I notice a frustrating Performance issues on Windows Servers with the Taskmanager for some time now. Not sure if known or already fixed.
Taskmanager opens normally but when you switch to an other register tab like the Details register, it hangs like this
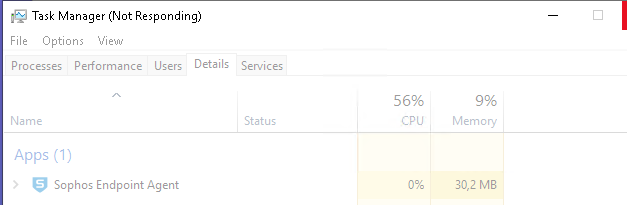
or shows only white space like this for up to 20-30 seconds, depending on CPU speed:
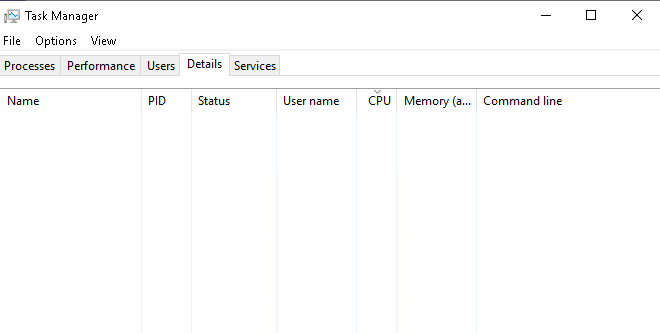
Once loaded, you can switch between the different registers and all is fine. If you close the Taskmanager and open it again, the issue is happening again.
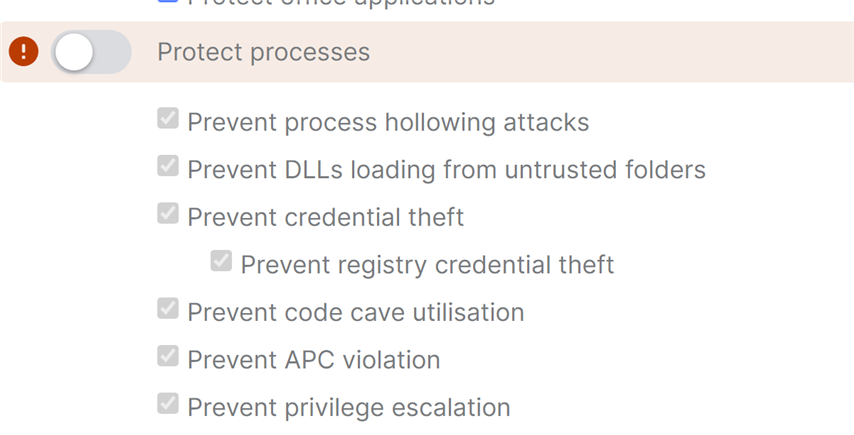
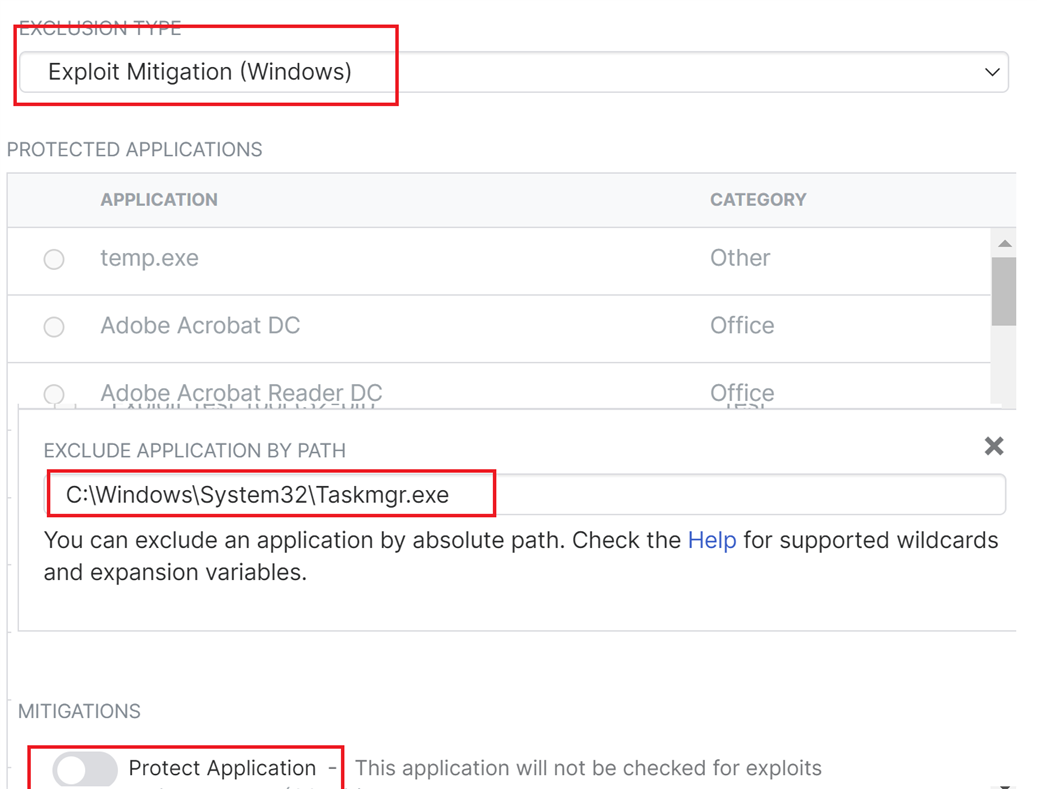
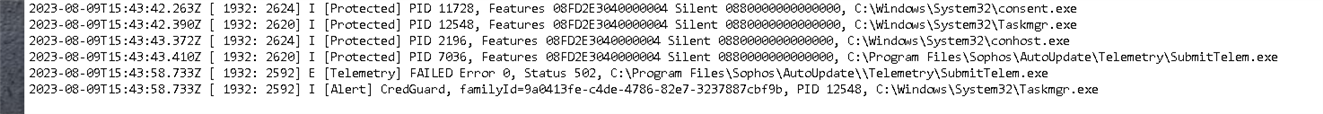
After disabling Sophos Components one by one, it turned out to be Exploit Mitigation causing the issue. Can be recreated at any time.
