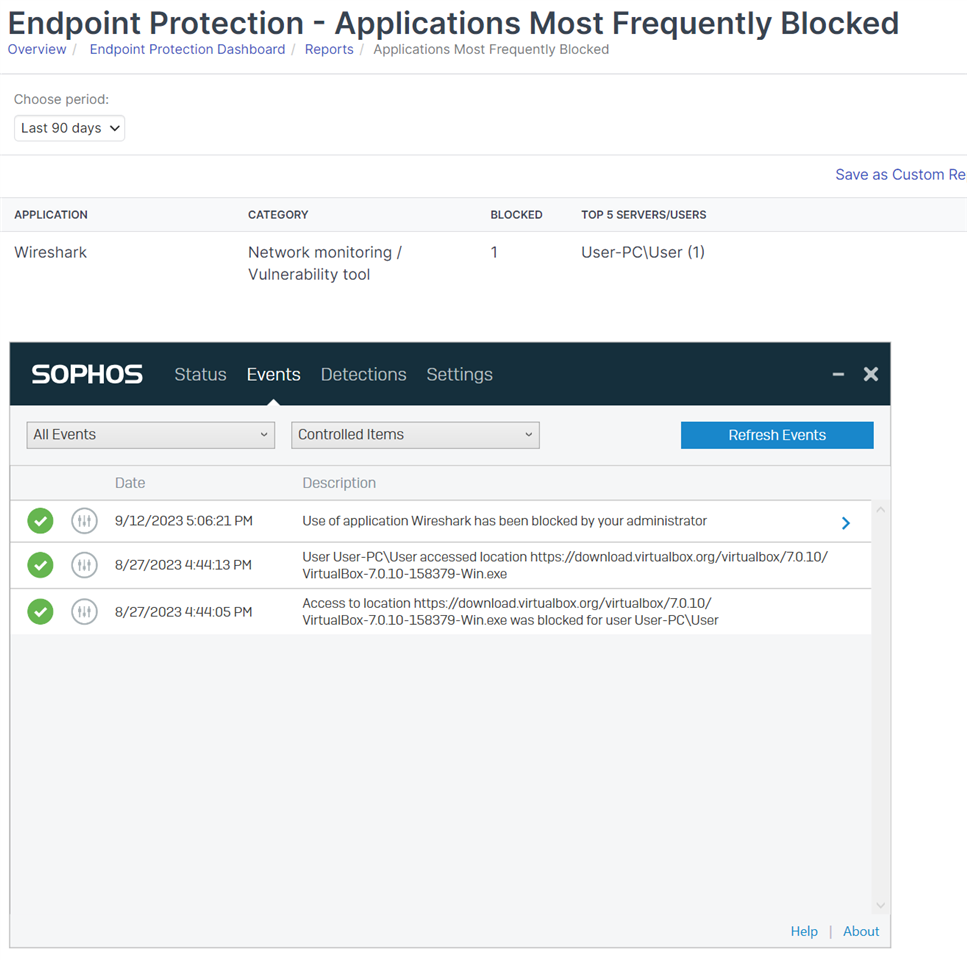
I am testing the Sophos endpoint protection EAP, and have synchronized application control enabled. I am having an issue, where all the controlled application that are set to blocked are showing up as allowed, even applications I do not use, such as remote desktop, SSH, TightVNC, proxies ect.
