Hi, i had a case opened at the sophos support regarding my problem and the fix after two weeks was to disable peripheral control.
Maybe someone has a better solution for this because i think there must be one
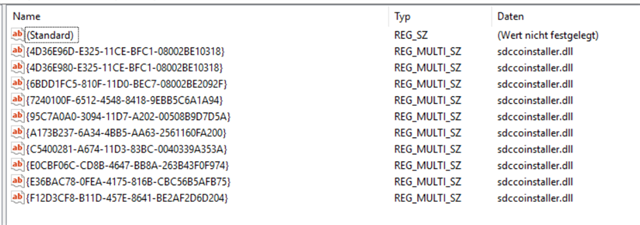
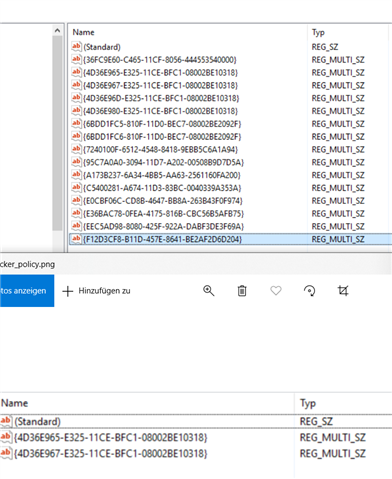
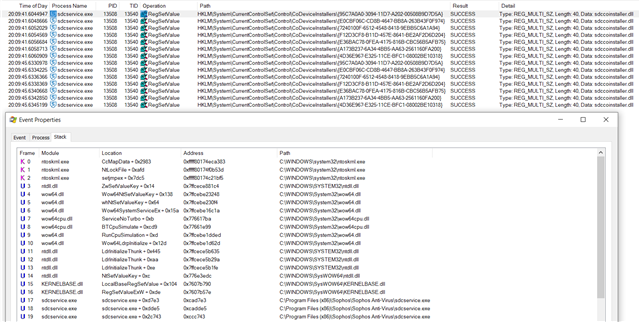
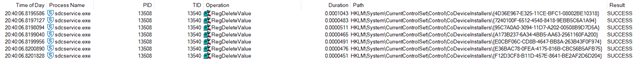
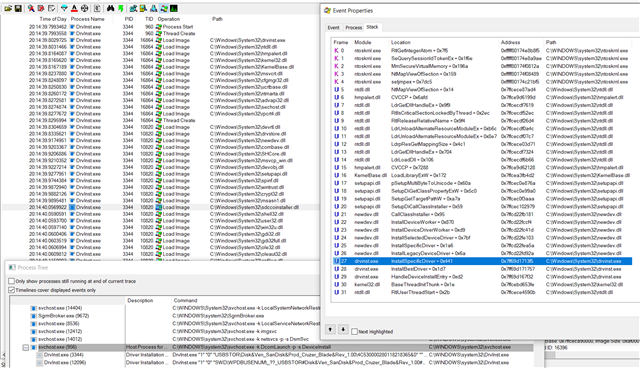
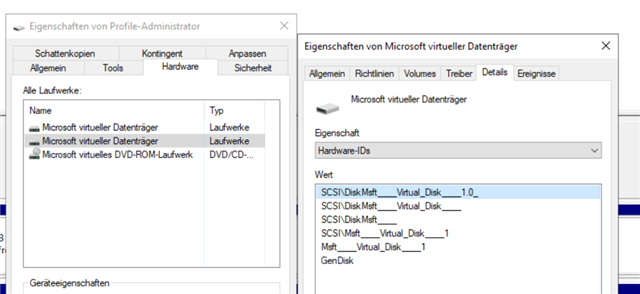
Problem is: Microsoft FSLogix Profile Container attach a virtual hard drive (.vhdx) from a network location to a Remote Desktop Server as the User's Profile Container. with Sophos Endpoint Protection enabled and Peripheral Control activated (Block Removeable Disks!) the process of attaching this file as a virtual drive fails. But no device is listed as blocked in sophos central. Otherwise i would have exclude it of course.
When i allow Access to Removable Disks in the Base Policy or a special Policy for the exact server. It works and the drive is mounted as you can see below.
I have no idea what else i could try. Hope anyone could help me.
Best regards Thomas
This thread was automatically locked due to age.