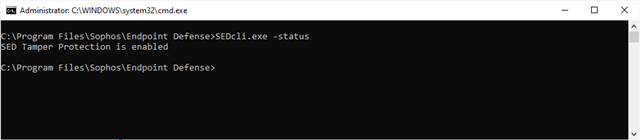
Since past 3 days ,on one of our production server,I installed Sophos(biggest mistake of my life) ,it was showing red on central cloud console ,so I called in the support.
We got into Sophos program Intercept X 2 months back and this was the last set.The support checked and turned on tamper protection for us and asked me to restart the server after business hours to get in sync with the cloud.
I did that and nothing happened ,so I called in ,for next two days and 10 hours ,the support engineers kept trying different WIndows hack instead of Sophos hack to uninstall this stuck Sophos agent ,and ofcourse they are not Windows admin and werent able to.The asked me for the safe mode option,but thats not an option as we use private cloud and use SAAS(Software as Service),they wont do anything software related at the back end.
In our previous Antiviruses,they always had a master wipe tool which would cleanup everything regardless of tamper protection on and off ,because in real world,clients get off sync all the time and I was wondering if anyone had success in uninstall without the safe mode option.
Any help will be appreciated ,I am on the verge of rebuilding our server out of sheer desperation.
This thread was automatically locked due to age.