Hi,
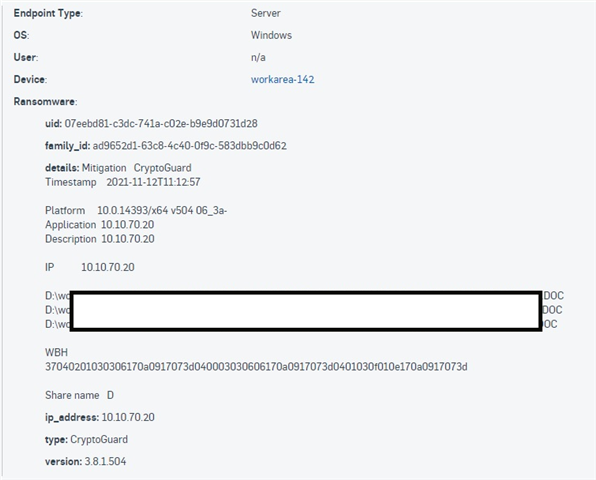
Sophos Cryptoguard detected a ransomware attack from a remote computer in our network. Crypto Guard restored original files and blocked access from the remote computer, which feels safe. But we have not been able to find out what really caused the attack. Could this be a false positvie?
This thread was automatically locked due to age.


