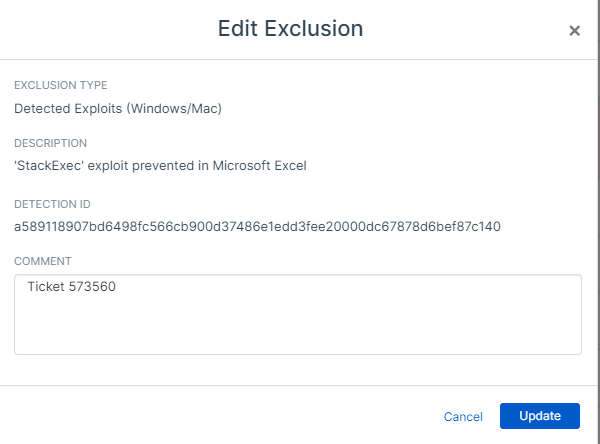
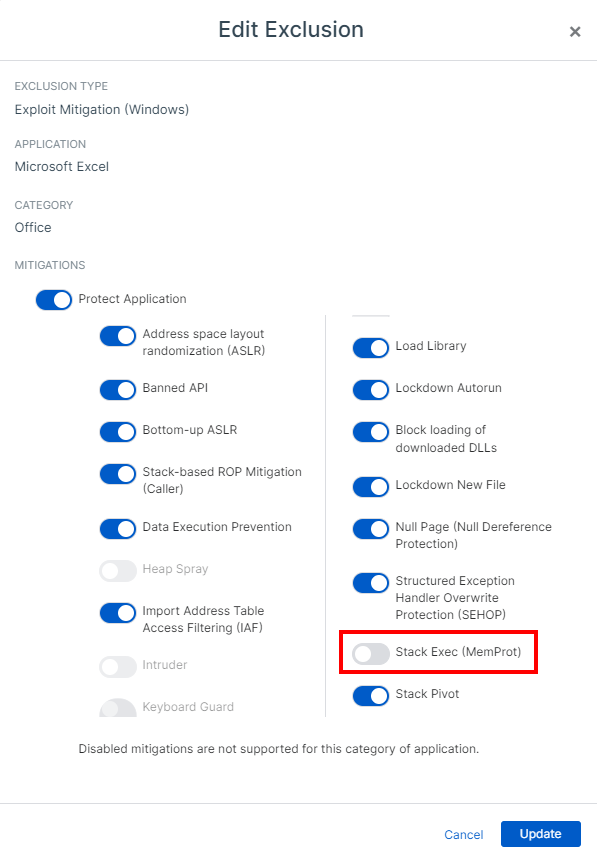
Recently we noticed that we are receiving over five detections on a given day for Stack Exec. The threat graph for all detections are identical with the root cause been Microsoft Office 2016. The reputation for Microsoft Office is good and the file is legitimate. We are using Starquery so the detections are triggering on the sqlengine.dll, symtraxas400provider.dll among other .dll files based on the 'uncertain reputation'. These files are legacy based on the fact that the application was written along time ago for certain criteria which as not changed over the years
In investigating these alerts the only option given is block and clean. That option cannot be use as the application is needed. Can an exclusion be created for this specific starquey detection? How can this detection be reduce?
Are others receiving this detection and how do you address it?
This thread was automatically locked due to age.