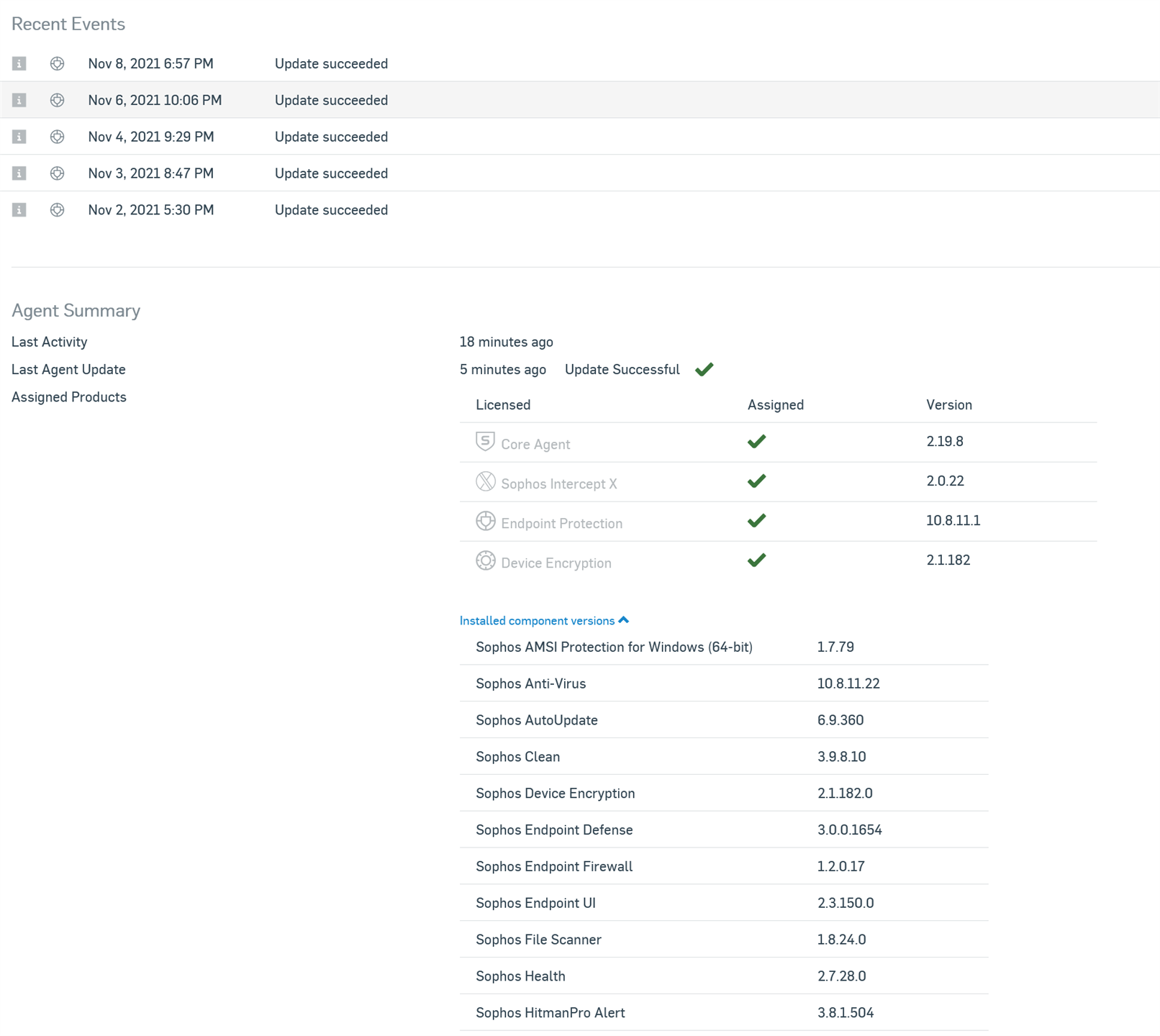
This is a continuation of https://community.sophos.com/intercept-x-endpoint/f/discussions/126818/unquoted-path-vulnerability---please-fix-asap. That thread is locked because of age....but the problem remains!
PavSupport 4 months ago you said "Its fixed in Hitmanpro version 3.8.2 which doesn't have announced dates yet, but this version is already available as a Hotfix. Hotfix after some testing becomes a part of general release (likely in June sometime)." It's now August and this still hasn't been updated. When is it going to happen?
This thread was automatically locked due to age.