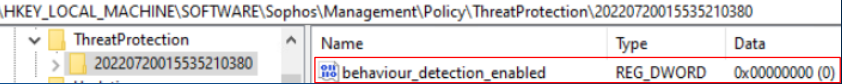
- Malicious Behavior Detection

Reg key: HKEY_LOCAL_MACHINE\SOFTWARE\Sophos\Management\Policy\ThreatProtection\Number folder
The "behavior_detection_enabled" key value should change from 1 to 0 when it is disabled
- "Enable real-time scanning for Remote files" from Threat Protection policy
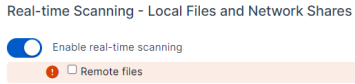
Reg key: HKEY_LOCAL_MACHINE\SOFTWARE\Sophos\Management\Policy\ThreatProtection\Number folder
The "on_access_exclude_remote_file" key value should change from 0 to 1 when it is disabled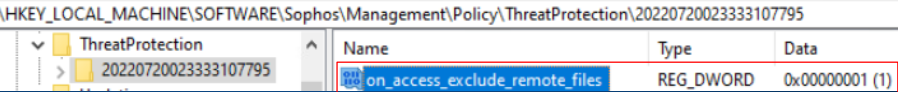
- Deep Learning / Machine Learning
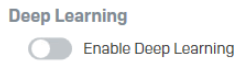
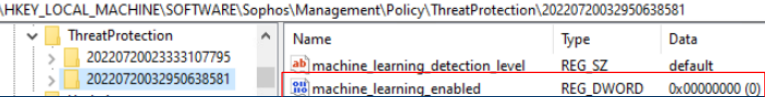
Reg key: HKEY_LOCAL_MACHINE\SOFTWARE\Sophos\Management\Policy\ThreatProtection\Number folder
The "machine_learning_enabled" key value should change from 1 to 0 when it is disabled
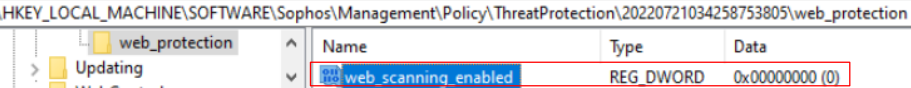
- Real Time Scanning for Internet / Web Protection
![]()
Reg key: HKEY_LOCAL_MACHINE\\SOFTWARE\Sophos\Management\Policy\ThreatProtection\Number folder\web_protection
The "web_scanning_enabled" key value should change from 1 to 0 when it is disabled
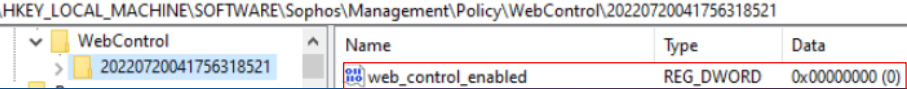
- Web Control
![]()
Reg key: HKEY_LOCAL_MACHINE\SOFTWARE\Sophos\Management\Policy\WebControl\Number folder
The "web_control_enabled" key value should change from 1 to 0 when it is disabled
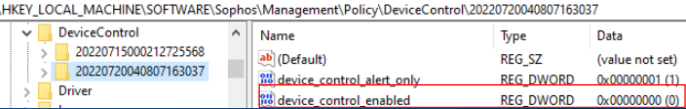
- Peripheral Control / Device Control
![]()
Reg key: HKEY_LOCAL_MACHINE\SOFTWARE\Sophos\Management\Policy\DeviceControl\Number folder
The "device_control_enabled" key value should change from 1 to 0 when it is disabled
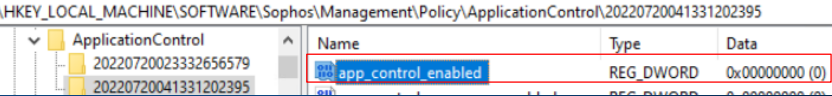
- Application Control
![]()
Reg key: HKEY_LOCAL_MACHINE\SOFTWARE\Sophos\Management\Policy\ApplicationControl\Number folder
The "app_control_enabled" key value should change from 1 to 0 when it is disabled
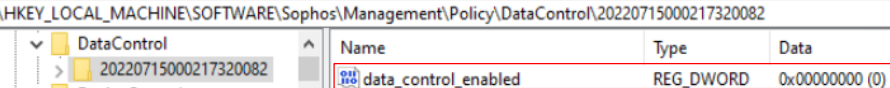
- Data Loss Prevention / Data Control
![]()
Reg key: HKEY_LOCAL_MACHINE\SOFTWARE\Sophos\Management\Policy\DataControl\Number folder
The "data_control_enabled" key value should change from 1 to 0 when it is disabled
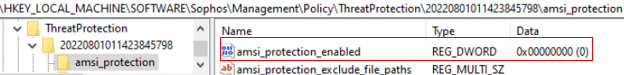
- AMSI Protection
![]()
Reg key: HKEY_LOCAL_MACHINE\SOFTWARE\Sophos\Management\Policy\ThreatProtection\Number folder\amsi_protection
The "amsi_protection_enabled" key value should change from 1 to 0 when it is disabled
