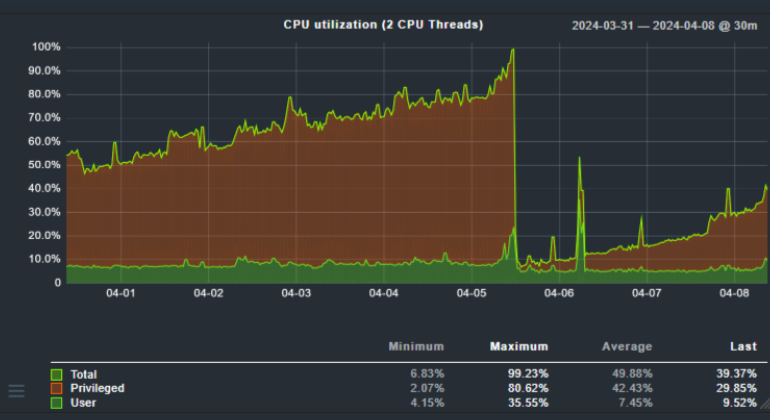
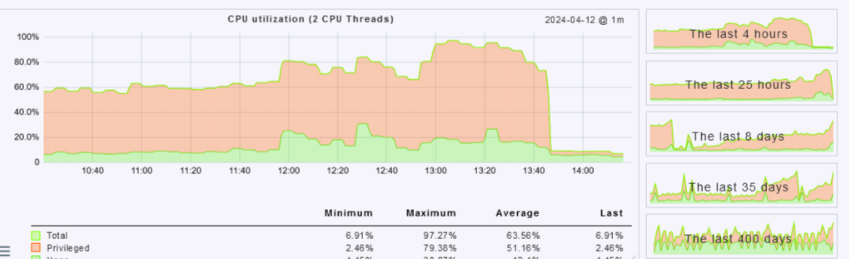
On some Servers behind Sophos UTM firewall, which is not capable of wildcard DNS hosts, we noticed increasing CPU load over the last days. Up to 100% today and the server became sluggish.
The CPU load was rising since March 28th - where we rebooted the server as requested by Sophos Endpoint pending reboot after component update.
Core Agent 2024.1.0.51
Sophos Intercept X 2023.2.1.6
Managed Detection and Response 2023.2.0.3
XDR 2024.1.0.51
Rising CPU load:
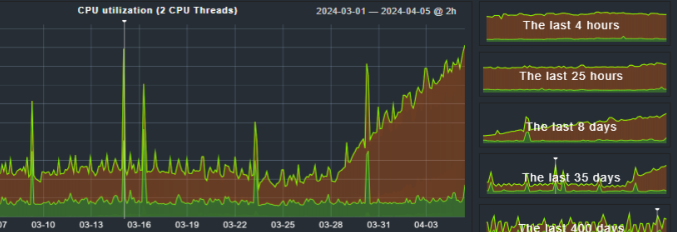