OS: Server 2019, Server 2022, and surely others.
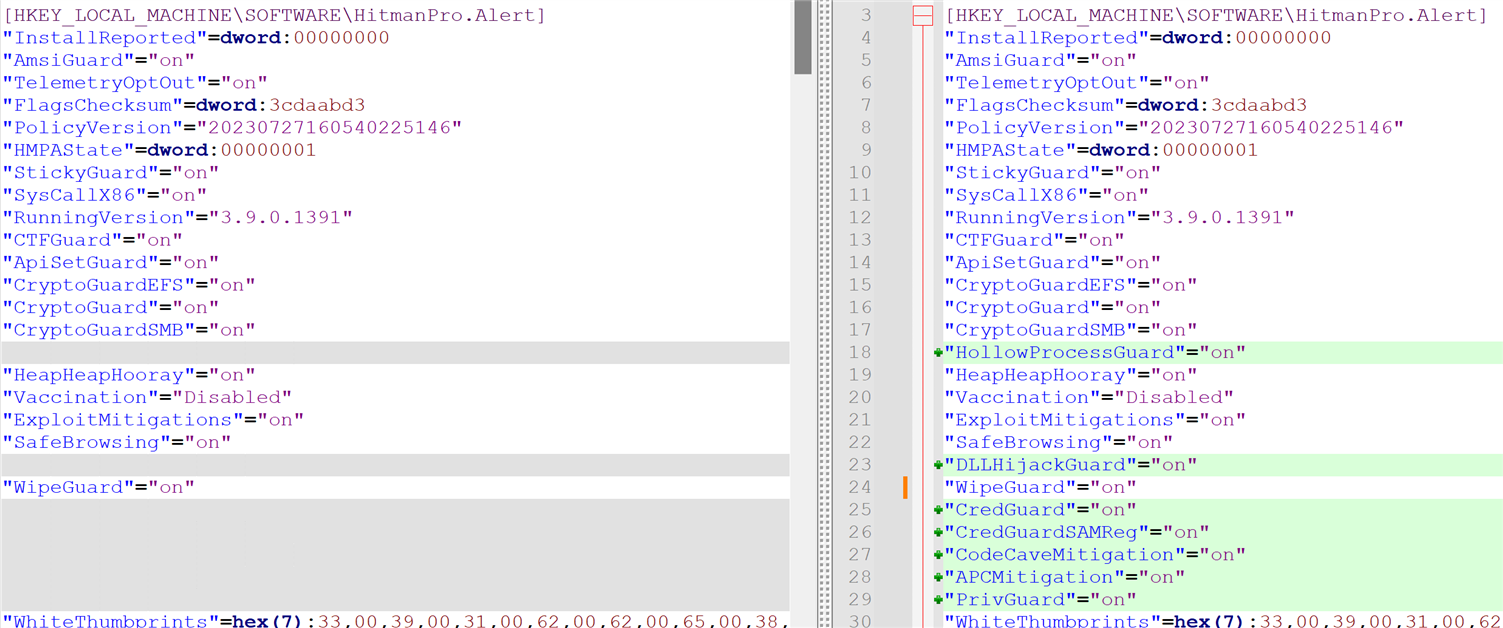
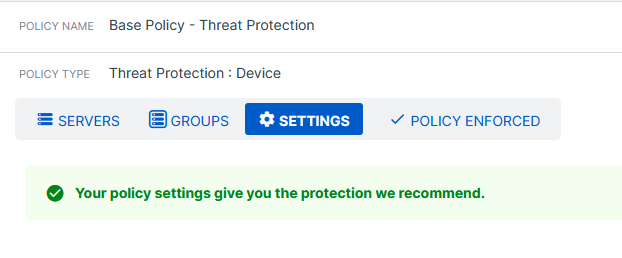
Affected Endpoints, that's the latest Version we have:


All policy settings are default & recommended
This thread was automatically locked due to age.