Download and use the attached Python script to test IPS detections with the EAP client. If you haven't installed Python yet, you will need to download the installer for Windows from https://www.python.org.
Python test script
Endpoint-Sophos-IPS-Tester.zip
Testing outbound malicious traffic
Start the script without arguments, for example by entering the following in a command prompt:
python c:\SophosIPS\endpoint-ips-tester.py
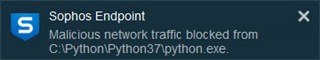
This will send out the test string to ipstest.sophostest.com:54445. Sophos Endpoint devices that have IPS will block this traffic, and detect a threat.
The endpoint will throw a message showing that malicious traffic has been blocked:
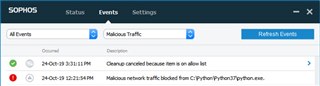
The endpoint application will show some more details:
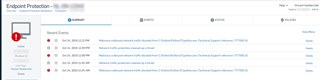
You'll find more details in Sophos Central:
The python script interpreter is the application responsible for the outgoing malicious traffic. However, as python.exe is not malicious on its own, it won’t be cleaned up.
Testing cleanup
You can test cleanup by compiling the script into an executable, using pyinstaller (https://www.pyinstaller.org/). The executable you create will not be whitelisted, and thus will get cleaned up.
Testing inbound malicious traffic
To see what happens when inbound malicious traffic is intercepted, run the script on one machine with the --server argument. If it takes the wrong network address, add the –a option to specify the correct address on which to listen to.
python endpoint-ips-tester.py -a 172.19.3.10 -s
On another machine run the script to send a tcp test package to the machine that is listening. For example:
python endpoint-ips-tester.py -a 172.19.3.10 -t tcp
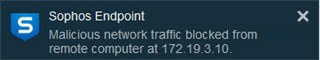
This will result in a detection of incoming malicious traffic on the first machine. The traffic will be blocked.
Of course no cleanup can be performed here, as the application responsible for the traffic is not on the machine with the inbound traffic.