Users received legitimate word files via Outlook.
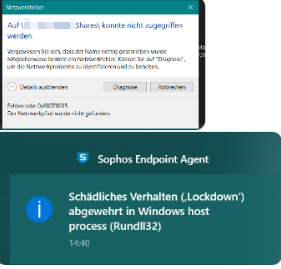
When received they opened and edited the attachment directly (explains the AppData\Local\Temp\NDFCE93.tmp filename) an then while then saving the file on the Windows Server SMB file share, their Sophos EP creates a lockdown event for C:\Windows\SysWOW64\rundll32.exe
This is happenign since today for a few users that have not changes their way of work. I have asked them to do exaclty the same with the same mail attachment after a reboot and it could not reproduce the issue.
Licensed Assigned Version
Core Agent 2024.1.0.46
Sophos Intercept X 2023.2.1.6
Device Encryption 2023.2.0.7
Managed Detection and Response 2023.2.0.3
XDR 2024.1.0.46
Is this a new and known issue?
Details like:
Detection type Lockdown Application PathC:\Windows\SysWOW64\rundll32.exe Version10 PID14420 Detection IDae580bbd997cec514fae8b611df72ae52e03e4017e39bce46bc3f06f4c1b900a Mitigation Lockdown Policy LockdownNewFile Timestamp 2024-03-26T13:40:23 Platform 10.0.19045/x64 v3 06_8e- PID 14420 WoW x86 Enabled 08FDAE3A40000004 Silent 0080800000000000 Application C:\Windows\SysWOW64\rundll32.exe Created 2023-11-20T14:12:24 Modified 2023-11-20T14:12:24 Description Windows host process (Rundll32) 10 Filename C:\WINDOWS\system32\msdt.exe Lockdown type: LolBin Command line: -skip TRUE -path "C:\WINDOWS\diagnostics\system\networking" -af "C:\Users\XXXXX~1\AppData\Local\Temp\NDF82B2.tmp" -ep "NetworkDiagnosticsSharing" Loaded Modules (43)
Or:
Detection type Lockdown Application PathC:\Windows\SysWOW64\rundll32.exe Version10 PID22208 Detection ID2b7c55ff0422b6e9674a1b6842768914918eb75772fc7236febd7d6eac914a07 Mitigation Lockdown Policy LockdownNewFile Timestamp 2024-03-26T12:57:29 Platform 10.0.22621/x64 v3 06_ba* PID 22208 WoW x86 Enabled 08FDAE3A40000004 Silent 0080800000000000 Application C:\Windows\SysWOW64\rundll32.exe Created 2022-05-07T05:19:48 Modified 2022-05-07T05:19:48 Description Windows host process (Rundll32) 10 Filename C:\Windows\system32\msdt.exe Lockdown type: LolBin Command line: -skip TRUE -path "C:\Windows\diagnostics\system\networking" -af "C:\Users\xxxxxx\AppData\Local\Temp\NDFCE93.tmp" -ep "NetworkDiagnosticsSharing" Loaded Modules (36)
This thread was automatically locked due to age.