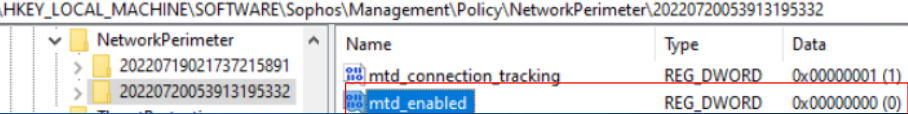
- Network Threat Protection
![]()
Reg key: HKEY_LOCAL_MACHINE\SOFTWARE\Sophos\Management\Policy\NetworkPerimeter\Number folder
The "mtd_enabled" key value should change from 1 to 0 when it is disabled
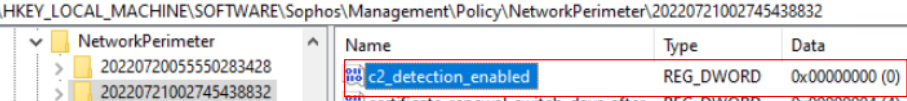
- "C2 Detection" from Threat Protection policy
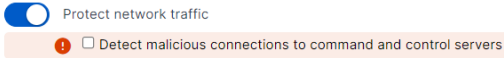
Reg key: HKEY_LOCAL_MACHINE\SOFTWARE\Sophos\Management\Policy\NetworkPerimeter\Number folder
The "c2_detection_enabled" key value should change from 1 to 0 when it is disabled
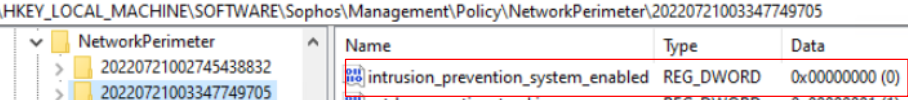
- "Intrusion Prevention System (IPS)" from Threat Protection policy
Reg key: HKEY_LOCAL_MACHINE\SOFTWARE\Sophos\Management\Policy\NetworkPerimeter\Number folder
The "intrusion_prevention_system_enabled" key value should change from 1 to 0 when it is disabled
Intercept X related functions - All of the intercept X function keys can be seen in the key folder below by default, please refer back to the screenshot when you need to compare the keys before and after you disable an intercept X component.
Reg key: HKEY_LOCAL_MACHINE\SOFTWARE\HitmanPro.Alert
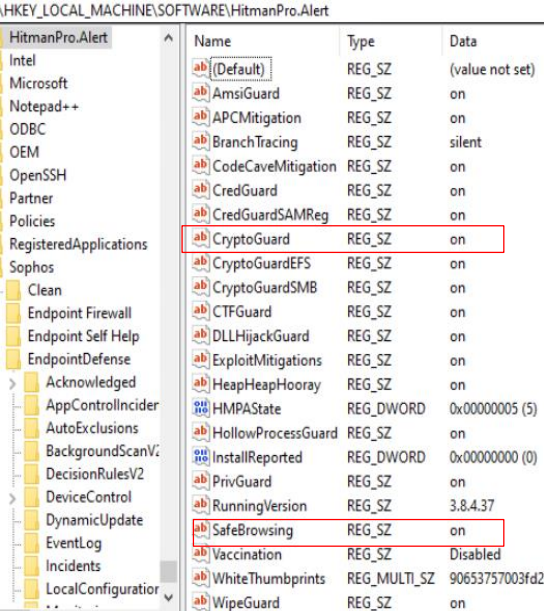
- Ransomware Detection
![]()
When Ransomware Detection is turned off from the UI, rather the value of the "CryptoGuard" key changing from on to off, the key will be removed instead. The resulting key folder shown below.
The CryptoGuard key is no longer in the key folder.
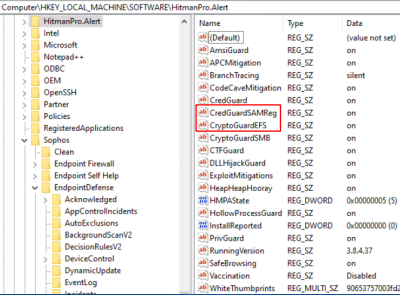
- Exploit Mitigation
![]()
When "Exploit Mitigation" is turned off from the UI, all of the "Exploit Mitigation" related function keys will be removed from the key folder. The resulting key folder can be seen below.
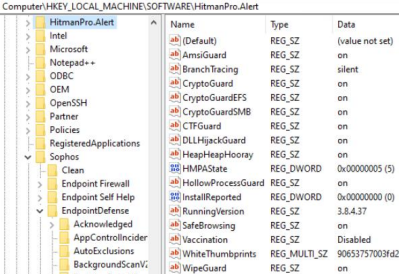
If you need to isolate the "Exploit Mitigation" subfunctions further, you have to do so from the Threat Protection policy and check back here to see if the particular subfunction key has been removed from the key folder to confirm its disablement.
- Safe Browsing
![]()
When "Safe Browsing" is turned off from the UI, the "SafeBrowsing" key will be removed from the key folder. The resulting key folder can be seen below. You can compare this to the key folder shown above for the difference.
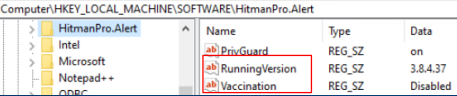
Hopefully, you’ll find this article helpful for your troubleshooting. Have a lovely day.
Updated disclaimer
[edited by: Qoosh at 9:31 PM (GMT -7) on 31 Mar 2023]

