How can we protect our devices from accessing specific forbidden hosts when they are outside our network - so no longer protected by XG firewall?
I've created a Website Management rule in Central with tags for the recent Autodiscover issue.
This works but only blocks browser based access on windows clients (on MACs it does not even block browsing!).
On Windows I can still access the FQDN autodiscover.to with Outlook and telnet.
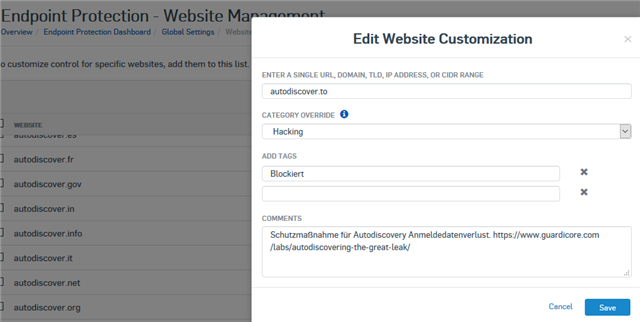
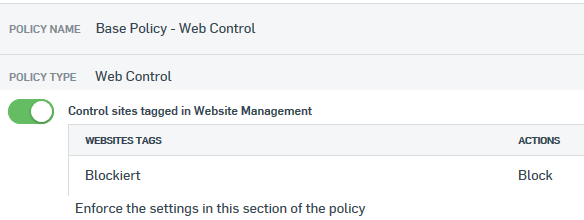
I do not want to put the FQDN into hosts file though this would be the safest way.
This thread was automatically locked due to age.