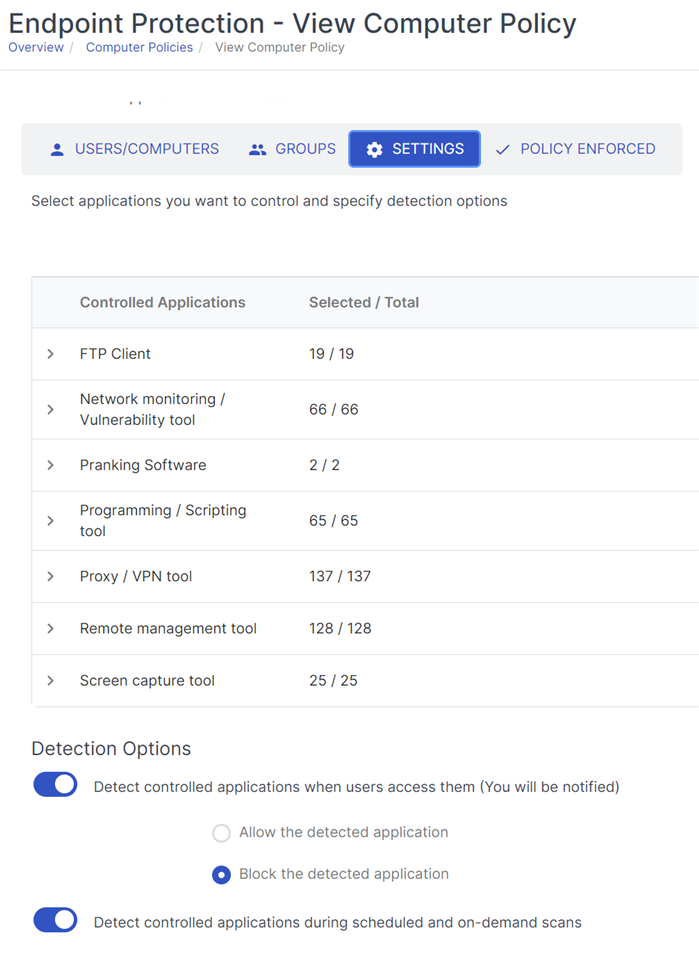
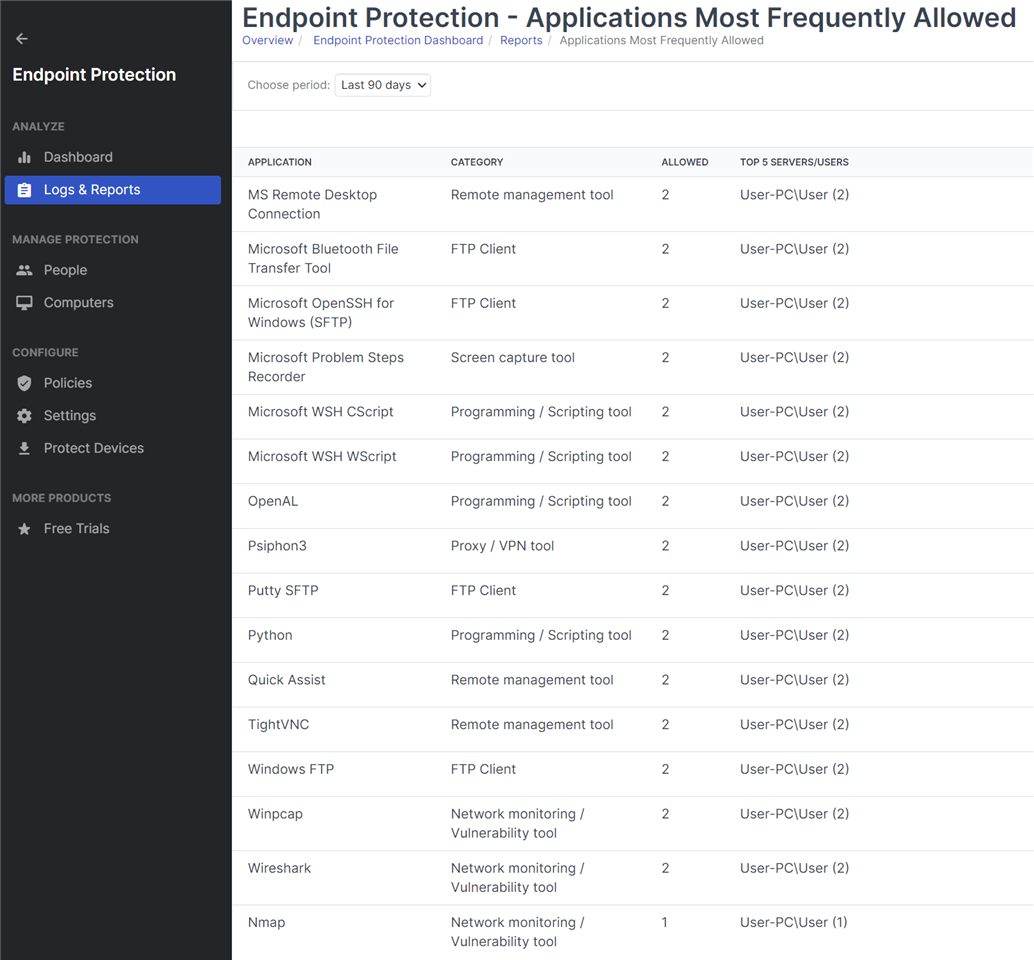
How can these applications be blocked, and also frequently allowed the same time? i do not use any of the programs. Also, I have wireshark blocked, and the Endpoint Security informs me that it was blocked, but it not showing up in the list of blocked applications in Sophos Central.

This thread was automatically locked due to age.