I have identified a problem with Sophos Encryption, and I need to do a validation before bringing it up with Support as an issue. I can run a powershell command (as seen below) to find the encryption status however it doesn't tell me that it was Sophos which encrypted it. Is there a command or registry key I can pull to confirm that it is actually Sophos Encryption that encrypted the drive or that it is at least activated?
I cannot depend on Sophos Central if you have guessed it because the problem I'm facing is that Sophos Central shows no indication of errors or fault, but it is not encrypted properly, and I can confirm because these computers do not get the pin request and boot authentication request and yet Sophos Central has no errors.
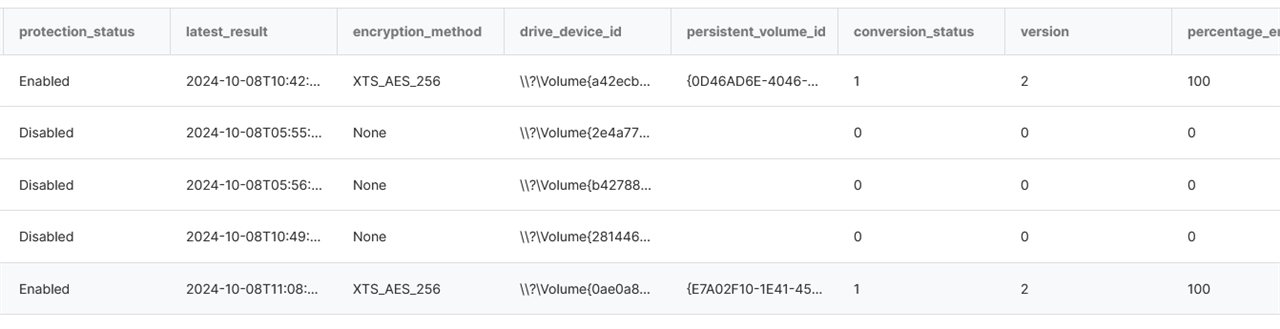
Command used: manage-bde -status c:
Good Result
Volume C: []
[OS Volume]
Size: 476.07 GB
BitLocker Version: 2.0
Conversion Status: Fully Encrypted
Percentage Encrypted: 100.0%
Encryption Method: XTS-AES 256
Protection Status: Protection On
Lock Status: Unlocked
Identification Field: Unknown
Key Protectors:
TPM And PIN
Numerical Password
Bad Result
Volume C: [OS]
[OS Volume]
Size: 464.29 GB
BitLocker Version: 2.0
Conversion Status: Used Space Only Encrypted
Percentage Encrypted: 100.0%
Encryption Method: XTS-AES 128
Protection Status: Protection Off
Lock Status: Unlocked
Identification Field: Unknown
Key Protectors: None Found
What I want to do is run a PowerShell script across all endpoints, and if I see that Sophos Encrypted the drive but it comes up with something like Used Space Only (which is wrong in the policy) or it uses AES128 then it should report back as a problem. I have no problem writing this, but without confirming that the endpoint has Sophos Encryption and that it actually activated on the computer itself I can't go any further.
Any help is greatly appreciated.
Added Tags
[edited by: GlennSen at 7:51 AM (GMT -8) on 4 Nov 2024]