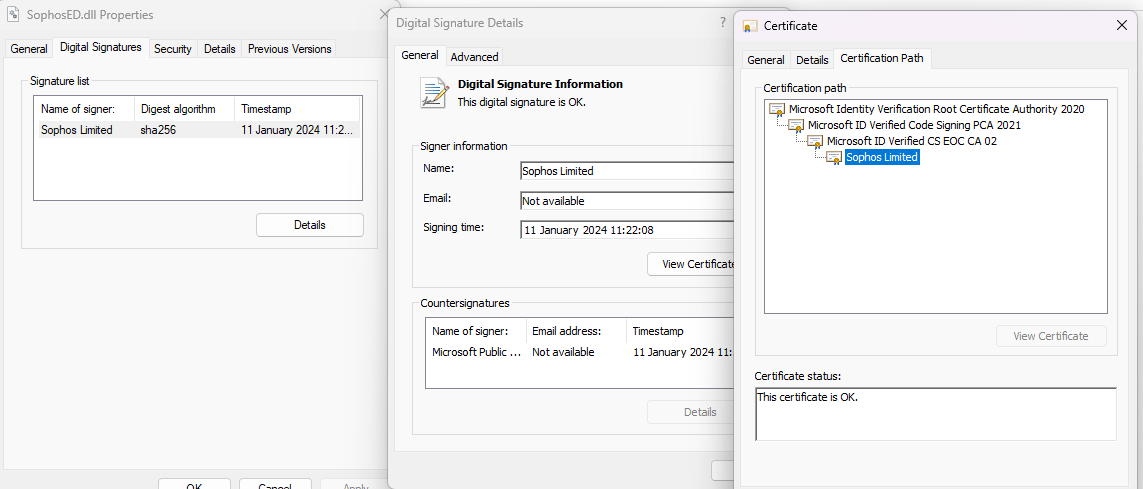
Hi Team,
Some of the users have started to complain about the error after system restarting they are getting (C:\Windows\System32\SophosED\SophosED.dll is either not designed to run on windows 10 22H2).
I am attaching the screenshot for more info.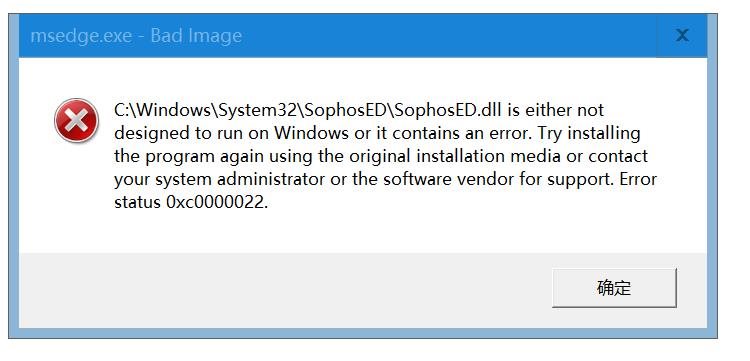
This thread was automatically locked due to age.