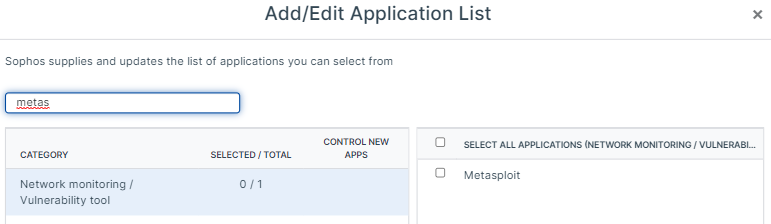
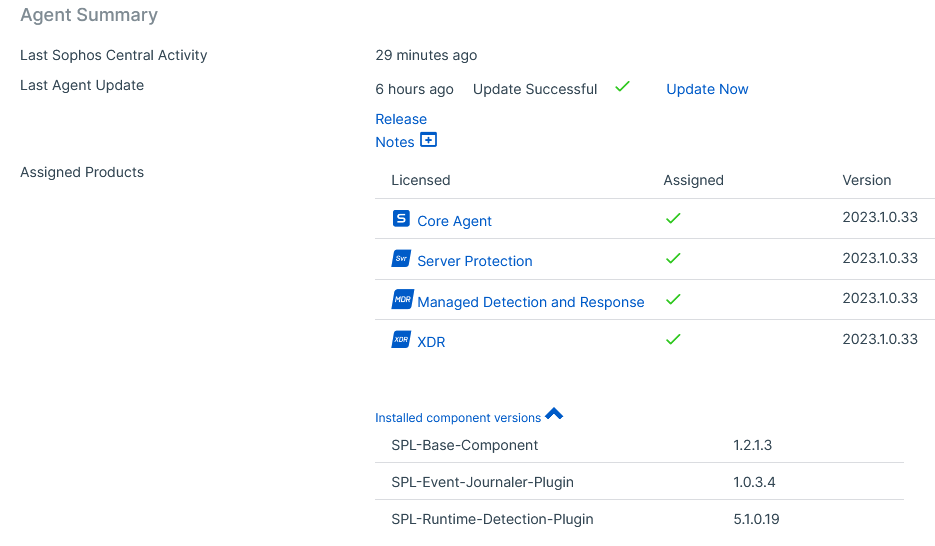
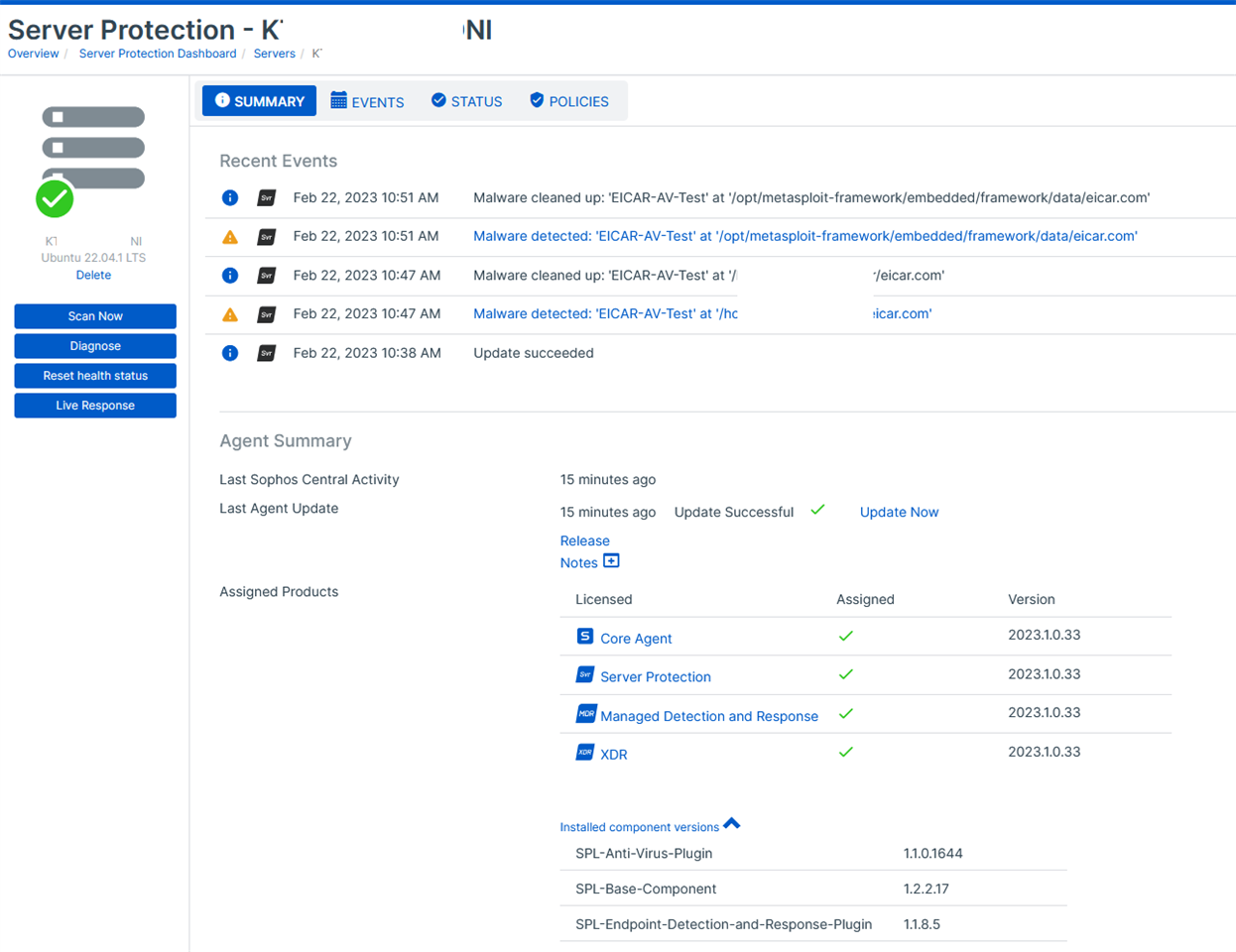
An admin downloaded and installed metasploit framework on a Linux Server with Intercept-X installed.
Nothing happened from the Sophos side.
I expected it to detect and alert at least a PUA we then need to whitelist.
