This thread was automatically locked due to age.

I'm pretty sure it's to do with Software Restiction Policies under:
HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\safer\codeidentifiers\262144
This seems to be referenced in the query pack file
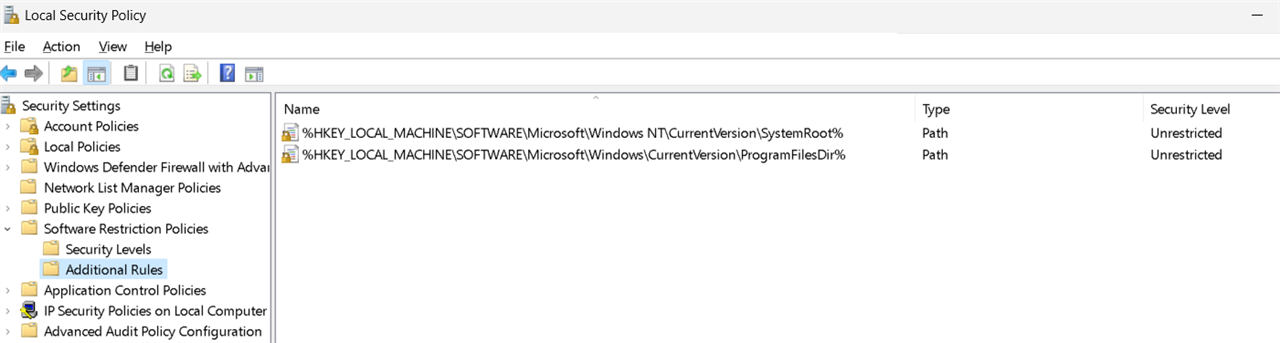
Do you have a any rules on the computers with the error?
If you create the default 2 additional rules as shown in the previous screenshot. I assume it clears from the future.
I suppose you can do the same via Group Policy.
What version of the query pack do you have:
C:\ProgramData\Sophos\Live Query\Queries\Packs\Latest\version.txt
Thanks.
Creating a default SRP GPO will neither block or allow something special. It is just that there is something configured for the default MS System folders.
Sounds like the Query scanning for SRP registry keys in that way does not make much sense.
It only creates "log noise".
Creating a default SRP GPO will neither block or allow something special. It is just that there is something configured for the default MS System folders.
Sounds like the Query scanning for SRP registry keys in that way does not make much sense.
It only creates "log noise".
We're seeing the same issue. When I look at Software Restriction Policies | Microsoft Learn I see that this technology is deprecated and replaced by Windows Defender functionality.
While creating the necessary keys through GPO sounds like a good workaround, I'm somewhat reluctant to make changes in my enterprise infrastructure just to avoid noise in the security software, unless it's a change that is necessary for security.
I would also love to know why the detection triggers on a deprecated function that a user can choose to activate or not. Are there people from Sophos on the community forums, or should this best be ticketed to support as an inquiry?
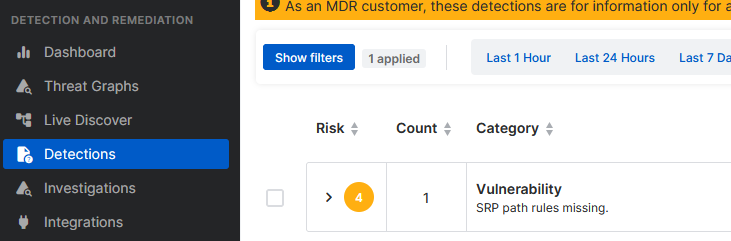
I have asked Support the question why it detects this seemingly harmless deprecated function, and like what's said in Central itself, the response was "These detections are for information only unless you have an MDR license." Which I don't (hoping to get one soon). It's still a shame it clutters up the new, extremely useful dashboard so much.
Today I've created a default SRP policy on my workstation and set the default security level to "Basic User" to test if it has any adverse side-effects and to see if the detections change. I'll post the results in a few days as the detections occur on different times of day.
Edit: A default SRP policy with default security level set to 'basic' doesn't change a thing. It still complains about missing rules, and I'm not prepared to deploy an application whitelisting system just to get rid of the detection. Guess I'm living with it.
"detections identify activity on your devices that's unusual or suspicious but hasn't been blocked. They're different from events where we detect and block activity that we already know to be malicious." Sadly you dont get any information via support. The reason is simple, they want to sell MDR ;-)
After raising your concerns to our teams internally, I was informed that the detections related to Software Restriction Policies will be disabled in an upcoming release.

That is very good news, thank you.
We do understand that when looking at the 'detections' we're kind of looking "under the hood" of the Sophos engine and many detections are just observations (like a changed user, password incorrect, etc) and are mainly for MDR purposes. But, especially with the new user friendly dashboard graphs, end users can also keep a better eye on their environment (even those with MDR). If these 'medium' alerts will be gone (or informational) in the future, the view will be so much clearer.
Thanks!