Has anyone else had problems recently with Linux servers (specifically Amazon Linux 2 EC2 instances running at AWS) having massive CPU spikes on ever SAV update?
We've had multiple production systems fail multiple times a week due to this problem -- it only started in the last month or so though. We've been using SAV on these instances for years without a problem.
I've tried calling/opening an issue with Support ... but apparently all Sophos engineers are on vacation or something as no one has gotten back to me and the tech-support number for critical issues keeps hanging up on me. Since I can't get any official support (despite being a 10+ year corporate customer), I hoped someone else in the community might have some insight into this cpu spike problem.
thanks
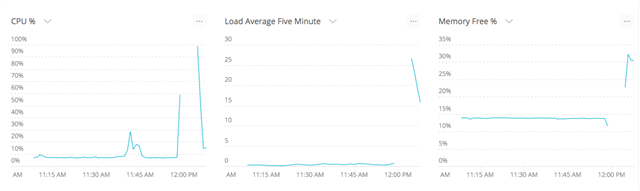
SAV update occurred at ~12:00pm ... as you can see our monitoring agent stopped sending data during the spike ... needless to say, this sort of spike causes problems for the application running on the instance as well. We shouldn't be getting DoS'd by our antivirus software :(
This thread was automatically locked due to age.



