We're receiving mails that got blocked by our mail gateway and I used them for testing Sophos Intercept-X.
Most of the mails I test have no attachment but links to zip files containing xls or xlsm files. I can download and execute the files without problem on my machine with Intercept-X.
Virustotal shows some vendors detect the files as trojan or whatever. Sophos does not. Why does it not work? Should be one of the most simple ways of attack.
I could present more examples. Here just the latest.
Mailbody:
Hallo
In diesem Brief sende ich Ihnen alle notwendigen Unterlagen zu unserem
baldigen Treffen, genau wie wir es vor nicht allzu langer Zeit besprochen
haben. Bitte überprüfen Sie die erforderlichen Informationen hier:
stage1.artisanenterprisellc.com/dr--era-skiles/peters-25.zip
zip is containing audit-69241583.xls
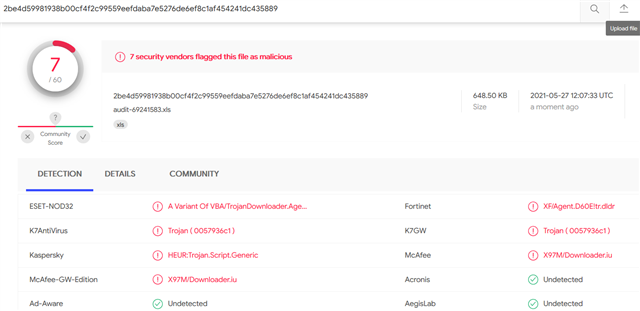
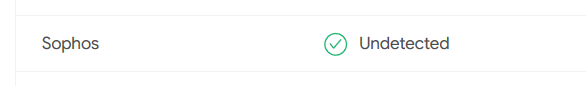
right click scan:
Screenshot of xls opened in online viewer.

This thread was automatically locked due to age.