Hi everyone,
Two PCs in the organization I manage can no longer connect to any wi-fi(office, home or hotspot).
The users reported that the issue started on Thursday 16/06/2022. They were suddenly disconnected from the wi-fi they were connected to, and from tat time could no longer reconnect, or connect to any other wi-fi.
I have reset the wi-fi adapter, and attempted to update(using a LAN cable for internet connection) – but Microsoft reported that the driver is up to date.
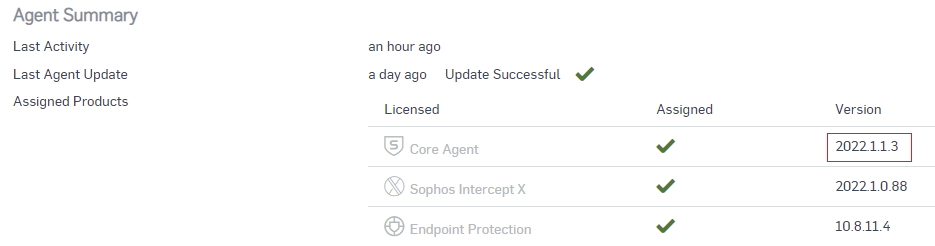
However, after i uninstalled Sophos Intercept X Endpoint that was running on both PCs, they could connect to any wi-fi normally as before, but upon re-installation of the Endpoints, the issue came up again.
I formatted one the PCs and reloaded the Operating System. It could connect to wi-fi, but once I installed the Sophos Endpoint, it could no longer connect, - “Can’t connect to this network” is the message displayed after entering the wi-fi password.
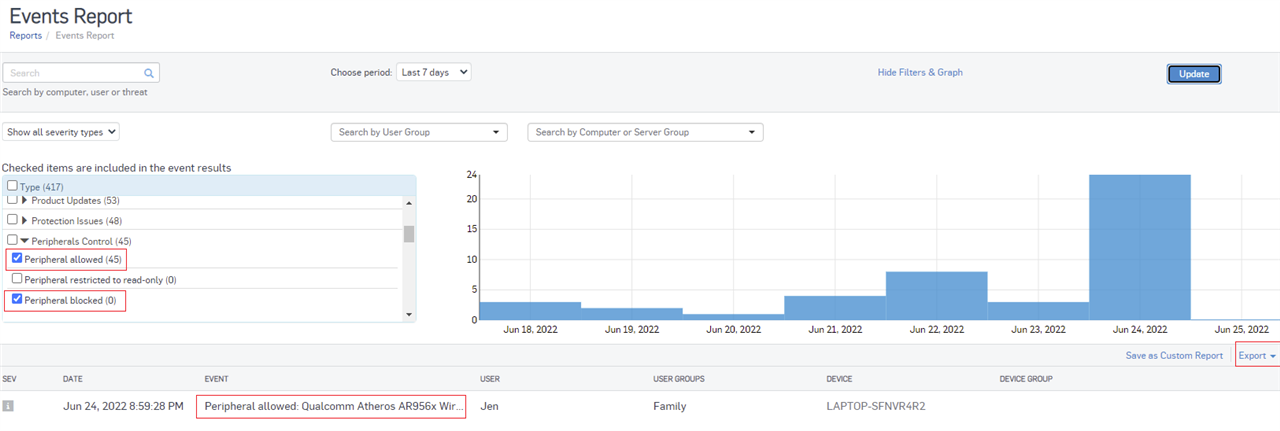
I connected a USB wi-fi adapter(manufactured by Realtek) on one of the PCs, nd the PC could connect to wi-fi normally with it.
The PC model is HP 250 G2
OS is Windows 10 Pro
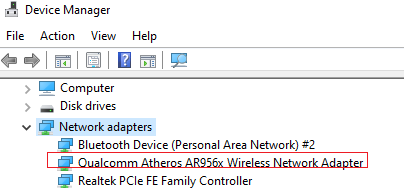
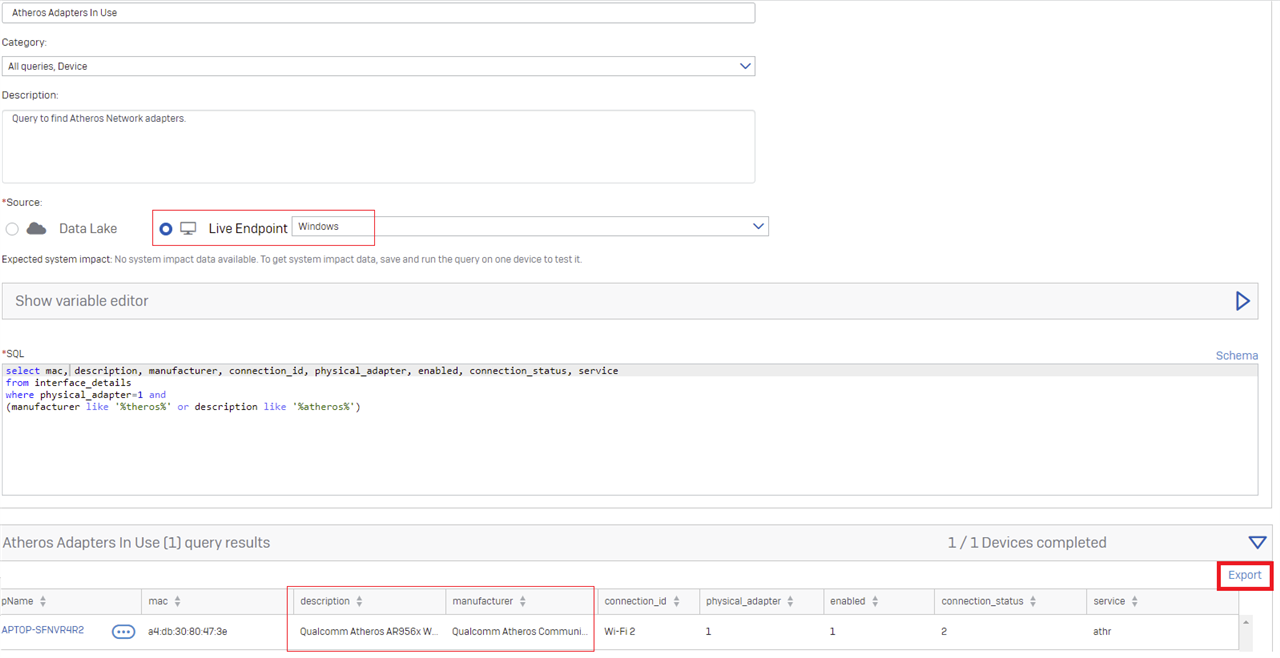
The wi-fi adapter model is QCWB335(written on the adapter card)
The wi-fi manufacturer is Qualcomm Atheros
*But the driver installed for it by Microsoft which had been working is Qualcomm-Atheros-QCA9565, as seen in Device Manager
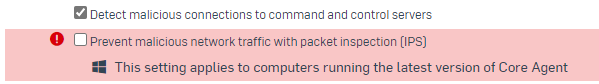
I am suspecting that that there must have been an update from Sophos that is causing this abnormal behaviour, because all other systems in the organization are working fine right now.
I need help to fix this as soon as possible.
Thanks
This thread was automatically locked due to age.