Hello
First of all, I'm completely new to Sophos, Second of all, i dont have access to the Sophos console. (New IT job, havent been given access yet)
my question is this though, we deploy Sophos
-core agent
-endpoint advanced
-sophos intecept x
on each machine here.
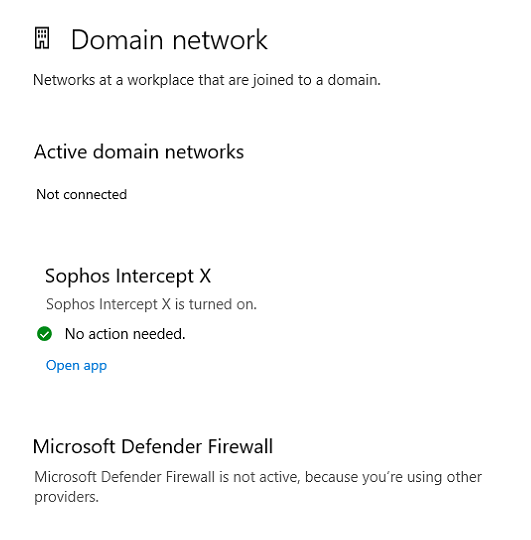
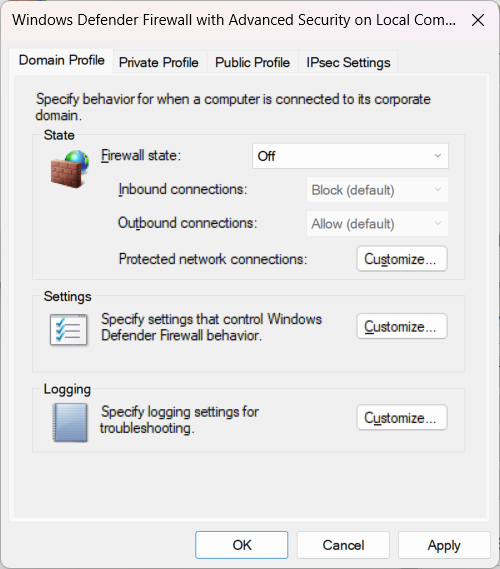
The firewall for each machine is controlled by windows Defender firewall.
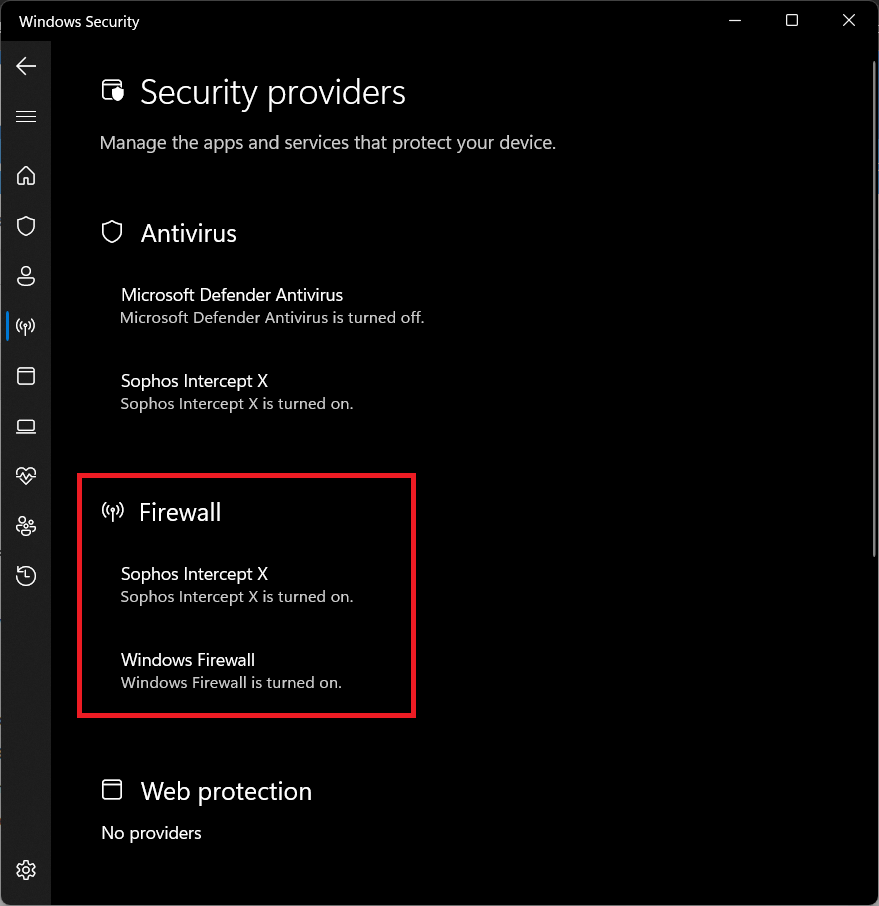
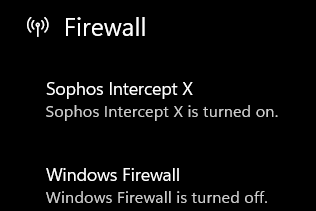
Except for one user, who for some reason, the firewall is managed by Sophos Intercept x.
How do i get this one user back to be managed by windows defender?
I removed the software, it went back to windows defender, i then re-installed it, and after a minute after the re-install , sophos intercept x took over the firewall...
any advice appreciated,
This thread was automatically locked due to age.