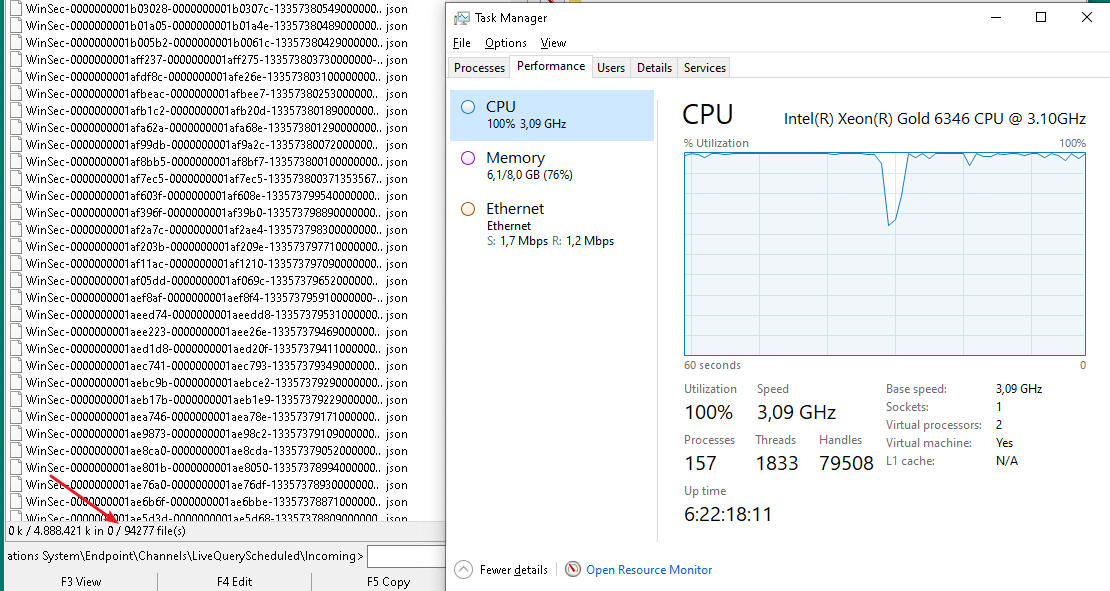
CPU load caused by MCS client:
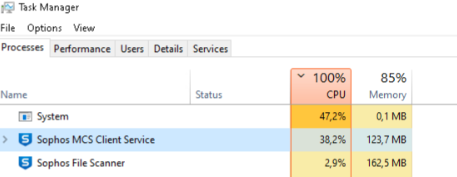
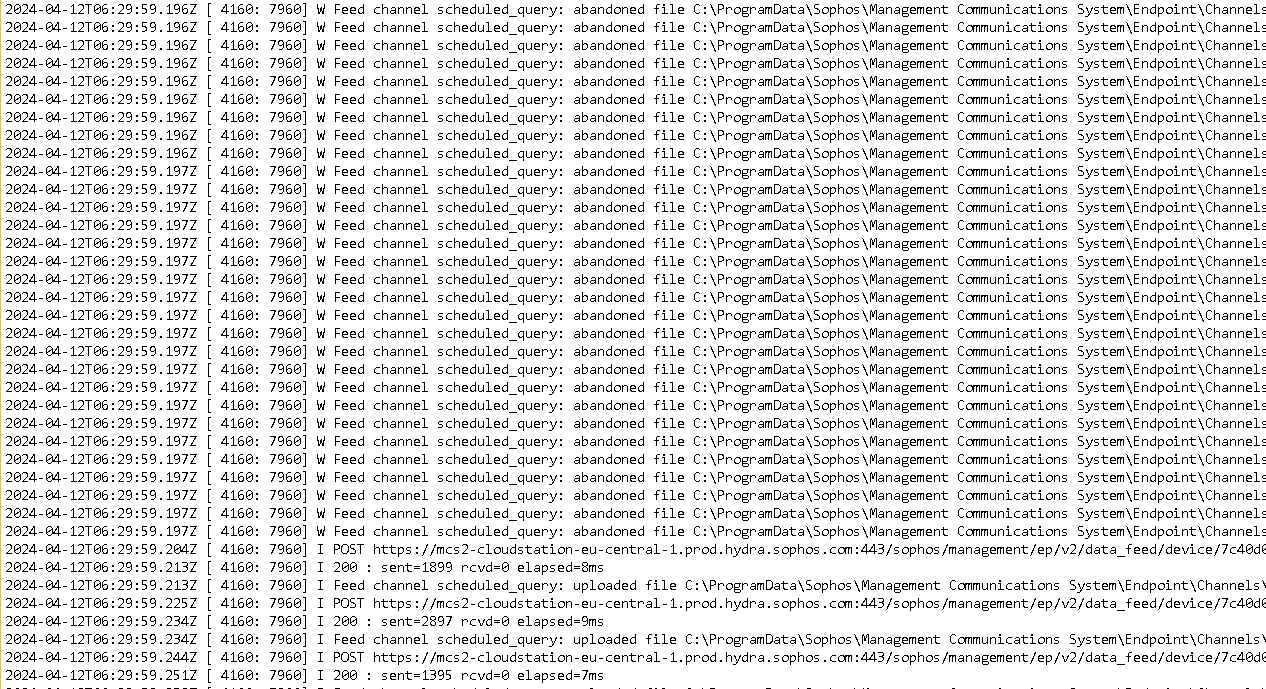
We could find from the logs that the MCS client was trying to push json files to datalake. An ammount of over 100k files in
C:\ProgramData\Sophos\Management Communications System\Endpoint\Channels\LiveQueryScheduled\Incoming\
Filenames like scheduled-20240322091806838.json
The files could not be pushed to the push servers and were aging out. The huge ammount of files that MCS was trying to upload caused the increasing CPU load.
