hi,
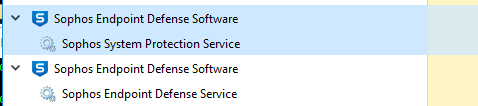
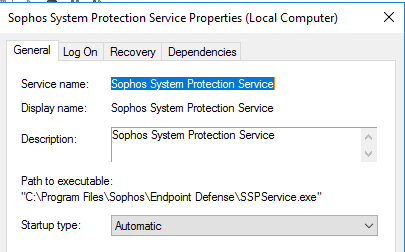
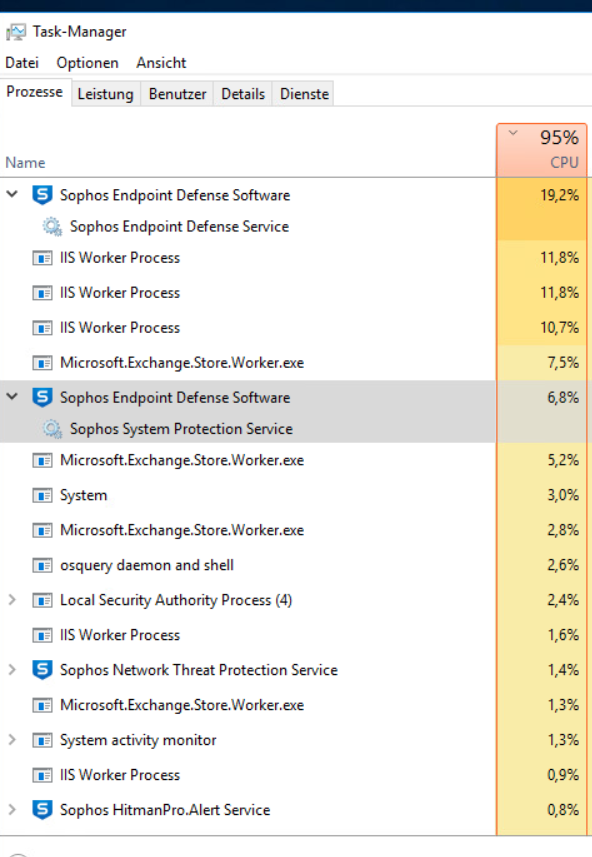
since friday we have high cpu with the sophos endpoint defense software process.
windows server 2016
sophos central server core version: 2024.2.2.1
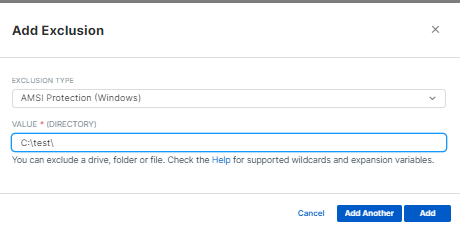
after disabling all the features the cpu is back to normal..
any ideas?
This thread was automatically locked due to age.