Dear All,
Hope you are all doing well.
I have a question regarding AMSI Sophos Protection. Is it okay to turn off AMSI logging? Turn off AMSI logging to resolve compatibility issues – Sophos Home Help
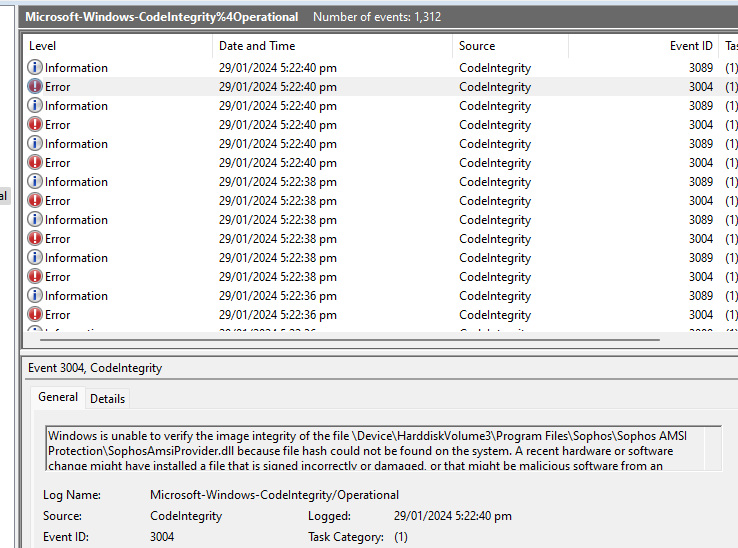
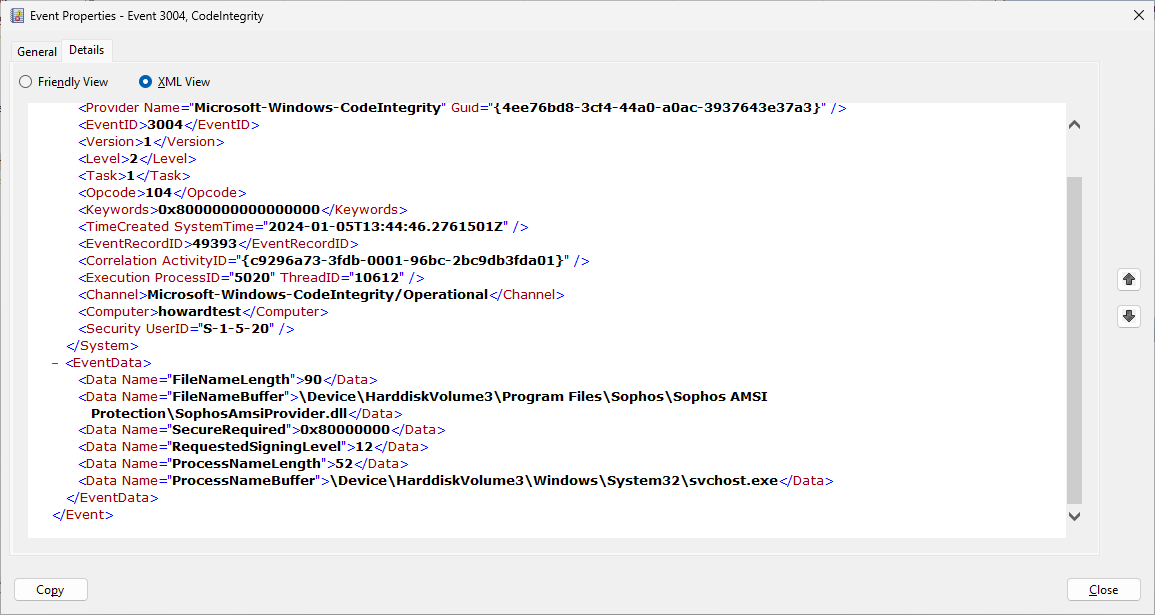
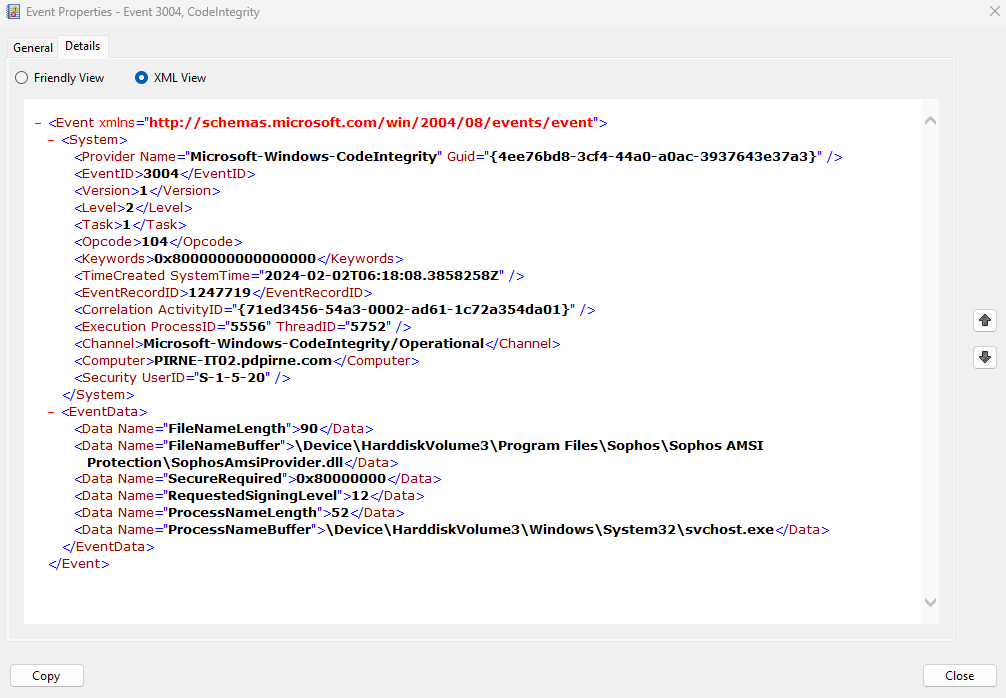
Since we upgraded our workstations to Windows 11 with Sophos Endpoint installed, we are receiving event logs showing Windows Audit Event Failure.
