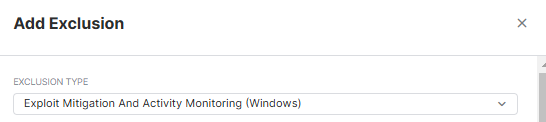
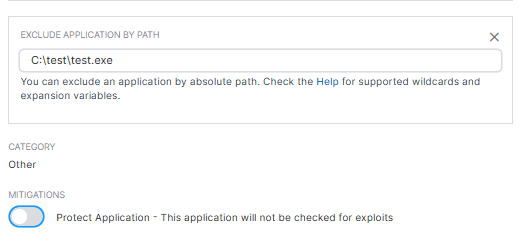
we have parallels RAS that allow us to login to VDIs. I have setup SSO on parallels it allows me to log in with my user name and password then once i select the vdi it tells me i have to be part of RDP group. I got in touch with Parallels and they suggested that iuninstall sophos endpoint and it worked. they sent me what to exclude, i did apply the exclusion and made sure that the newly created vdis get the policy yet it is still not working. The other weird behavior is that when i uninstall endpoint reinstall it again single sign on remains working. I tried to turn off all the settings on the endpoint to determine what is blocking the sso it still doesn't allow me to log in. I have always to uninstall sophos to make it work. How can i determine what is blocking the sso? any tools or cmd to check what is happening in the background? why when uninstalling the endpoint and reinstalling it, it works?
Edit Tags
[edited by: GlennSen at 9:29 AM (GMT -8) on 8 Jan 2025]