Hi,
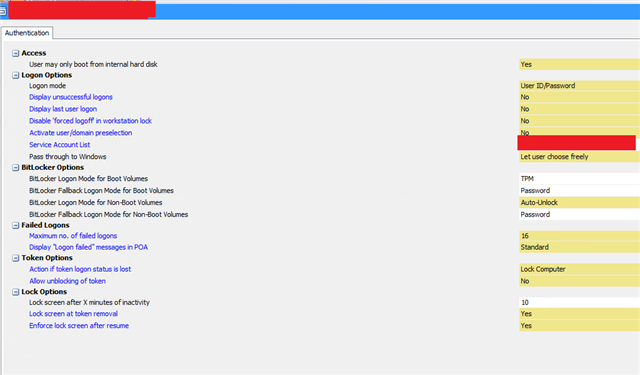
We are currently looking into setting up GPO for Windows Updates, as the feature updates require multiple reboots, every reboot will require the enter of the Bitlocker PIN.
Is there a way to suspend Bitlocker so this can happen? Not sure if it can be link to our GPO?
Kind regards, Dan
This thread was automatically locked due to age.