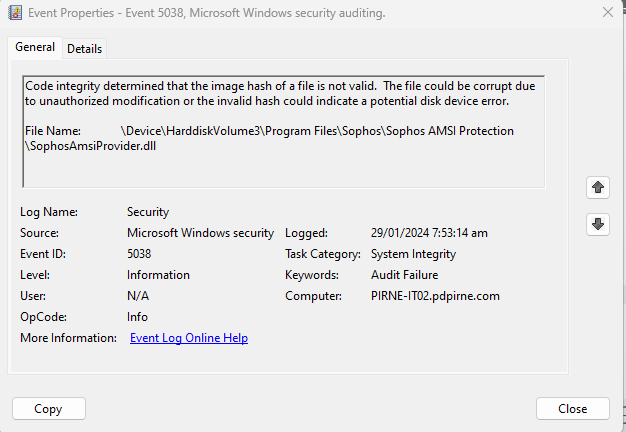
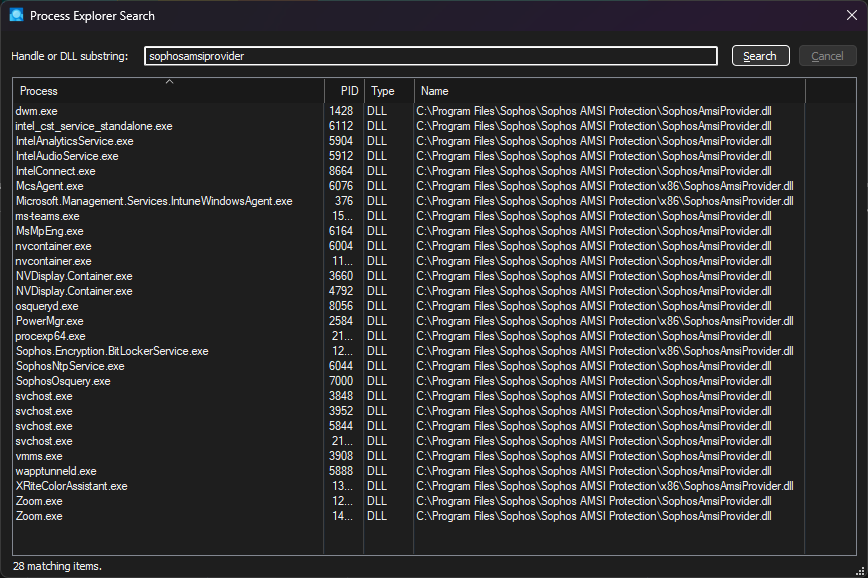
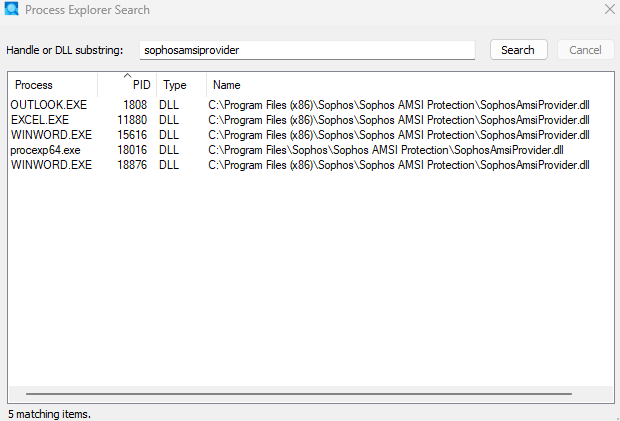
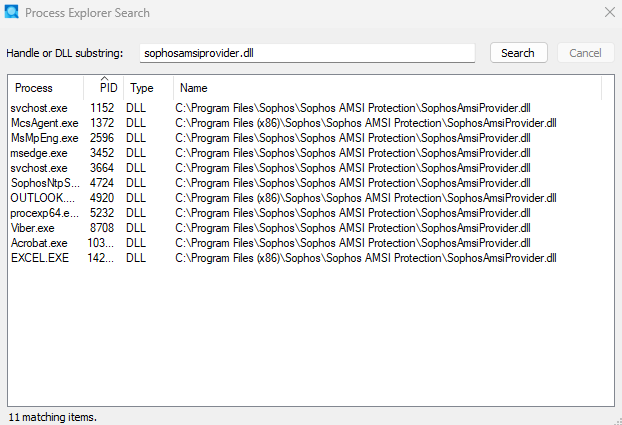
Then I found this article: Windows Security Event Log: Event ID 5038 System Integrity Audit Failure against SophosAmsiProvider.dll
For now, our audit logs from Wazuh are full because of these alerts. Above article said that this is a normal behavior, and we can ignore it. So, is it safe to turn off the AMSI logging so we could prevent it from triggering in Windows event logs? If we turn off, does the protection also will be turn off?
Thank you in advance!
This thread was automatically locked due to age.