Is anyone else noticing issues with SSL inspection recently? we've just had the new core agent 2023.1.0.73 deployed on our estate and seeing a vast amount of websites being blocked 'the encryption used by this server hosting the URL is insecure' downgrading our core agent to the previous version completely removes this problem.
As you can see from the screenshot this is a Cisco website using TLS 1.3 but is being blocked.....
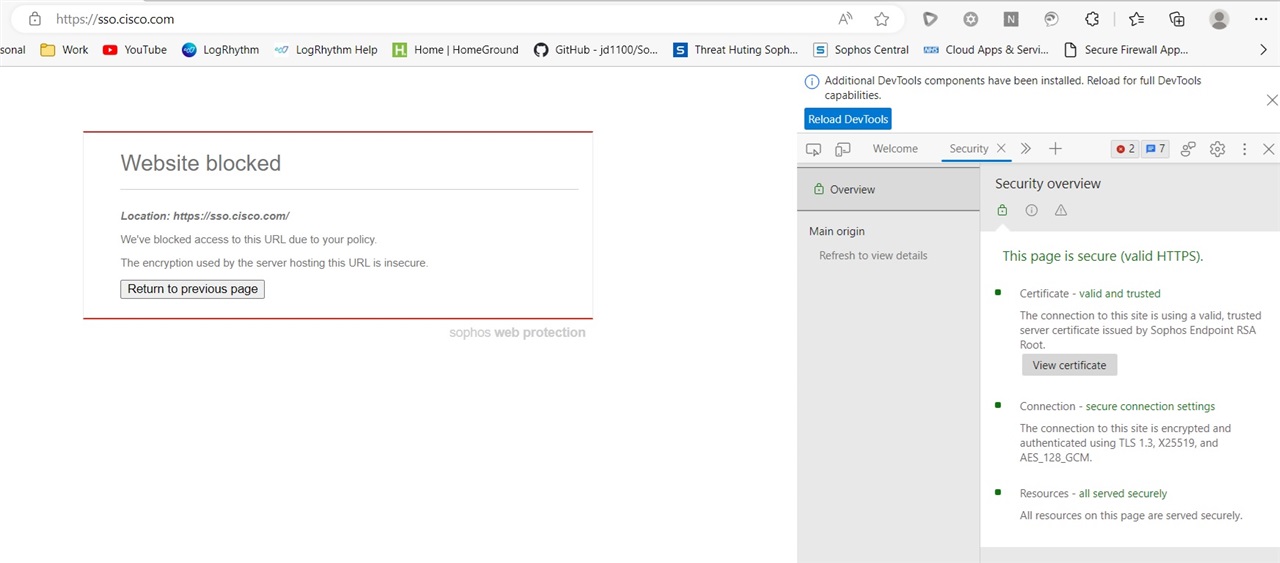
2023-06-05T07:15:33.716Z [18416:24736] I [clienthello] connection:0x17c6083ae70 sni:sso.cisco.com ip:72.163.4.70 flowId:98923 decision:decrypt source:snf_cache
2023-06-05T07:15:33.728Z [18416:24736] E SSL_do_handshake returned SSL error= 1 reason=338 error:00000001:lib(0)::reason(1) SSL*=0000017C5F1ACB80
2023-06-05T07:15:33.729Z [18416:24736] E Failed to set up SSL MITM encryption: Unrecoverable SSL error during handshake(): error:00000152:lib(0)::reason(338)
2023-06-05T07:15:33.737Z [18416:24248] E SSL_do_handshake returned SSL error= 5 reason=0 error:00000005:lib(0)::reason(5) SSL*=0000017C5F1ACB80
2023-06-05T07:15:33.737Z [18416:24248] E UnrecoverableError in hasOutput() for flowId=94696 side=Right
2023-06-05T07:15:33.737Z [18416:24248] E SSL_do_handshake returned SSL error= 5 reason=0 error:00000005:lib(0)::reason(5) SSL*=0000017C5F1ACB80
2023-06-05T07:15:33.737Z [18416:24248] E UnrecoverableError in output() for flowId=94696 side=Right
2023-06-05T07:15:33.738Z [18416:24248] E SSL_do_handshake returned SSL error= 5 reason=0 error:00000005:lib(0)::reason(5) SSL*=0000017C5F1ACB80
2023-06-05T07:15:33.738Z [18416:24248] E UnrecoverableError in hasOutput() for flowId=94696 side=Right
2023-06-05T07:15:33.738Z [18416:24248] E SSL_do_handshake returned SSL error= 5 reason=0 error:00000005:lib(0)::reason(5) SSL*=0000017C5F1ACB80
2023-06-05T07:15:33.738Z [18416:24248] E UnrecoverableError in output() for flowId=94696 side=Right
This thread was automatically locked due to age.


