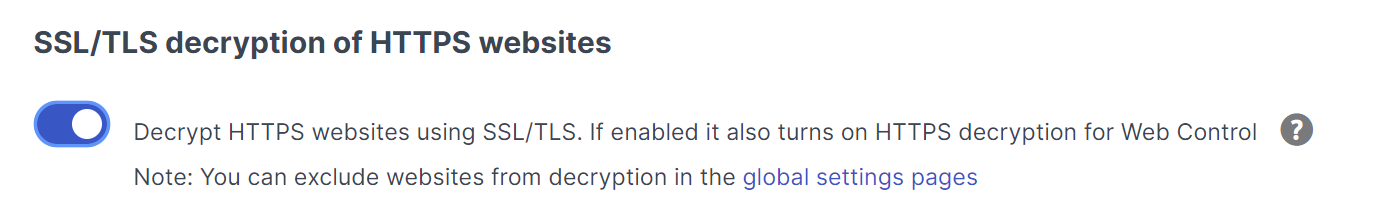
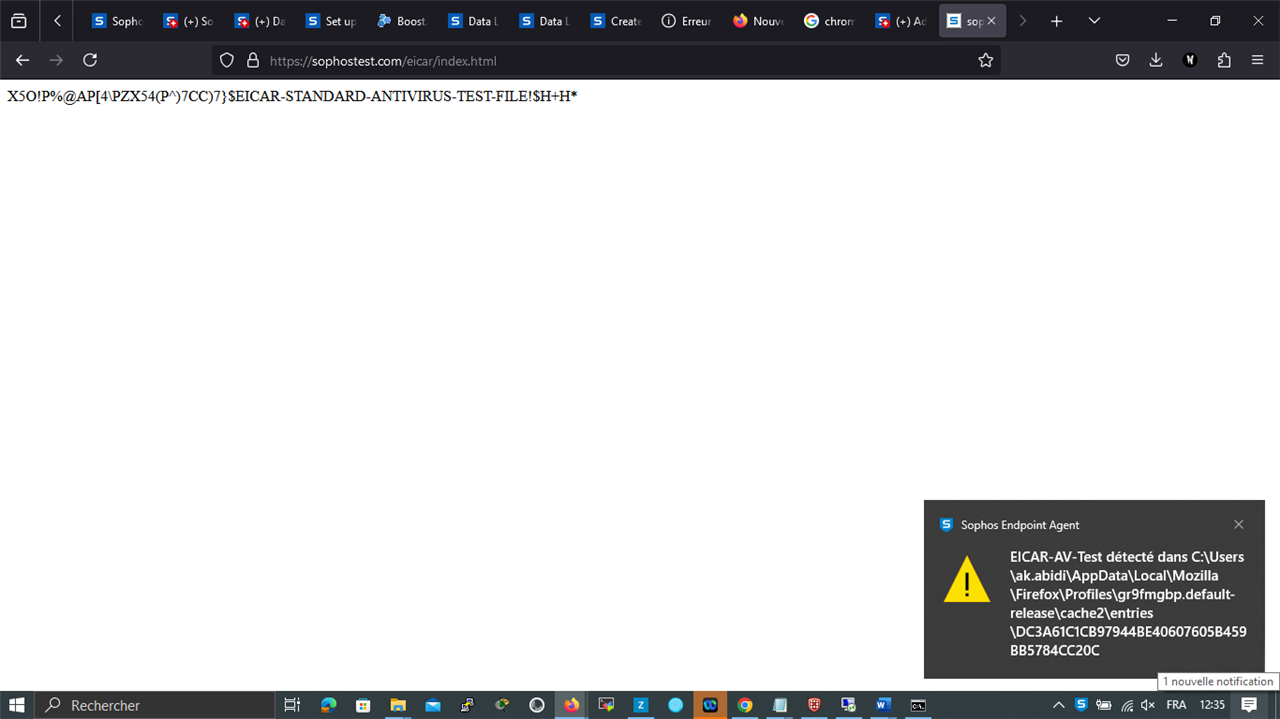
(Browser-Specific): Threat Protection policies only detects malwares in Firefox when accessing the eicar website but failed to detect it using Chrome.
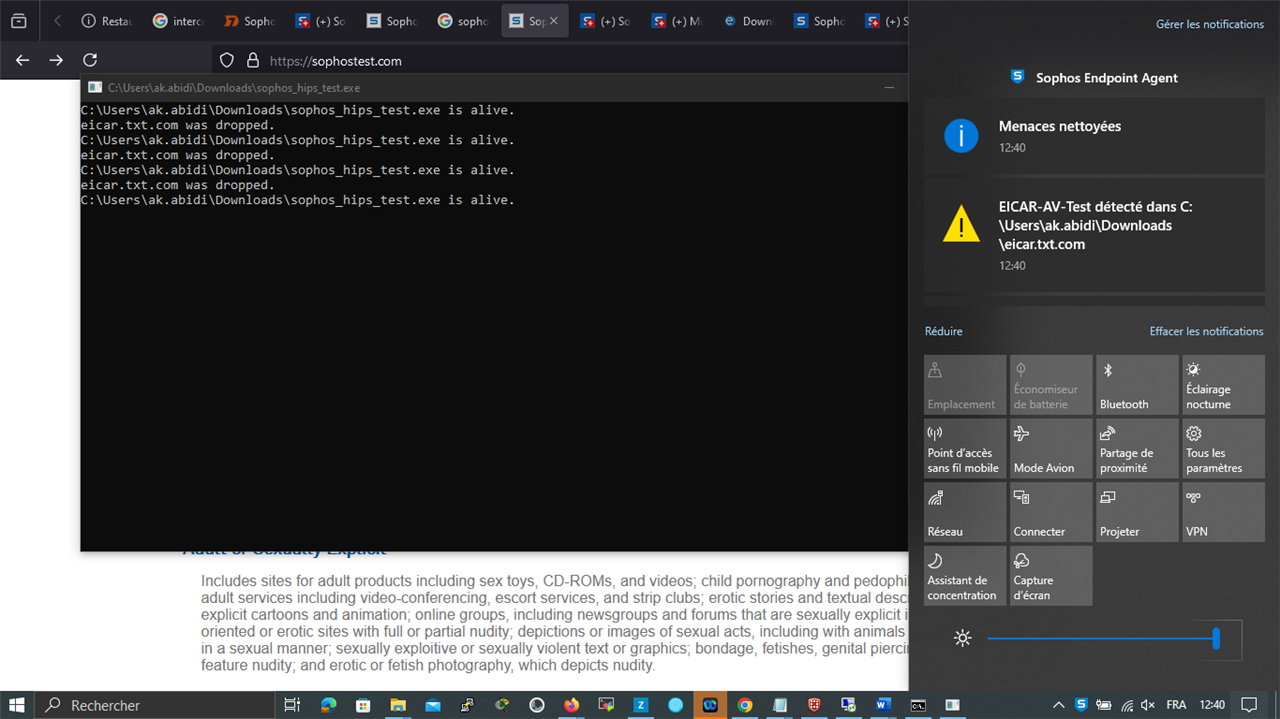
also, what is this behavior, it keeps detecting the malware, cleans it, but never kills the sophos_hips_test.exe ?
This thread was automatically locked due to age.