hello,
we have issue on more than 90 PC when we push last 21h1 and 21h2 update
The network thread protection installation fail :
C:\ProgramData\Sophos\Sophos Network Threat Protection\Logs
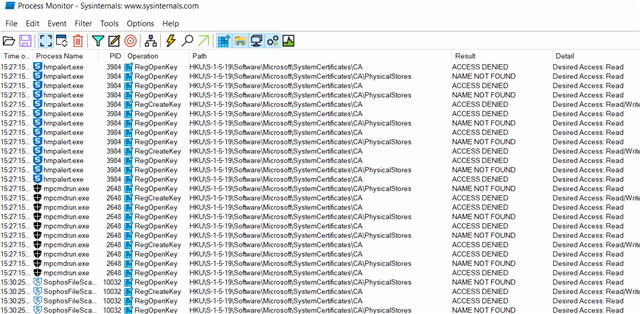
2022-02-15T15:06:30.217Z [11800: 4260] E DLL verification error: -2146869243: C:\Program Files\Sophos\Sophos Network Threat Protection\.\BPAIF.dll
2022-02-15T15:06:30.218Z [11800: 4260] E Failed to start service: File C:\Program Files\Sophos\Sophos Network Threat Protection\.\BPAIF.dll not signed by Sophos
2022-02-15T15:06:30.218Z [11800: 4260] E Could not start the service. File C:\Program Files\Sophos\Sophos Network Threat Protection\.\BPAIF.dll not signed by Sophos
theese KB doesn't work
https://support.sophos.com/support/s/article/KB-000036818
https://support.sophos.com/support/s/article/KB-000038164
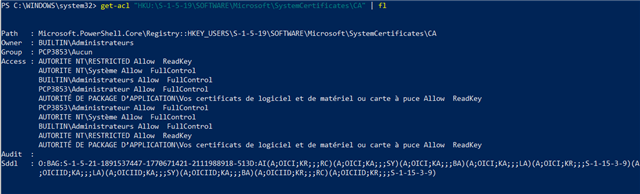
the sophos support say to me it's a Windows issue ... (a certificate issue)
but I have more and more pc with this issue,
I can't believe there is 90 pc with Windows issue ...
(pc Acer TravelMate P215-53 )
thnaks
This thread was automatically locked due to age.