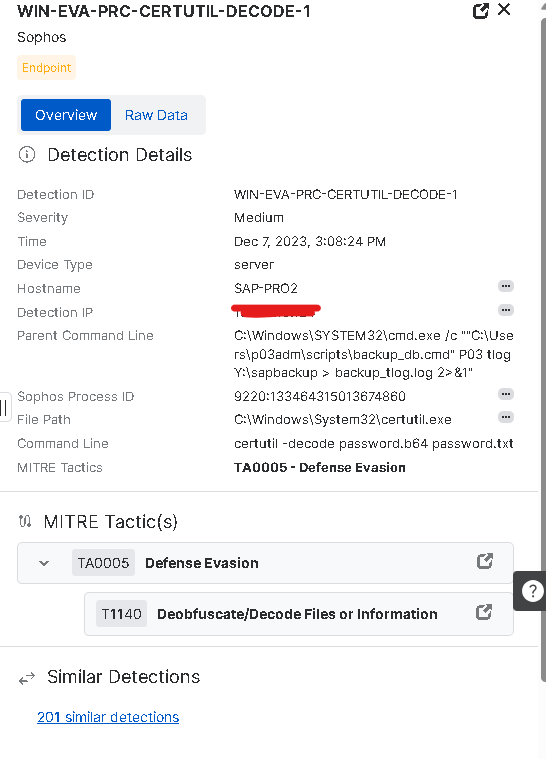
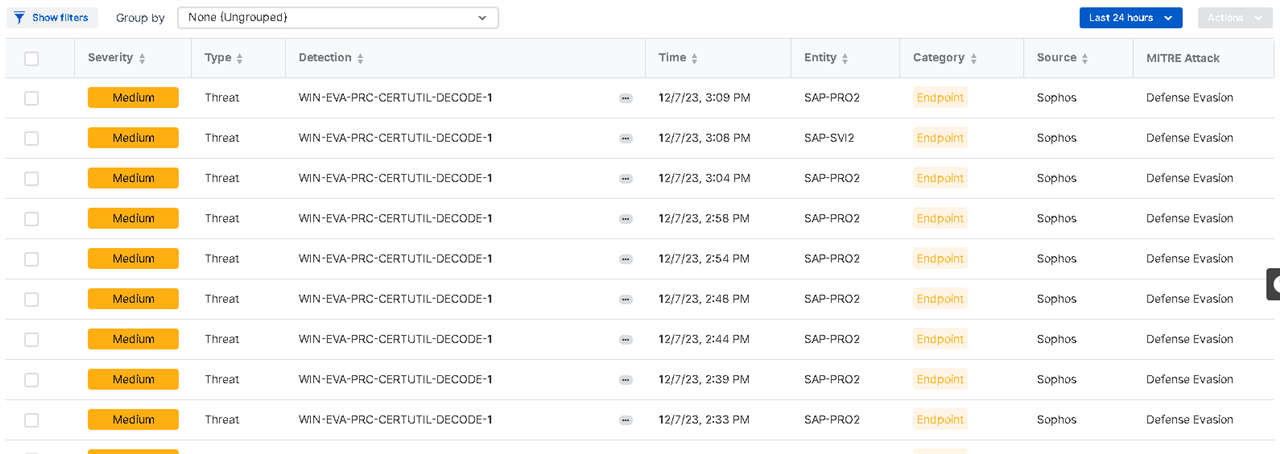
Our SAP server’s backup process, that is using certutil.exe, is detected as a defense evasion threat.
In details the detection is
Detection ID: WIN-EVA-PRC-CERTUTIL-DECODE-1
Command Line: certutil -decode password.b64 password.txt
File Path: C:\Windows\System32\certutil.exe
Parent Command Line: C:\Windows\System32\cmd.exe /c "C:\Users\p01adm\scripts\backup_db.cmd P01 tlog Y:\sapbackup > backup_tlog.log 2 >&1!"
Mitre Tactics: TA0005 Defense Evasion
T1140 Deobfuscate/Decode Files or Information
I've tried to exclude certutil.exe with an exclusion in the Threat Protection device policy, but it not works.
How can I disable this detection?
Thanks.
This thread was automatically locked due to age.

