Hello everyone,
We get the following alert
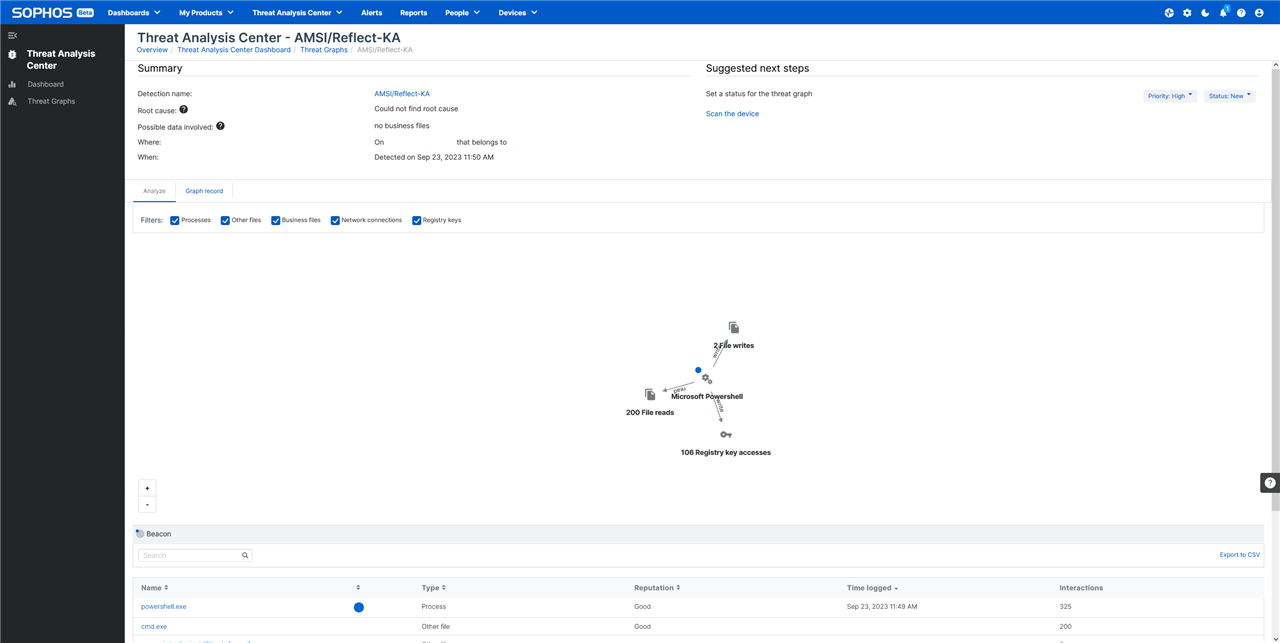
What happened: We could not clean up a threat.
Where it happened: computer name
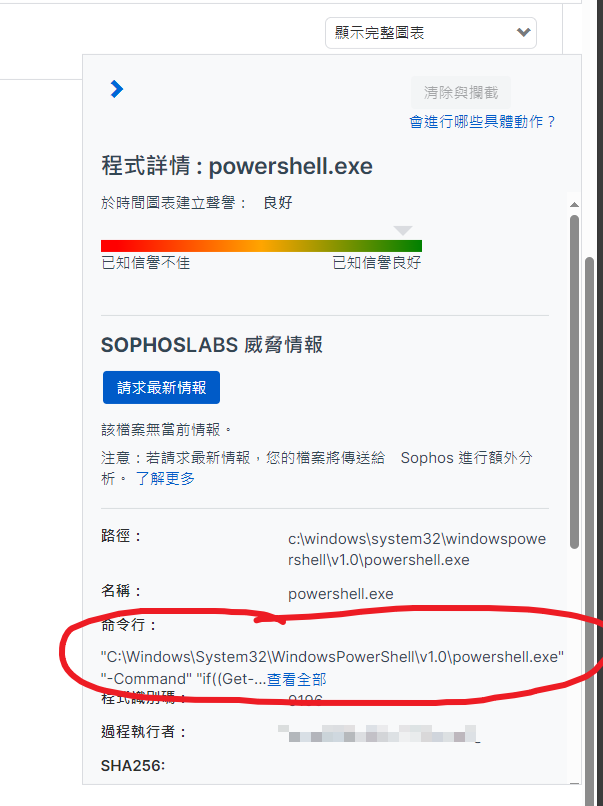
Path: C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe
What was detected: AMSI/Reflect-KA
How severe it is: High
What Sophos has done so far: We attempted to clean up a threat.
It is for only for one users, used to be two. I cleaned the temp files for both users on their respective PCs, and it seems that fixed the issue for the first user, or maybe just a coincidence.
However this one user's account on this PC keep giving us this detection.
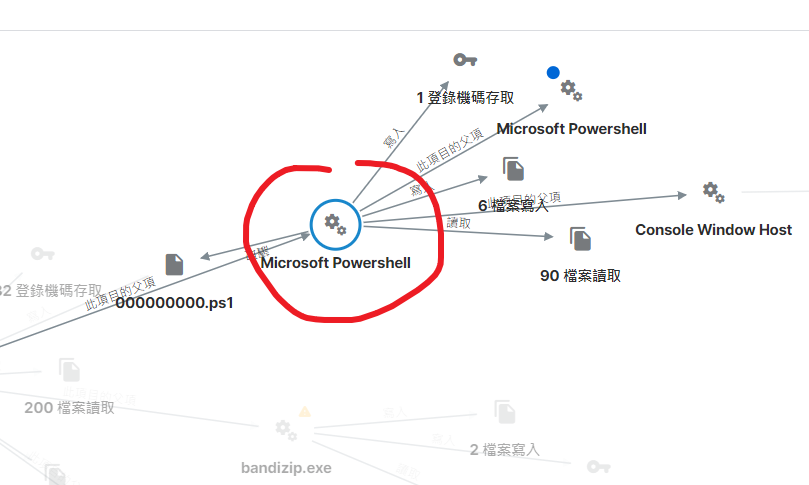
Seems to be triggered by two different things, but they all lead to powershell.
Please see the images, hope that helps.
Any idea about this. Much appreciated.
This thread was automatically locked due to age.