As a further test I did a download of metasploit framework for windows on a windows machine. Sophos Firewall did not detect any threat. Further I did not install metasploit but did the right click scan with Sophos EP.
Nothing happened again.
I think it's strange that you allow a tool that can pentest your internal network without any notice.
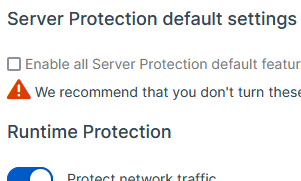
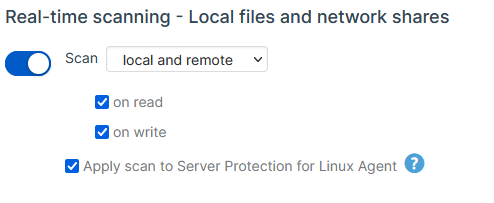
Linux Server:
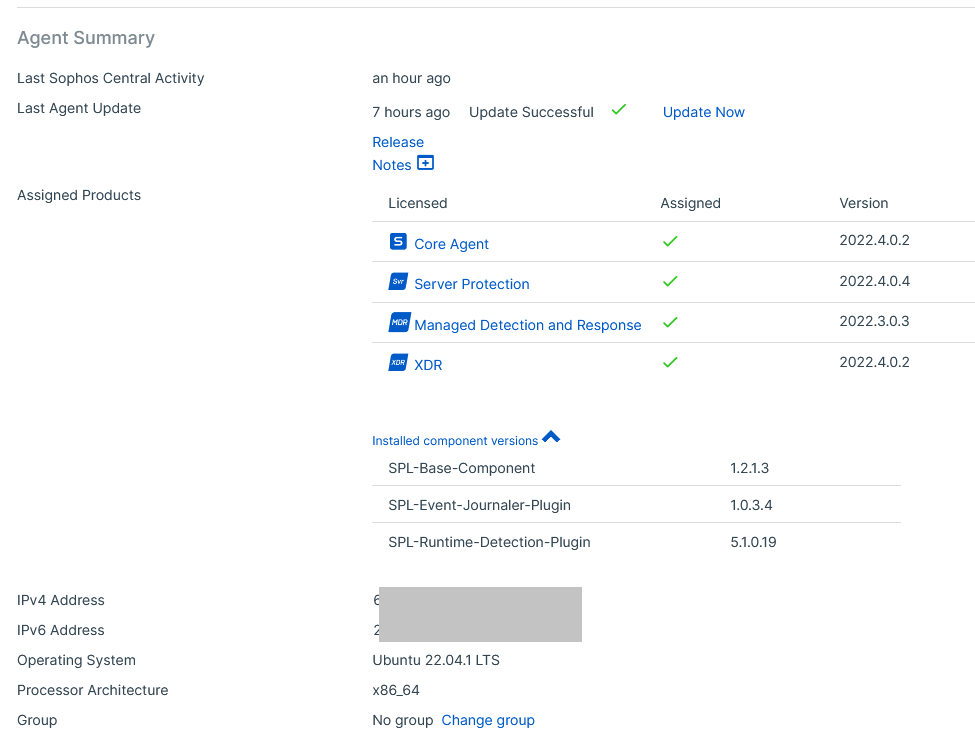
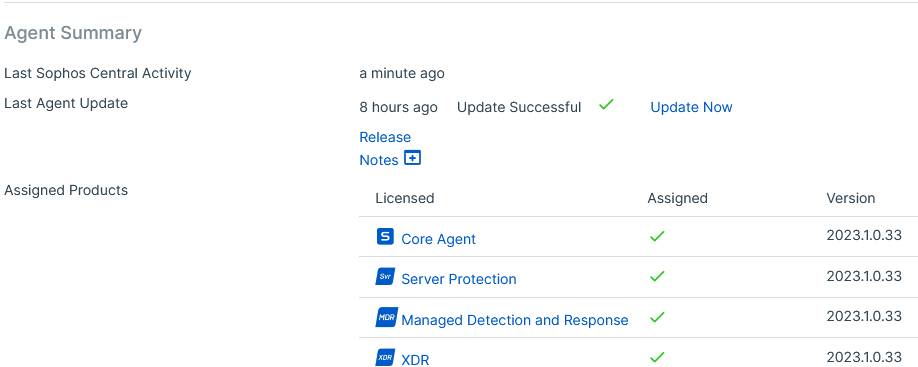
Windows EP:
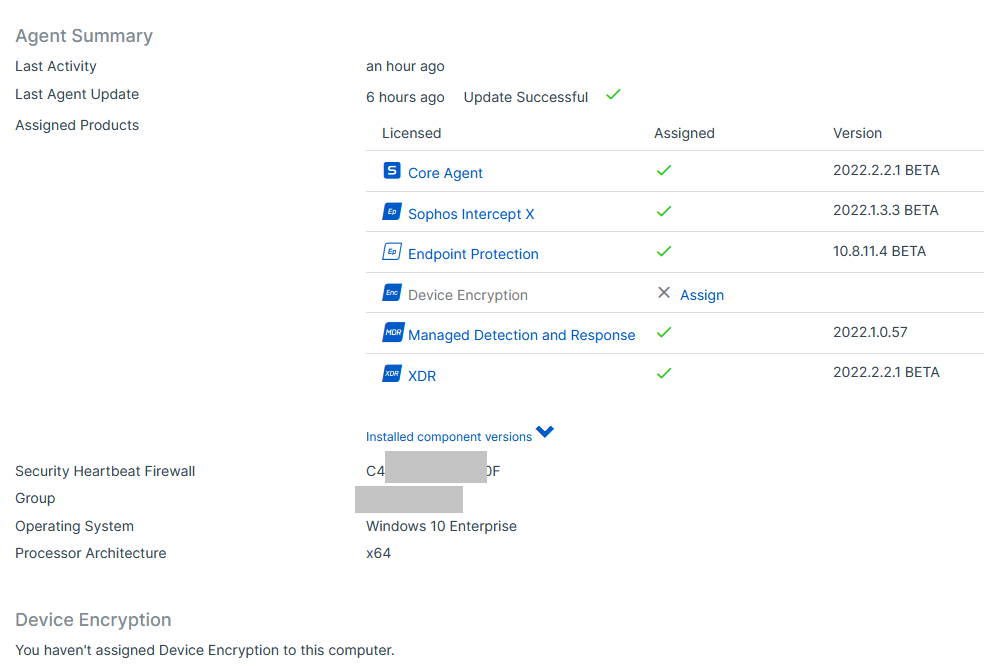
This thread was automatically locked due to age.