2024-04-05T09:57:22.286Z [ 3032: 4840] W Feed channel scheduled_query: too old file C:\ProgramData\Sophos\Management Communications System\Endpoint\Channels\LiveQueryScheduled\Incoming\scheduled-20240322095704005.json
2024-04-05T09:57:52.496Z [ 3032: 4840] W Feed channel scheduled_query: too old file C:\ProgramData\Sophos\Management Communications System\Endpoint\Channels\LiveQueryScheduled\Incoming\scheduled-20240322095735944.json
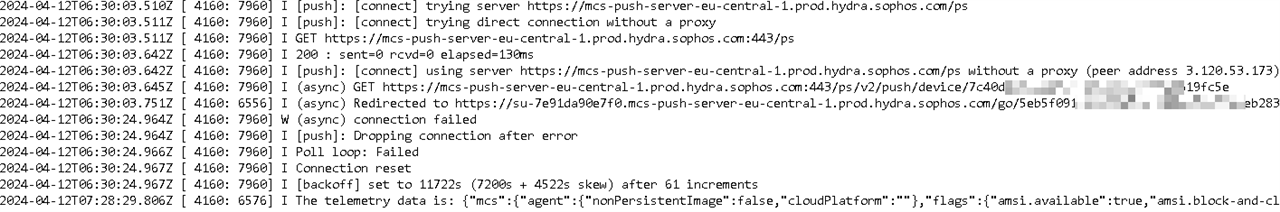
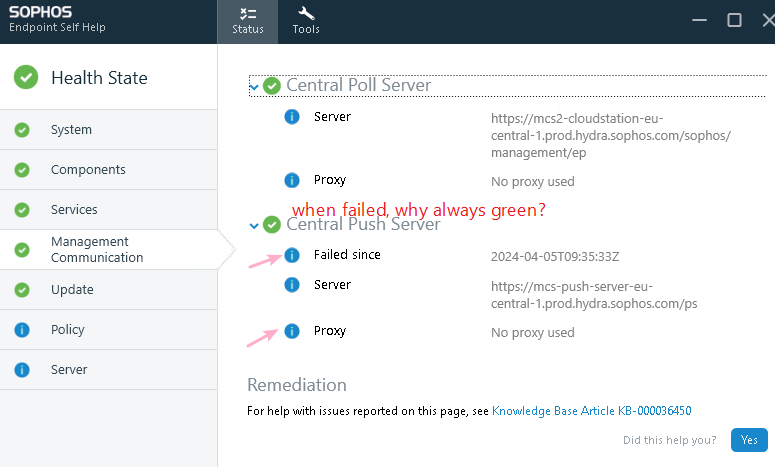
We can see from the MCS logs it is trying to reach
mcs-push-server-eu-central-1.prod.hydra.sophos.com
but is then redirected to su-7f291a12c603 - one of the hundreds of servers used for loadbalancing.
2024-04-05T09:35:12.403Z [ 4160: 7960] I [push]: [connect] using server mcs-push-server-eu-central-1.prod.hydra.sophos.com/ps without a proxy (peer address 18.184.143.209)
2024-04-05T09:35:12.406Z [ 4160: 7960] I (async) GET mcs-push-server-eu-central-1.prod.hydra.sophos.com:443/.../xxxxxxxxx-c179-4ec3-bcea-7b7dd619fc5e
2024-04-05T09:35:12.429Z [ 4160: 6880] I (async) Redirected to su-7f291a12c603.mcs-push-server-eu-central-1.prod.hydra.sophos.com/.../xxxxxxxxx-9b47-4f95-a250-bfef4036f015
2024-04-05T09:35:33.448Z [ 4160: 7960] W (async) connection failed
2024-04-05T09:35:33.448Z [ 4160: 7960] I [push]: Dropping connection after error
2024-04-05T09:35:33.450Z [ 4160: 7960] I Poll loop: Failed
2024-04-05T09:35:33.452Z [ 4160: 7960] I Connection reset
On the firewall we allow 443 to DNS group mcs-push-server-eu-central-1.prod.hydra.sophos.com - that is the only thing we can do at an UTM.
When the Endpoint then decides to directly contact the sophos Servers with their su-******* name, it fails, of course.
Is there anything we could do except allowing 443 for the Sophos Endpoints to any at the UTM?
I can see on the agent, there is some proxy setting available, how can we use and configure that?
This thread was automatically locked due to age.